Understanding how Gen-AI models, particularly large language models (LLMs), learn requires examining their behavior both during training and after training is complete. During this process, loss functions play a central role by showing how far the model’s predictions are from the correct outputs. A lower loss generally means the model is making better predictions, while a higher loss indicates more mistakes. Tracking this value over time helps us understand whether the model is actually learning or struggling. These metrics provide a clearer picture of how well the model generalizes to new, unseen data, beyond the training set.
Modern cyber defense increasingly relies on AI systems that analyse vast amounts of threat intelligence and identify patterns beyond traditional analytical reach. As these models grow more powerful, they also become harder to understand raising concerns about transparency and reliability. This post walks through the role of explainable AI in strengthening cyber attribution, outlining how GNN- and LLM-based techniques can clarify model reasoning and support operational decision-making, and highlight what security teams need to consider when integrating XAI into real-world workflows.
Advanced Persistent Threats (APTs) are long‑term, highly sophisticated attacks carried out by well‑resourced or state‑sponsored actors who infiltrate networks, evade detection for months, and target high‑value information. Traditional signature‑based cybersecurity tools can no longer keep up with these stealthy campaigns, making attribution far more complex and reliant on behavioral and intelligence‑driven methods. In this blog, we explore how AI—particularly Deep Reinforcement Learning, Federated Learning, and Explainable AI—is transforming APT attribution from a manual, reactive process into an automated and adaptive capability.
This blog post explores the integration and impact of Artificial Intelligence and Machine Learning (AI/ML) on security in wireless communications—particularly within 5G, 6G, and beyond. While the broader context includes security within the 6G architecture and emerging 6G technologies [1], this post specifically focuses on pre‑6G security.
As cybersecurity defenses evolve, so do the tactics of digital adversaries, shifting from simple detection scripts to sophisticated Environmental AI. This next generation of malware leverages lightweight machine-learning models to distinguish between a genuine user and a security sandbox by analyzing complex behavioral patterns like mouse entropy and system jitter. By embedding TinyML directly into malicious binaries, attackers can now outwit traditional virtualization detection, remaining dormant until they are certain of a high-value target.
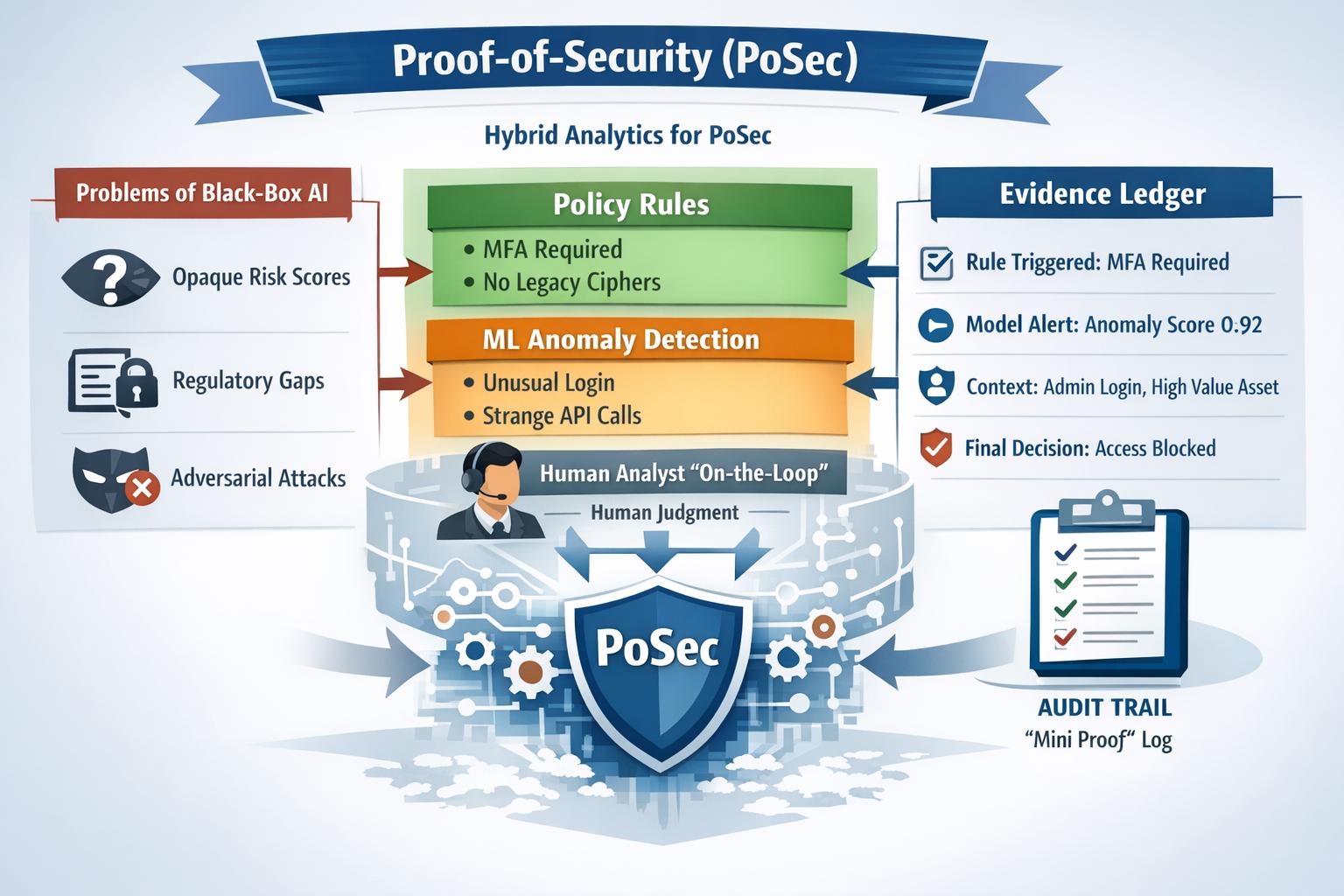
Proof-of-Security (PoSec) reframes “AI for cyber defense” from chasing detection accuracy to producing decisions that can be explained and audited. It argues black-box models fail in practice because they obscure risk posture, create compliance gaps (e.g., traceability expectations in NIST guidance), and remain fragile to adversarial manipulation especially as attackers weaponize AI. PoSec instead uses hybrid analytics (deterministic policy rules + ML anomaly detectors + humans on-the-loop) where combination logic is explicit and rules can dominate high-severity cases. An evidence ledger then logs which rules/models fired, key context, and the final action, turning each alert into a reconstructable “mini proof” suitable for operations and audits.
