
Securing the Future Transportation: Unveiling Cyber Threats in Electric Vehicles (EVs) Charging Infrastructure
As Electric Vehicles (EVs) and their charging infrastructure rapidly expand worldwide, they are becoming prime targets for cyber threats. This blog explores critical vulnerabilities in EV charging systems, including session hijacking, remote discharging, relay attacks, and electromagnetic eavesdropping, which pose serious risks to both vehicle owners and power grids. Discover how these cyber risks impact grid stability, safety, and the future of secure transportation.
Modern Electric Vehicles (EVs) Charging
The modern world is contemplating Electric Vehicles (EVs) as one of the most promising solutions to confront accelerating air pollution. Recent forecasting of future greenhouse gas emissions indicates that the transportation sector is responsible for 16.2% of global greenhouse gas (GHG) emissions [1]. The primary contributor to these emissions in the transport sector is the combustion of fossil fuels for road vehicles. In response, researchers, policymakers, and governments are devising national strategies aimed at zero-emission transportation. Norway as the world's electric car capital, has introduced the Norwegian EVs policy with the ambitious goal of transitioning 100% of vehicles to zero-emission (electric or hydrogen) by 2025 [2]. In December 2022, Canada announced plans to boost the availability of EVs, targeting a 60% share of EVs in the total vehicles by 2030 [3]. Consequently, the number of EVs on the road is expected to surge significantly in the near future.
Growth of EVs:
To support this rapid growth in EVs, extensive investments in Electric Vehicle Charging Infrastructure (EVCI) are accommodated worldwide. Besides the advancements in EVs technology, an effective charging infrastructure is crucial for facilitating the widespread adoption of EVs [4]. Conductive EVs charging, which involves the physical transfer of electrical energy through conductive connections, is the widely used method of charging around the globe. This process requires a charging cable to connect physically to the charging station through the vehicle’s charging port [5], [6]. Global statistics reveal that, in 2021, there were 1.8 million publicly accessible fast chargers globally, marking a 37% increase from the previous year, despite pandemic-related disruptions. Additionally, the installation of public slow chargers showed an average growth rate of over 60% between 2015 and (Figure 1) 2020 [7]. The expansion of charging infrastructure is illustrated in Figure 1.
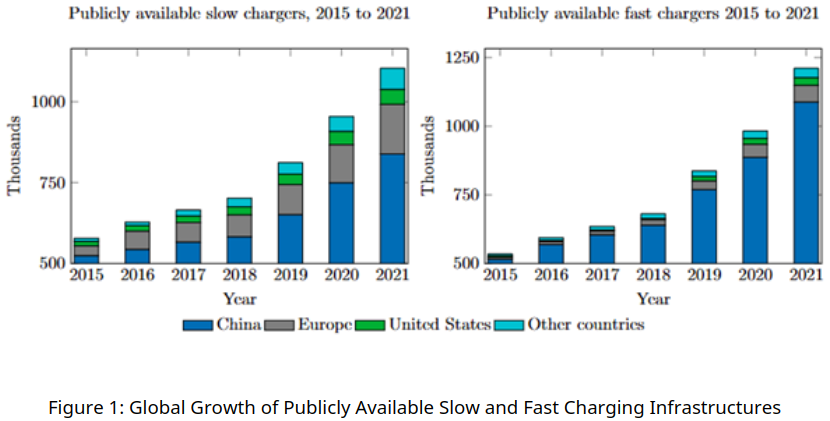
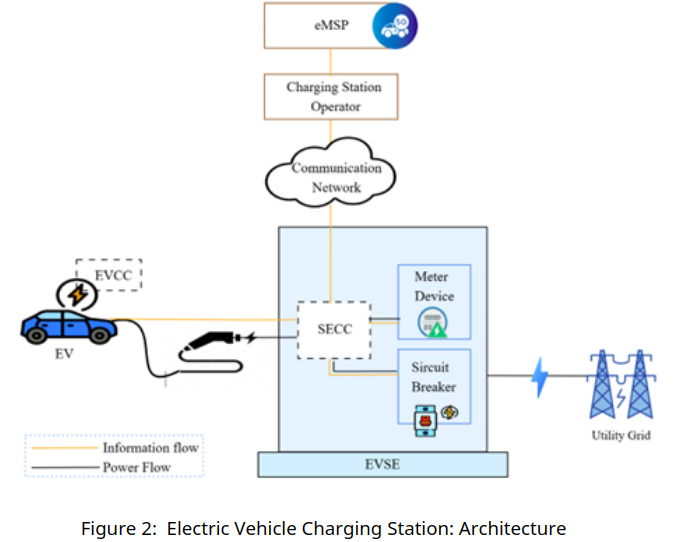
Figure 2 illustrates the system model of an EVs charging station. Each component plays a role in the process of charging an EVs and facilitating the flow of information and power:
-
Electric Vehicle (EV): The EV is connected to the charging station to receive power for recharging its battery. It is equipped with an EVCC (Electric Vehicle Communication Controller), which manages communication between the EV and the charging station.
