
Keylogger: The ultimate hidden tool for monitoring your typing!
Keylogger:
Often referred to as keylogging or keyboard capturing using a software or hardware tool, keylogger record the keys struck on a keyboard in a hidden way so that a user using the keyboard is unaware that their typing is being recorded.
Keylogger History:
The first keylogger was discovered in the mid-1970s, developed by the Soviet Union to target hardware typewriters.
After the Internet invention in 1983, keyloggers’ development became much more sophisticated for hardware and software-based keyloggers. Recent software-based keyloggers are much more sophisticated and usually are bundled feature within a malware. On the other hand, hardware-based keyloggers went through several developments, such as support different keyboards and ports with many advanced features.
Keylogger Types:
-
Software-based keyloggers
Software-based keyloggers are programs coded in such a way to operate in computers. Interestingly, software-based keyloggers are used for benign and malicious activities. Malicious keyloggers are either created independently or as a bundled feature within a malware. Meanwhile, benign keyloggers are used legally by families and businesses to monitor computer and network usage without their users' knowledge.
API-based keyloggers are among the popular types of software-based keyloggers. It takes only a few lines of codes to create API-based keyloggers; such API calls are used like GetAsyncKeyState(), GetForegroundWindow() to capture keystrokes based on a timer interval in milliseconds.
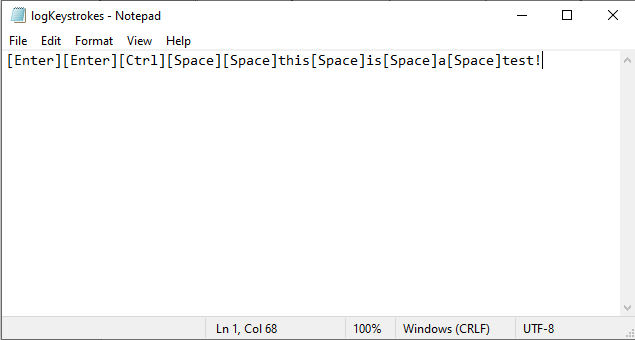
Another popular one is form grabbing or sniffing keyloggers; this sophisticated type has the intelligence to detect specific patterns of forms and inputs. For instance, a banking website or password protected textbox. This type is widely used in banking malware and Remote Administration Tools (RAT). The picture below demonstrates a software-based keylogger log file sample.
-
Hardware-based keyloggers
Hardware-based keylogger consists of a tiny memory chip planted in a device that can be roughly 4cm long. The hardware-based keylogger can be easily attached to a computer keyboard plug, making it much more stealthy than a software-based logger. The keystroke log is recorded in a small memory chip in the hardware keylogger that can be opened using specific computer programs that usually come with the hardware keylogger software’s collection. See the picture below for a hardware-based keylogger.

Hardware-based keyloggers are popular forensic tools. Besides their benign use, hardware-based keyloggers are also used maliciously by criminals and computer hackers for online piracy and computer hacking activities; however, they need to have physical access to the computer for exploitation in such cases.
Keylogger Countermeasures
We suggest the below countermeasures for avoiding a keylogger:
-
Using a virtual keyboard.
-
Using two-factor authentications (2FA).
-
Always have good Anti-Virus software installed in your system. Recommended and best anti-virus programs can be found here: https://www.av-test.org/en/.
-
Never clicking on untrusted links or execute untrusted software.
-
Keep your system updated to avoid zero-day vulnerabilities.