As organizations increasingly integrate AI into complex digital environments, understanding its governance implications has become essential. This blog post highlights why strong governance is critical for securing intelligent systems and ensuring responsible deployment across mission‑critical contexts. It also outlines the key considerations that guide trustworthy, transparent, and accountable AI practices while framing the broader relationship between AI governance and cybersecurity, including the risks, frameworks, and standards shaping secure and responsible AI use.
As Large Language Models (LLMs) become core to modern Artificial Intelligence (AI) systems, they also open new attack surfaces. This post explores how AI red-teaming—the practice of probing models like GPT for weaknesses—helps uncover biases, data leaks, and prompt-based exploits before they cause harm. From prompt injections to automated adversarial pipelines, discover how researchers are reshaping cybersecurity for the era of intelligent systems.
Quantum computing is no longer a distant concept. As it moves from theory to real-world application, it introduces a new set of security risks for digital systems. The cryptographic algorithms that currently protect financial transactions, communications, and data exchanges may not be strong enough to withstand quantum-based attacks. Assessing Post-Quantum (PQ) security has become a critical step in preparing organizations for this transition. When combined with Artificial Intelligence (AI), PQ security assessment provides a structured, data-driven approach to evaluate risks, identify vulnerabilities, and guide secure migration strategies. This article explores how Post-Quantum Cryptography (PQC) and AI work together to help organizations strengthen and future-proof their cryptographic infrastructure.
In the high risk setting of malware detection, transparency and explainability are critical components of trustworthy prediction making. However, for deep learning-based detection methods such transparency is often hindered by model complexity. In this blog post, we explore the application of Graph Neural Networks in malware detection and focus on their unique explanatory capabilities.
QR codes are now widely used in emails, payments, and advertisements, but they have also become a powerful tool for cybercriminals. Quishing, or QR code phishing, embeds malicious URLs in QR codes to trick recipients into scanning them, thereby bypassing traditional email security controls. This article explains how quishing attacks work and presents an AI-driven detection pipeline that analyzes QR codes and their destination URLs using lightweight transformer models. It also discusses practical deployment strategies for enterprise and endpoint protection.
Testing how strong encryption really is is essential for security. Even when systems come with formal mathematical proofs, weak designs or misuse can still leak information. Machine learning is now used as a practical tool to automatically spot patterns and weaknesses. It does not replace mathematical proofs, but it helps confirm which systems are insecure and which ones remain strong in real-world testing.
A penetration tester sits surrounded by multiple monitors, analyzing thousands of lines of code, network maps, and vulnerability scan results. The goal is to find the critical flaws before a real attacker does. This scene is familiar to any security professional. It is a labor heavy process of pattern recognition, creative thinking, and relentless curiosity. But now, a powerful new partner is joining the red team: Artificial Intelligence.
If you work in incident response or threat intelligence, you have probably felt the firehose. Alerts, logs, takedown notices, paste sites then someone asks, “Who did this?” Large Language Models (LLMs) promise relief: they read fast, summarize well, and speak fluent acronym. But attribution is not just reading; it is judgment under uncertainty. Used wisely, LLMs accelerate that judgment. Used carelessly, they accelerate misattribution.
