
Data Leakage in Mobile Apps
Data security can be defined as a list of protocols and techniques that preserve data from deliberate or unexpected damage, tampering or exposure. One of the massive issues in data security is data leakage, known as low and slow data stealing. This issue can be applied to any organization and even person, regardless of the size of organization or profession of the person.
If we want to define data leakage accurately, we can define it as an illegal electronic or physical spread of any kind of data that belongs to an organization or a person to an external target. It is one of the most disquieting threats to enterprise security in 2019. Its threats usually occur via the web, emails, and mobile data storage devices such as laptops and smartphones.
NowSecure, a mobile app security firm, states in its new research that millions of Android users could be at risk. They examined 250 of the most popular Android apps in different categories. These apps were classified in online retail, brick-and-mortar retail, finance, insurance and travel apps that all are available in the Google Play Store. The study showed that 70 percent of them leaked personal information that increased the risk of fraud and identity theft for their users. As Figure 1 shows, online and brick and mortar retail apps are the most vulnerable apps among other categories.
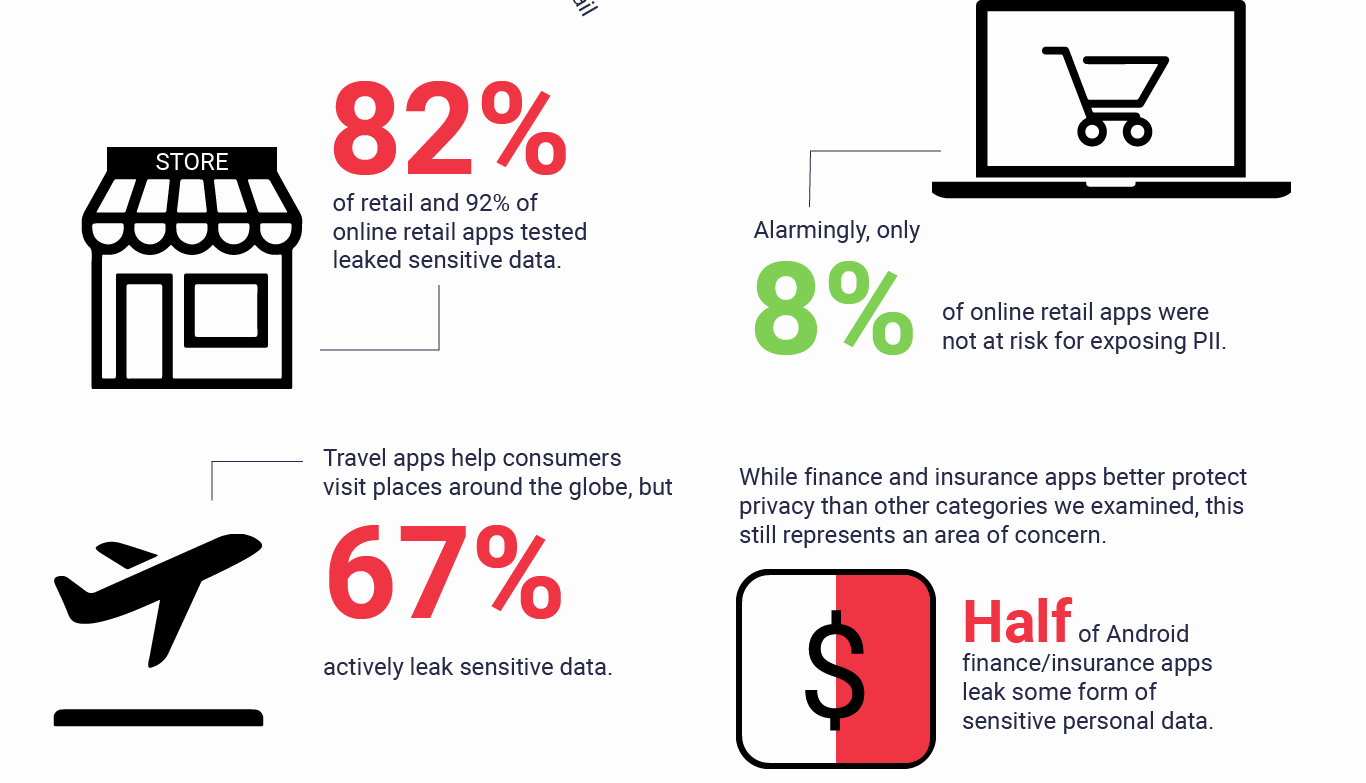
Figure 1. Vulnerable apps categories that leak personal information [NowSecure research].
The first effective way to prevent this kind of cybersecurity breach is to remove unusable apps and to update frequently used apps periodically to ensure that the last version of them is used. App Annie found that among the 60 to 90 apps installed on a person's phone, users only opened 9 of them daily. For a monthly period, this number would be 30 apps. It means that most of the installed apps were not even opened once over a long period of time. Nevertheless, these apps may have authorized access to personal information. So, the simplest way to protect personal data is to delete unused apps and ensure that apps used are kept up to date.
The second potent way is to limit browsing and be more cautious about the information that one shares and fills in on websites' forms because of phishing. It is strongly recommended to ensure that critical processes like online shopping and banking are done only on reliable devices and on secure and encrypted connections.
Users are still in danger if the app producers do not fulfill some preventative duties in their developing process. Some of these considerations that can prevent data leakage in the mobile app are listed below:
-
Android apps developers should use a set of Android data encryption tools such as KeyStore. Since data processing enables the availability of data and faster processing, it is a crucial and sensitive part of the mobile phone application. Data processing needs to be secured because of containing confidential information. The sensitive data should be encrypted, and the developer needs encryption keys to cypher information and use it in the future. Many times, developers save the keys on the device. But if the hackers get access to the encrypted key, they can easily find the public key and decrypt the data.
-
The Android app developers must implement HTTPS to add a high amount of security to the data being transferred between users' phones and servers.
-
To avoid disclosing personal data, developers should use appropriate input types (like 'password' types). Auto-caching makes the user's experience comfortable and efficient. However, developers should be careful about the data that they put on the shared clipboard.
-
Ensure that the production version of the app does not use logs. Although logs are helpful for developers, they might contain sensitive information like passwords or access tokens stored on devices locally.
Wrapping up!
When discussing data leakage and security in a mobile app, it is not limited to the above points. But it is essential to stay updated with the latest security patches of tools and applications. It helps to build a safe environment in which all users are fulfilling their needs without any concerns. Also, it is crucial to keep a thread on the techniques used by hackers to compromise the security of apps to prevent malicious action.