-
Electric Vehicle Communication Controller (EVCC): This component is responsible for handling all communication between the EV and the charging infrastructure, specifically with the SECC (Supply Equipment Communication Controller). It ensures the proper exchange of data, such as charging status and payment information.
-
Supply Equipment Communication Controller (SECC): The SECC manages communication between the EVCC and the rest of the charging station infrastructure. It is the central unit responsible for overseeing the charging session, relaying messages between the vehicle and the charging station's internal systems and ensuring proper execution of the charging protocol.
-
Electric Vehicle Supply Equipment (EVSE): The EVSE includes the physical charging station components that supply power to the EV. It includes the Circuit Breaker for safety and power management and the meter device that measures the amount of energy transferred during the charging session.
-
Charging Station Operator: This entity manages the day-to-day operations of the charging station, including maintenance, monitoring, and ensuring efficient operation. It communicates with both the SECC and the eMSP via the communication network.
-
eMSP (Electric Mobility Service Provider): The eMSP oversees the customer-facing aspects of the charging, including managing user accounts, billing, and payment. It provides the interface between the EV owner and the charging infrastructure.
How Can Cyberattacks Exploit EVs Charging Vulnerabilities?
The main focus of this blog post is to discuss some attacks targeting EVs charging systems and exploited vulnerabilities. In addition to traditional cyberattacks, attackers may exploit communication vulnerabilities between EVs, charging stations, and the grid, leading to unauthorized access, data breaches, and potentially large-scale manipulation of charging networks. As the adoption of EVs and charging stations increases, understanding these attacks is critical for developing robust security measures to protect the charging infrastructure and ensure the safe and reliable operation of EVs charging systems [8].
Series of attacks on EVs charging systems – Concordia University study
Concordia University researchers recently conducted a study to investigate the security of EVs charging mobile apps as an attack surface against the power grid [9]. They have thoroughly studied the interactions of the different components and validated them on a real-time co-simulation test bed. Their findings evidence the design and implementation vulnerabilities of the EVs charging mobile application can be exploited to perform unauthorized operations on the connected EVs Charging Station (EVCS). The analysis identified several critical vulnerabilities within the EVs charging mobile app as follows:
-
Unverified Ownership: The system fails to verify if the user initiating the charging session is the actual owner of the vehicle. This opens up possibilities for unauthorized use.
-
Improper Authorization: The applications do not properly enforce authorisation for critical functions, allowing attackers to exploit these weaknesses to perform unauthorized actions such as starting or stopping charging sessions.
-
State Synchronization Issues: There are inconsistencies in maintaining the legitimate states (3-tuple states) across the Charge Management System (CMS), EVCS, and the mobile application. This inconsistency can be manipulated to hijack charging or discharging sessions.
-
Insecure QR Code Handling: Some applications store QR codes in temporary files on external storage, which can be accessed by an attacker to hijack charging sessions.
An attacker can exploit the above-mentioned vulnerabilities identified in the EVCS system to execute various malicious activities. To exploit these vulnerabilities, attackers need to control several adversarial accounts (ex: bots), which grant access to existing charging services via mobile applications. They can easily create their own network of legitimate mobile application accounts. The only security measures during account creation are SMS or email authentication/verification (ex: one-time passwords and email verification). In crafting the attack, an attacker can utilize the communication APIs to manage the verification process from online SMS and email providers, like Twilio [11]. In addition, attackers can generate fake email accounts as required for the verification steps. The set of attacks conducted is explained below.
Remote charging session hijacking:
As per the ideal specifications, CMS should only allow a charging request only if it is issued by the account holder who is bound with the EV. However, the existing CMS does not perform account-based authorization during the charging session. As the user is only linked with the EVCS ID, any EV connected to an EVCS can be charged remotely despite of whether the user who initiated the charging request is the legitimate owner of the EV. The CMS does not perform charging authorization to validate whether the user is allowed to perform this action or if the user is the actual owner of the EV. This weakness lets the adversarial accounts hijack charging sessions. Thus, an adversary can take control of an active charging session remotely. This is possible due to vulnerabilities in the state synchronization between the EVs charging mobile application, the EVCS, and the CMS. These components can be forced into unexpected states, allowing attackers to hijack charging sessions. For example, if the CMS and EVCSs are in a charging state while the mobile application is in the registration or discovery state, an attacker can exploit this misalignment to gain unauthorized control over the charging session.
Remote discharging attack:
Vehicle-to-grid (V2G) capabilities allow the EVs energy back to the power grid. EVs owners can register to sell energy back to the grid during peak hours by utilizing their mobile application. However, the current charging infrastructure does not have adequate authentication mechanisms. An adversary who hijacked the session as the above-mentioned attack can register themselves as a legitimate user to sell energy to the V2G scheme. This allows the adversary to gain more profit by discharging other users’ vehicles. This is a critical vulnerability as it can exhaust the EV’s battery. The attacker can exploit this by manipulating the communication protocols between the mobile application and the EVCS, initiating unauthorized discharging commands.