This post walks through how LLMs really change attribution what they are great at, where they can hurt you, and a pragmatic checklist to keep your conclusions defensible.
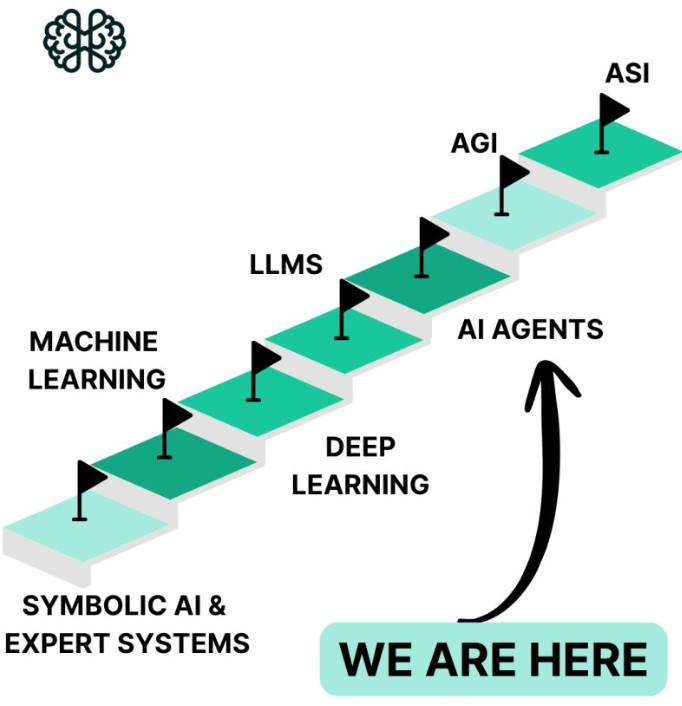
Artificial Intelligence (AI) has entered a new era. For decades, AI was about symbolic systems, machine learning, and deep learning models that learned patterns from data. Then came large language models (LLMs), which made it possible for machines to understand and generate human language on a scale. Now we are stepping into the age of AI agents, autonomous, proactive systems that don’t just respond to prompts but can interact with tools, environments, and even other AI agents GenAI Works [1].
Artificial Intelligence (AI) systems, particularly those leveraging machine learning (ML) and large language models (LLMs), face a distinct set of security challenges. These technologies often operate on vast datasets and complex algorithms, making them susceptible to different attacks. As AI becomes increasingly integrated into critical infrastructure and decision-making processes, ensuring its resilience against emerging threats is essential for maintaining trust and operational integrity.
Cryptography has always been a game between code makers and code breakers. But the code makers just got a boost. Modern Artificial Intelligence (AI) systems can now reduce the number of possible messages before traditional cryptanalysis starts. This brings a significant change in the security model.
In today's digital landscape, cyber threats are becoming more advanced, rendering traditional security models inadequate for safeguarding sensitive data and digital infrastructure. Organizations can no longer depend on perimeter-based security measures that presume trust within the network [1]. Enter Zero Trust Architecture (ZTA)—a groundbreaking security framework that eradicates implicit trust and mandates continuous verification at every point of network access.
With the advancement of technology and the increasing use of digital assets in IT environments, security concerns have risen. These concerns can be associated with various parts of an IT environment. However, there are always areas within a firm’s IT infrastructure and systems that are either unmonitored or not adequately monitored. Additionally, an area that was once a concern and later resolved may become a threat again due to emerging security risks, yet it may go unnoticed. These unattended security threats within an organization are known as "Cyberspace Blind Spots"
Quantum malware represents a futuristic cybersecurity threat that exploits the unique capabilities of quantum computing, such as qubits and superposition. In contrast to traditional malware, it targets vulnerabilities in quantum systems and conventional encryption methods (e.g., RSA2048). It operates as a "time capsule" threat—lying dormant until quantum computers can decrypt data secured by today’s standards, posing significant long-term risks to sensitive information [1][2].
Side-channel attacks (SCAs) exploit indirect information such as timing variations, power consumption, or electromagnetic emissions to extract sensitive data from hardware and software systems. In contrast to traditional attacks targeting coding flaws, SCAs take advantage of physical characteristics, making them particularly insidious.
The cybersecurity landscape is rapidly evolving, with cybercriminals employing increasingly sophisticated techniques to breach systems and exploit vulnerabilities. From AI-powered phishing to ransomware-as-a-service (RaaS), modern threats demand advanced defensive mechanisms. One promising technology that enhances cybersecurity strategies is Retrieval-Augmented Generation (RAG). By combining the strengths of large language models (LLMs) with real-time data retrieval, RAG offers a proactive approach to threat detection and mitigation.
