
An Introduction to the Maze Ransomware
What is the Maze Ransomware?
"Ransomware is a type of malware from cryptovirology that threatens to publish the victim's data or perpetually block access to it unless a ransom is paid" [1]. The Maze ransomware was first detected in May 2019 by Jerome Segura [2]. It is a new kind of ransomware because it exfiltrates data from the victim's computer to a remote server before encrypting them. Thus the Maze ransomware can demand two times payment to the victims: 1) for a decryptor to recover the encrypted data, and 2) for not releasing the stolen data to the public. Some other well-known ransomware such as Sodinokibi, Nempty, DoppelPaymer, Ragnarlocker, etc. are now following the same steps of the Maze [3].
Attack process and timeline
The common mean of Maze ransomware attacks are macro-enabled email attachments [4], remote desktop connection with poor password [5], exploit kit [6], or the server vulnerabilities [7, 8], etc. After gaining access to the victim's computer(s) through the approaches mentioned earlier and a reconnaissance and lateral movement stage, the Maze is executed. Upon execution, Maze will scan files and exfiltrates them to a file server. It will then encrypt and append different randomly generated extensions to the encrypted files. A Maze note is placed in each folder, as shown in Fig. 1 [9]. The Maze will attempt to connect to various websites by IP address (C2 servers). It will delete shadow copies to ensure that all the data cannot be restored easily [3]. If the victim does not pay the ransom, the data is released to the public [10].
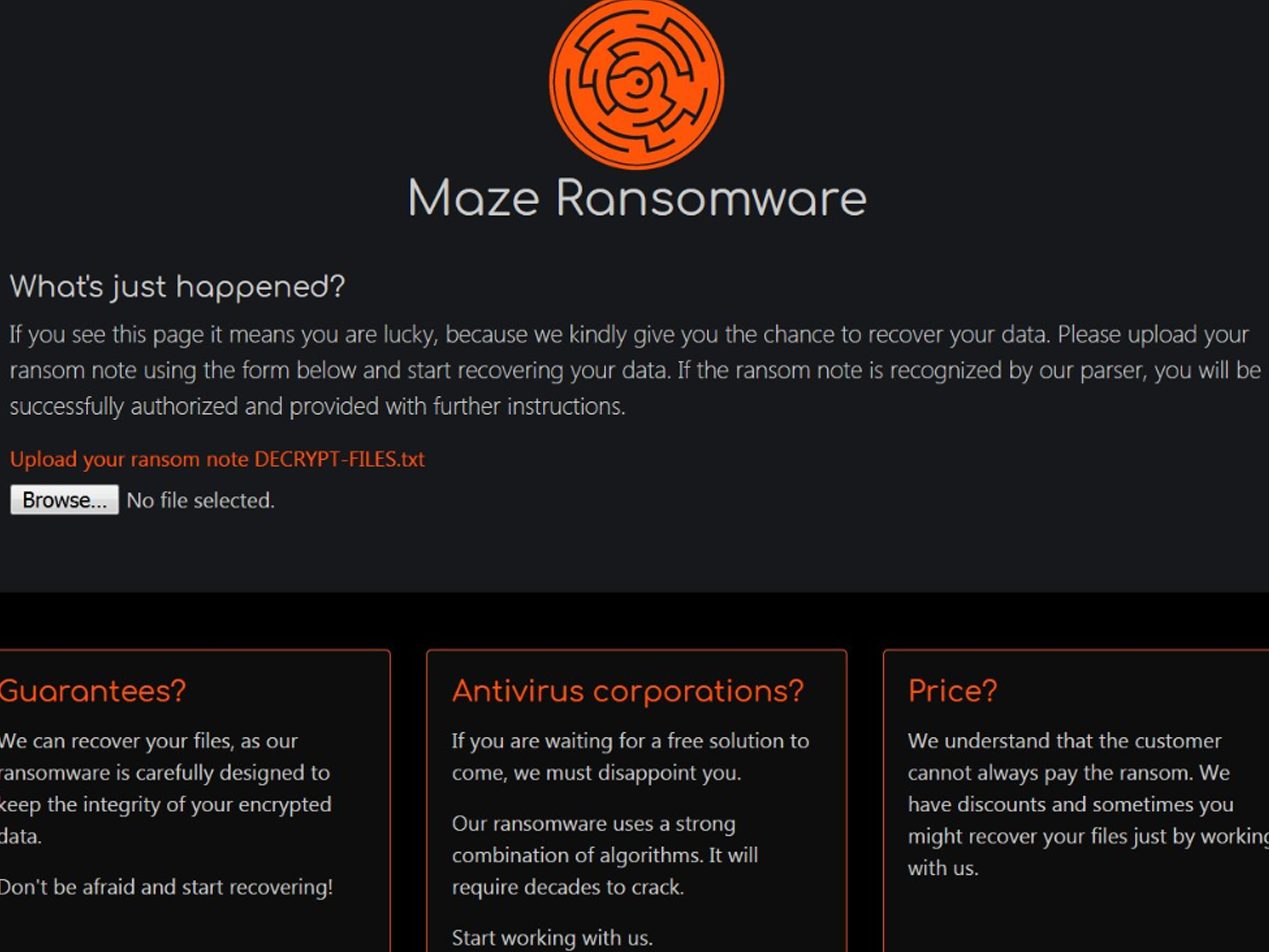
Figure: A snapshot of Maze ransomware attack notification on victim's computer [9]
Hacker groups such as FIN6 and TA2101 are believed to be responsible behind the Maze ransomware. It was also reported that Maze does not attack any system if the language set on the system is Russian (from Russian Federation or Moldova), Ukrainian, Belarusian, Tajik, Armenian, Azerbaijani, Georgian, Kazakh, Kyrgyz, Turkmen, Uzbek, Tatar, Romanian (from Moldova, nor Romania) and various dialects of Serbian [3].
A Maze ransomware incident timeline can expand over three weeks [3, 9]. The first week is for initial compromise when Cobalt Strike artifacts are deployed in the victim's computer(s) and network, and internal administrative accounts are compromised. The second week is for reconnaissance, during which data are typically stolen and uploaded to a file server. In the third week, Maze ransomware spreads and halts the network. At this point, the victims become aware of the attack and begin response actions.
Recent victims of the Maze Ransomware
Recently, the Maze ransomware has victimized IT firms [11], law firms [12], medical providers [13], cybersecurity insurance firms [14], etc. The Maze ransomware operators are interested in making money only because, on March 18, 2020, they mentioned that they would not target health providers during the COVID19 pandemic. However, they released medical customer data on May 5, 2020, after the victim denied to pay the ransom [13]. The maze operators may also sell the information on the dark web even after receiving the ransom payment for not disclosing it.
How to protect against the Maze Ransomware
There are several recommendations available for protection against Ransomware [15]. Besides, using updated security software and install OS patches, we should keep 1) a secure offline backup of the system and data, 2) ensure the use of a strong and unique password, and 3) encrypt data whenever possible. A strong password can reduce the risk of a Maze attack through RDP. Encrypting data beforehand avoids the ransom threat for public disclosure of stolen data. It is important to increase cybersecurity awareness among the employees through training and education. Because more and more employees are now working from home due to the COVID-19 pandemic, which increases the risk of unauthorized access from a less secure home environment.
* Image source [4]