Above mentioned attacks have the following implications for the power grid:
-
Mass drop in load: Coordinated discharging attacks can cause a sudden drop in load, leading to underutilization of generation resources. This can destabilize the grid, as the power generation has to be quickly adjusted to match the reduced demand, potentially leading to operational inefficiencies and financial losses for power utilities.
-
Overloading and tripping transmission lines: Targeted attacks exploiting knowledge of the grid topology can overload specific transmission lines, causing them to circuit break. This not only disrupts the power supply but can also cause cascading failures in the grid, leading to widespread outages. An adversary with knowledge of grid vulnerabilities can craft such attacks to maximize disruption towards the grid.
-
Power grid instability: Synchronized oscillatory load attacks can push the grid beyond safe frequency operation limits. This can cause load shedding or even blackouts if the grid's stability is compromised. Attackers can leverage remote control capabilities provided by mobile applications to execute these attacks, exacerbating the grid's instability during peak load times.
-
Economical impact: Large-scale attacks on the EVs charging infrastructure can lead to significant economic impacts. Attackers can synchronize charging or discharging events to create artificial demand peaks, increasing generation costs and transmission losses. This could also lead to increased electricity prices due to the need for additional generation capacity to meet the artificially increased demand.
Relay Attack on EVs charging systems:
V2G facilitates communication between EVs and the power grid, enabling smart charging, automated billing, and especially bidirectional power flow [10]. ISO 15118 is the standard supporting these functionalities. It enables high-level communication and authentication processes on top of the TLS protocol. One of its features, Plug-and-Charge (PnC), simplifies the charging process by allowing users to start charging simply by plugging in their vehicle, without additional authentication steps at the charging station. A relay attack is a form of cyber-attack where an attacker intercepts and relays communication between two entities, making them believe they are directly communicating with each other. This type of attack is particularly effective in scenarios where the communication is encrypted, as the attacker does not need to decrypt the information but simply forwards it between the entities.
In the context of this attack, an attacker could exploit the V2G communication channel to steal energy. The attack involves relaying the communication between a victim's vehicle and the charging station to the attacker's vehicle. As a result, the attacker’s vehicle receives the charge while the victim’s vehicle is billed for the energy. This is possible because the ISO 15118 standard, despite its advanced features, lacks sufficient measures to prevent such relay attacks. The attack can be extended further if the reverse charging flow is enabled, allowing the attacker to sell the energy from the victim's vehicle back to the grid, thereby profiting from the sale while leaving the victim's battery depleted. Experimental results have demonstrated the effectiveness of the attack in charging environments, proving that the vulnerability could be exploited to steal energy.
Electromagnetic (EM) side-channel attacks:
The Combined Charging System (CCS) employs PLC for communication between the EV and the charger. It uses differential signalling to minimize EM emissions. However, in practice, these implementations often deviate from the ideal, leading to single-ended signalling, which significantly increases susceptibility to EM side-channel attacks. This vulnerability allows an attacker to use an antenna to intercept the EM emissions generated by the PLC signals. These emissions can then be analyzed to reconstruct the original communication data exchanged between the EV and the charger. Researchers have demonstrated that this method enables an attacker to recover messages with a high degree of accuracy, achieving a 91.8% validation rate of CRC32 checksums. This implies that an attacker can effectively eavesdrop on the communication between the EV and the charger from an adjacent parking bay.
Are EVs Charging Protocols Secure Enough to Current Cyber Threats?
The above-mentioned attacks highlight different security risks and vulnerabilities present in the current EVs charging infrastructure. Existing charging authentication and authorization protocols, such as ISO 15118, OCPP (Open Charge Point Protocol), and OCPI (Open Charge Point Interface), suffer from various security and privacy issues, including inadequate authentication mechanisms, weak encryption practices, and susceptibility to relay and eavesdropping attacks. Many of these protocols were designed with interoperability and efficiency in mind but lack the robust security measures necessary to counter evolving cyber threats. Additionally, the reliance on plaintext communications (in some ICS protocols), insufficient session verification, and weak identity management expose EVs owners to potential identity theft, unauthorized billing, and service disruptions.
How Can We Strengthen EVs Charging Security Against Cyber Threats?
As a result of rapidly growing EVs usage, attackers could exploit these weaknesses on a large scale, leading to severe financial, operational, and even grid stability risks. Therefore, it is essential to develop new, secure, and privacy-preserving communication frameworks that ensure data confidentiality, integrity, and authentication while maintaining seamless charging. Advanced cryptographic techniques, such as post-quantum cryptography, zero-knowledge proofs, and blockchain-based authentication, could play a crucial role in safeguarding EVs charging networks. Standardization efforts must also focus on enforcing stronger security policies, real-time anomaly detection, and continuous firmware integrity checks to mitigate emerging threats and enhance the resilience of the EVs charging infrastructure.
References
[11] “Customer engagement platform,” Twilio. Accessed: Mar. 02, 2025. [Online].
Edited By: Windhya Rankothge, PhD, Canadian Institute for Cybersecurity
Related Blogs: Cybersecurity challenges of self-driving cars: How can machine learning help?