The rapid growth of Internet of Things (IoT) devices is transforming various aspects of daily life, including smart homes, healthcare, industrial automation, and critical infrastructure. These devices, which originate from diverse environments, are built by different vendors and designed for distinct purposes, creating a highly heterogeneous IoT ecosystem. However, from a network security perspective, this diversity presents significant challenges in accurately identifying and verifying the sources of communication between devices and servers.
In our hyperconnected digital environment, cybersecurity threats evolve rapidly. While technical defences (e.g., firewalls, encryption) are important, human behaviour remains a critical and often vulnerable component. The persuasive design addresses this challenge by guiding and motivating secure behaviours rather than relying solely on fear or mandatory policies.
The rapid advancement of the Internet of Medical Things (IoMT) is transforming the healthcare industry. IoMT devices, such as smart wearables, remote monitoring systems, and implantable devices, are improving patient outcomes and reducing healthcare costs. However, as these devices become more interconnected, they also introduce significant cybersecurity risks. Ensuring the security of IoMT has become a critical priority as the consequences of breaches could lead to compromised patient safety, data privacy violations, and severe financial losses.
Advancements in quantum computing are transforming cybersecurity, exposing vulnerabilities in current cryptographic systems. Quantum algorithms such as Shor's can break RSA (Rivest–Shamir–Adleman) and ECC (Elliptic curve cryptography), while Grover's weakens AES (Advanced Encryption Standard). To address these threats, the National Institute of Standards and Technology (NIST) is developing Post-Quantum Cryptography (PQC) standards. Additionally, risk assessment frameworks such as STRIDE help identify and mitigate vulnerabilities in cryptographic systems. This article explores the algorithmic-level risk assessment of these vulnerabilities, aligns them with the NIST Cybersecurity Framework (NIST CSF) and STRIDE model, and discusses mitigation strategies, including the migration to quantum-safe cryptography to ensure future-proof systems.
As Electric Vehicles (EVs) and their charging infrastructure rapidly expand worldwide, they are becoming prime targets for cyber threats. This blog explores critical vulnerabilities in EV charging systems, including session hijacking, remote discharging, relay attacks, and electromagnetic eavesdropping, which pose serious risks to both vehicle owners and power grids. Discover how these cyber risks impact grid stability, safety, and the future of secure transportation.
In the world of cybersecurity, staying ahead of vulnerabilities is a constant challenge. Automatic Exploit Generation (AEG) is an innovative technology that automates the discovery of software vulnerabilities and the creation of exploits to demonstrate their impact. In this blog post, we will explore what AEG is, how it works, the tools behind it, and the challenges that remain in perfecting this technology.
Ransomware-as-a-Service (RaaS) is a cybercrime model that enables individuals with little or no technical expertise to carry out ransomware attacks. It operates as a business model in which cybercriminals develop ransomware and offer it to affiliates in exchange for a share of the profits. This has resulted in a rise in ransomware attacks, impacting businesses, government institutions, and individuals globally. RaaS has significantly lowered the barriers to entry for cybercrime, making it easier for less-experienced attackers to engage in complex cyber extortion schemes.
Threshold cryptography is a powerful technique that enhances security, fault tolerance, and privacy by distributing cryptographic operations among multiple participants. Unlike traditional cryptographic systems that depend on a single key holder, threshold cryptography divides a cryptographic key into several shares, requiring a subset of those shares to perform operations such as decryption or signing. This approach not only secures sensitive operations but also reduces single points of failure.
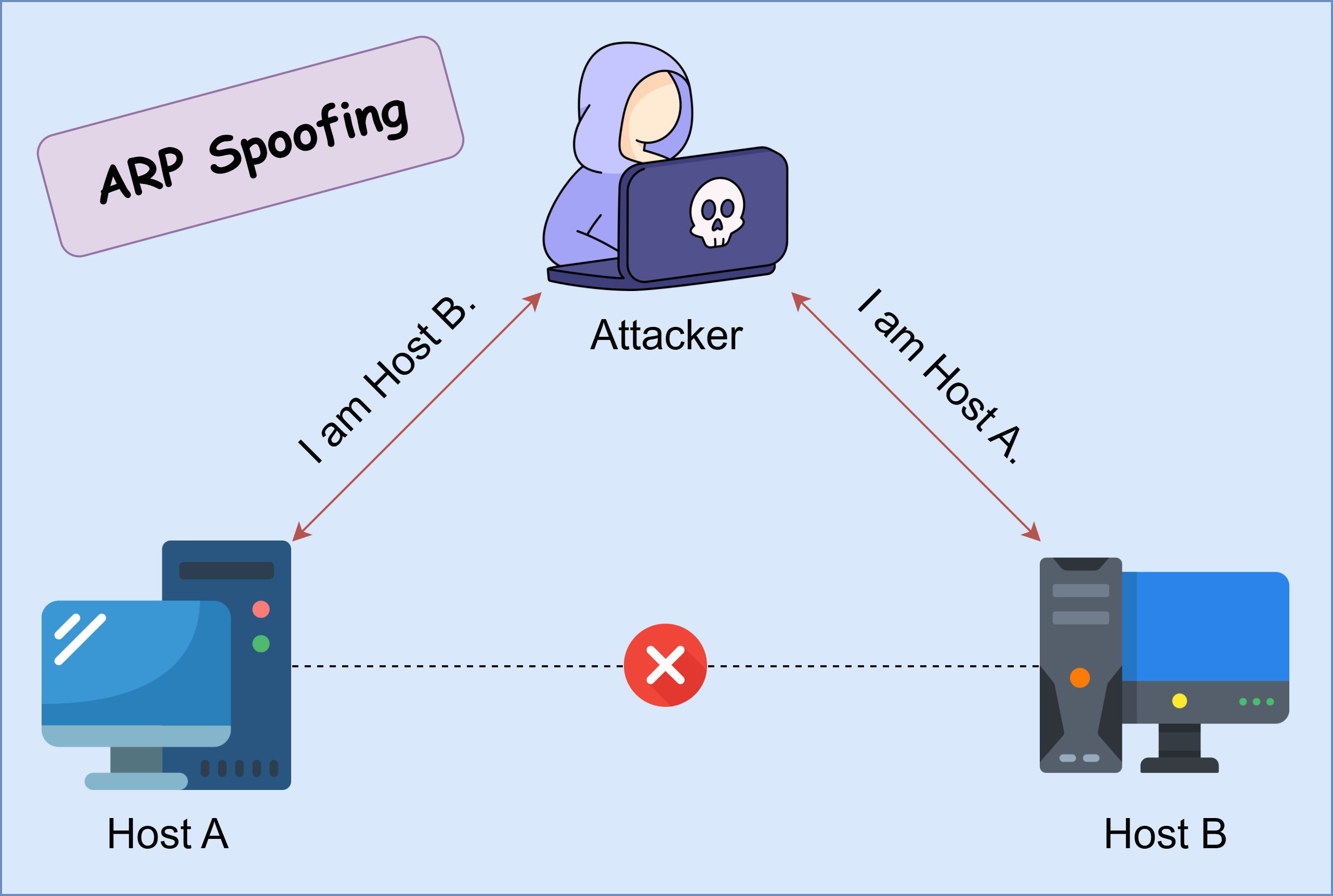
Ever wondered how an attacker can secretly eavesdrop on network traffic or even manipulate data without anyone noticing? One of the sneakiest ways to do this is through ARP spoofing. The Address Resolution Protocol (ARP) is what helps devices in a local network find each other, but here’s the catch—it wasn’t built with security in mind. That means a hacker can easily trick devices into sending their data to the wrong place, setting the stage for a man-in-the-middle (MITM) attack. In this post, we’ll break down the ARP protocol, how it works and how it can be manipulated to conduct MITM attacks.
Recently, a new scam has been identified in which attackers exploit web users' tendency to click through CAPTCHA tests quickly, to bypass verification tools without checking them thoroughly. This method primarily targets individuals through online advertisements, file-sharing services, betting platforms, anime websites, and web applications that generate revenue from traffic. CAPTCHA tests, which are routine and often boring, cause users to mindlessly click through them, making them vulnerable to this type of scams. Security experts have discovered hackers using fake CAPTCHA tests that install malware on Windows PCs when users follow the instructions.
Reverse engineering is a crucial process in cybersecurity, malware analysis, and software security research, and IDA Pro stands as one of the most powerful tools in this domain. This blog post provides an in-depth look at IDA Pro, the industry-standard disassembler and debugger developed by Hex-Rays, highlighting its key features, capabilities, and why it remains a preferred choice among security researchers and analysts. From its advanced disassembly and debugging functions to graph visualization, cross-referencing, and scripting support, we will explore how IDA Pro helps in understanding complex binaries.
The Advanced Encryption Standard (AES) is a widely adopted encryption algorithm, with hardware acceleration playing a critical role in improving its performance and security. While AES can be implemented in software, many CPU manufacturers provide hardware acceleration instructions to maximize the performances and to minimize the power consumption. This blog post analyzes AES acceleration support in four major CPU architectures: Intel, AMD, ARM, and RISC-V.
As organizations increasingly migrate their operations to the cloud, ensuring robust cybersecurity has become a top priority. The cloud offers unparalleled scalability, flexibility, and cost-efficiency, but it also introduces new cyber risks and challenges. To mitigate these cyber risks, organizations must adhere to established cybersecurity standards and frameworks during their cloud migration journey. A cybersecurity standard or framework is a set of guidelines, best practices, and requirements designed to help organizations protect their information systems and data from cyber threats.
Large-scale cyberattacks are not random acts of chaos but carefully orchestrated operations designed to exploit vulnerabilities, steal data, or disrupt operations. From reconnaissance to execution, attackers follow a systematic approach to maximize their success. This blog post delves into the step-by-step process of a large-scale attack, the considerations attackers make, and the lessons organizations can learn to prevent such incidents. All insights are backed by evidence and real-world examples.
Public Key Infrastructure (PKI) is a cornerstone of modern cybersecurity, enabling secure data encryption, certificate management, and digital communication. Hardware Security Modules (HSMs) protect cryptographic keys within tamper-resistant environments, ensuring their security against theft and misuse. This article explores the vital role HSMs play in strengthening PKI and fostering safer online transactions.
Cyber attacks are unavoidable. In today's interconnected world, operational technology (OT) systems are increasingly targeted by cyber adversaries. OT consists of hardware and software that control and monitor physical processes in industries like manufacturing, energy, and water treatment. Understanding the nature of these attacks, especially through frameworks like the Purdue Model, is essential for industry professionals aiming to bolster their defenses.
The integration of Artificial Intelligence (AI) in cybersecurity has transformed the way organizations detect, prevent, and respond to cyber threats. As cyberattacks become more sophisticated, traditional security measures are proving insufficient. AI offers the potential to not only enhance threat detection but also automate responses, making it a double-edged sword in the cybersecurity landscape.
As Large Language Models (LLMs) like ChatGPT, Bard, and Claude become increasingly powerful, they’re making a significant impact on cybersecurity—but their influence cuts both ways. These advanced AI tools can act as invaluable assets to cybersecurity professionals, helping to detect cyber threats and automate responses. However, they also introduce vulnerabilities, creating opportunities for attackers to exploit LLM capabilities for harmful purposes.
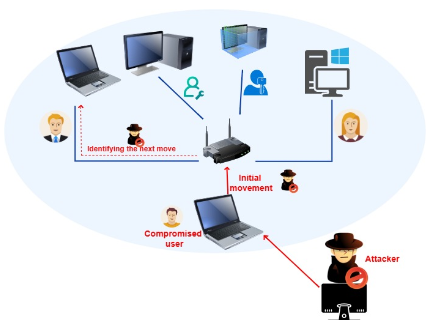
Discover how graph learning revolutionizes lateral movement detection by modeling network relationships and training machine learning classifiers to distinguish malicious activity from legitimate paths, enhancing cybersecurity defenses against advanced threats.
This blog highlights the cybersecurity risks of Distributed Energy Resources (DER) like wind and solar power. It discusses vulnerabilities in communication networks, focusing on a data integrity attack targeting offshore wind farms, which can destabilize grids and cause economic losses. The blog emphasizes the urgent need for enhanced security in DER systems to protect modern energy infrastructure.
This blog explores the CrossBarking exploit, a newly discovered attack targeting Opera's private APIs. It delves into how attackers use malicious Chrome extensions to inject harmful scripts, manipulate browser settings, and pair the exploit with XSS attacks for greater impact. Defensive measures, including stricter API permissions and enhanced extension vetting, are also discussed to help mitigate such threats.
This blog explores the evolving landscape of cryptography, comparing traditional libraries like OpenSSL and libsodium with emerging quantum-resistant solutions such as CRYSTALS-Kyber and PQClean. It highlights their features, performance, and security to help developers navigate immediate and future data protection needs in an era of advancing quantum computing.
The blog highlights the growing quantum computing threat to traditional encryption, the importance of cryptographic agility, and the adoption of hybrid approaches. It explores NIST standards, quantum-safe strategies, and practical steps to secure digital assets for the future.
The blog introduces honeypots—decoy systems used in cybersecurity to lure attackers and gather threat intelligence. It explains their role in identifying attack patterns, tools, and vulnerabilities, while protecting real systems. A step-by-step guide to setting up a honeypot with tools like Cowrie, VirtualBox, and Kali Linux is provided, along with tips for further exploration.
Quantum computing is no longer just a thing of sci-fi movies or distant tech dreams. It’s becoming real—fast! And while that’s super exciting for fields like science and medicine, it’s a bit of a nightmare for cybersecurity. Quantum computers will be so powerful that they’ll be able to crack the encryption we rely on today, which means everything from online banking to secure communication could be at risk. But don’t panic! This is where post-quantum cryptography (PQC) comes in, and the process of shifting to quantum-safe encryption is called post-quantum migration. Let’s break down what it is, why you should care, and what needs to happen to keep our digital world safe.
Modern CPUs integrate various advanced architectures and features to maximize performance and efficiency, but these advancements also introduce potential security vulnerabilities. Two major vulnerabilities recently discovered in Intel and AMD CPUs are Intel's RAPL interface vulnerability and AMD's Sinkclose vulnerability. Both vulnerabilities pose risks of sensitive data being extracted by attackers.
Graph Neural Networks (GNNs) have emerged as a cutting-edge tool in malware detection, offering a more robust approach than traditional techniques such as random walks or factorization.
A routine update gone wrong – CrowdStrike’s Falcon platform update triggered widespread system crashes and business disruptions.
Cyberbullying on social media is a growing crisis that significantly impacts teens' mental health, leaving many feeling isolated and distressed. Addressing this issue calls for a proactive, empathetic approach that encourages positive online interactions and builds safer digital environments for young people.
The use of recent disruptive technologies such as blockchain networks, cloud computing infrastructure and machine learning has made the supply chains more effective and efficient, but exposed them to different cyber vulnerabilities. Securing modern supply chains has become an essential, but a complicated task, with attacks such as SolarWinds.
Malware packers obscure malicious code, helping it evade detection by compressing or encrypting files. This blog covers types of packers, their uses, and effective methods for identifying and unpacking hidden threats.
This blog discusses SecOps, what it represents and its benefits.
In his post, most important security mechanisms deployed in android platform is described.
The blog discusses the definition of phishing and the most popular three sophisticated phishing attacks.
Which one do you prefer, traditional or electronic voting? If your preference is the latter one, read this post to know the requirements and potential threats of electronic voting.
Is ”a bunch of IOCs named for marketing” a CTI? or ”we did an IR response against a top tier APT, here are the only things the lawyer will let us say” a CTI? or ”this is a new threat; we have some generic and entirely impractical mitigation advice” a CTI? Or all of them plus many other definitions of CTI construct CTI? Is CTI a mythical animal like Pegasus, i.e., a horse with wings?
This blog will briefly discuss about CTI and how today’s CTI is still evolving. Why it is good or not to share CTI and why systems thinking is very important to Cyber Security and CTI is a good helper to achieve this. Hopefully, someday we can say that CTI can help us going far together in Cyber Security.
This post highlights the increase in cyber-attacks in the past few years. It discusses the various ways and strategies followed by malicious attackers to take control over the system. Also exposing that due to COVID19-pandemic, how everything has changed with number of attacks increased many-fold due to work from home facility. In addition, Internet-of-Things (IoT) devices have made it more critical for cybersecurity providers to secure IoT environments.
Hey! Are you using social media (Twitter, Facebook, Instagram, YouTube)? Are you aware of cyberattacks (data breach, phishing, SIM swap, disinformation) on social media and their impact? If not, this blog makes you aware of these attacks. This blog provides an overview of the rising cyberattacks on/via social media and their impacts.
This post is for companies who are dealing with the personal data of users for business purposes. As we know, data has become an integral part of almost every industry, such as social media, healthcare, e-commerce, and government. With the advancements in digital technology and the proliferation of online services, data is growing at a tremendous pace.
Are you struggling to keep up the security pace of your organization? If so, this article is for you! In today's era of rising global cybersecurity threats, Social engineering tests can prove beneficial for companies to stress-test their weakest links and resolve any underlying issues to avoid security breaches. One of the practical techniques is penetration testing (also known as "pen testing").
Unlike humans, deep supervised algorithms and machine learning techniques require several objects to learn. A child usually needs to perceive just a few examples of an object or even only one before recognizing it for life. By displaying photos of a horse and eagle and telling the child there is a magical creature in between called a unicorn, they can recognize it anywhere they see it. The question is, how can we program AI to be the same? A couple of MIT researchers proposed a distillation technique that synthesizes a small number of data points that do not need to come from the correct data distribution. Their experimental result illustrated that their model could compress 60,000 MNIST training images into only 10 images (one per class).
"mizaru, kikazaru, iwazaru" (see not, hear not, speak not). What can we learn from "see no evil, hear no evil, speak no evil" in the realm of cyber security? In cyber security we do need to see evil, to hear evil, and to speak about evil which can be facilitated by an approach coined as Situation awareness (SA). In SA, we "see and hear" the environment within a context of time and space, then we "speak" about their meaning and the projection in the future. Therefore, systems thinking is very important in cyber security. This blog will discuss how today's endpoint security, network security, threat information sharing, orchestration, and automation of cyber security are still evolving. By considering the current situation, it is good enough for us to say that cyber security is indeed a shared responsibility. It is indeed a "We" in wellness not an "I" in illness.
Crime detection using Artificial Intelligence (AI) approaches, especially Machine Learning (ML) techniques have attracted a lot of attention in both academic research and industry practices. However, the inability of humans to understand how some of these models arrive at their decision is raising a lot of ethical issues. In addition, data protection laws such as the General Data Protection Regulation (GDPR) has empowered data subjects to be entitled to an explanation of automated decisions impacting them and the right to challenge such decisions. Thanks to Explainable AI, an active area of research aimed at ensuring transparency in the use of AI and ML. This article explores the potentials and biases of AI and ML and highlights interpretability methods and libraries that can be leveraged in rooting out inequality in the application of automated decision-making in risk profiling and behavioral analytics as it relates to criminal justice and financial crime prediction.
The research community from different disciplines is studying the dissemination, detection, and mitigation of fake news, however, it remains challenging to detect and prevent the dissemination of fake news in practice. In this blog, we will share few useful tips that can help in identifying fake news articles.
If you are searching the term “artificial intelligence” on Google or you ended up on this particular blog, or commuted to work using Amazon, yes you made use of Artificial Intelligence.
As with all networked computing devices, increased connectivity often results in a heightened risk of a cybersecurity attack. Vehicles are currently being developed and sold with increasing levels of connectivity and automation. After all, people’s lives depend on the proper functioning of the system[1].
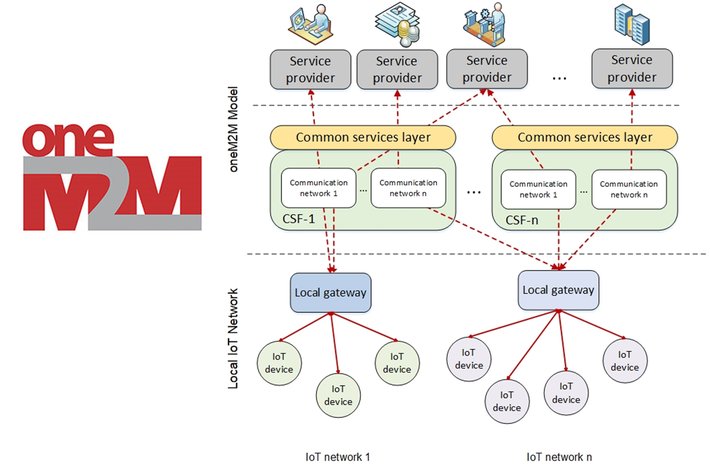
Due to IoT ecosystem's complexity, no single technology can deliver a complete IoT solution on its own. From connectivity, sensors, and gateways to the cloud and application systems, an IoT architecture is composed of various components working in concert with each other. As a global partnership project, oneM2M develops standard specifications that cover requirements, architecture, security solutions, and interoperability for machine-to-machine (M2M) and IoT technologies. oneM2M is a service layer platform to support end-to-end IoT services including M2M communications by developing technical specifications. In this blog, we introduce oneM2M and its service layer functions.
Abstract- The MITRE ATT&CK framework is a comprehensive matrix of tactics and techniques used by adversaries to compromise information technology (IT) and operational technology (OT) systems. This framework is used by security engineers to develop analytics to detect possible adversary behaviors. ATT&CK became the practical tool both for the adversary emulation team to plan events and for the detection team to verify their progress. In this blog, brief descriptions of the adversarial tactics used by malicious cyber actors in the IT and OT systems are provided.
The goal of Distributed Denial of Service (DDoS) attacks is to disrupt the normal traffic of a target network/server by overloading the target with a large volume of malicious traffic. In this blog, we provide descriptions of a wide variety of DDoS attacks categorized into two broad groups of reflection-based and exploitation-based attacks.
With the increase usage of smartphones, stalkers found new way to abuse their victims by stealing their online freedom. Usually, this is done by stalkerware apps which are a growing concern in domestic violence. In the recent past, these apps have come with disturbing and dangerous implications as they easily installed without victim's knowledge.
The static nature of the existing state-of-the-art computing systems provides asymmetric advantages to attackers that make them easy for reconnaissance, plan and launch attacks. The concept of Moving Target Defense (MTD) is to dynamically change the attack surface to increase uncertainty and confuse the attackers by invalidating their intelligence collected during the reconnaissance and it significantly reduces the attack success.
This blog describes how digital forensic techniques and tools enable defenders to detect cyberattacks and identify defensive approaches to prevent the similar attacks in future.
Small-scale IT providers are a bit hesitant to be thorough on cybersecurity implementations due to cost. This blog provides a brief insight on what might happen consequently.
Organizations often outsource some of their services to third-party vendors for handling their business-critical data. With some of your most valuable data assets stored with third-party organizations, security becomes a major concern. As a service organization, you would want to know whether the security controls implemented are the best practices to safeguard your customer’s data. You would also want to ensure that your third-party vendor is Compliant with various industry standards. This is when a SOC1 Audit comes into the picture. SOC1 Audit plays a key role in ensuring whether or not a company is compliant with the set security standards and has in place necessary controls. This blog covers the top 5 reasons why a data center should consider or rather need a SOC1 Audit. But before delving in, let us first understand what a SOC1 Audit is.
As 5G standards continue to evolve, all relevant stakeholders including research institutions should be involved in the 5G technology rollout process and the 6G development initiative to ensure the security of billions of IoT devices and systems. This also applies to the development of emergent networks which will have big implications for government and industry solutions in terms of public safety and critical asset protection.