Don't become a victim of a RAT (Remote Administration Tool) strike!
Remote Administration Tool (RAT)
RAT is a software that remotely gives a person total control over a machine. Remote Administration Tools (RATs) come with several malicious features and different Anti-malware commercial products recognize RATs such as Trojan\Backdoor. The RAT gives the attacker access to your machine, just as if they had normal physical access to your device (or more). For instance, a RAT is equipped with sophisticated features like password sniffing, detailed process manager, file manager to edit files (add, delete, upload, download, execute, rename), use of the victim’s camera, and many others.
History of RAT
Security companies have been struggling to detect Trojan and Backdoor programs because they have been created in unprecedent numbers and equipped with different obfuscation techniques. It is widely known that RAT programs are among the largest subset of Trojans and Backdoors—malware category. The figure below gives details about the distribution of RAT samples.
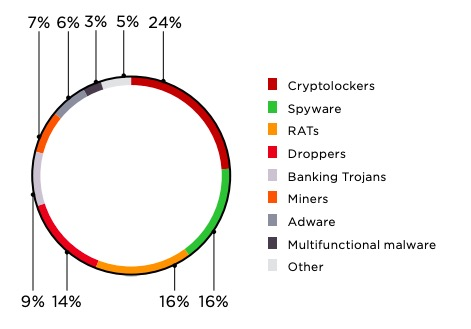
Image source: https://www.ptsecurity.com/ww-en/analytics/cybersecurity-threatscape-2019-q1/
Although, a complete RAT history is unknown, there are several types of RAT programs developed in the past two decades and we have highlighted the three main types based on their features:
-
Direct and reverse connection.
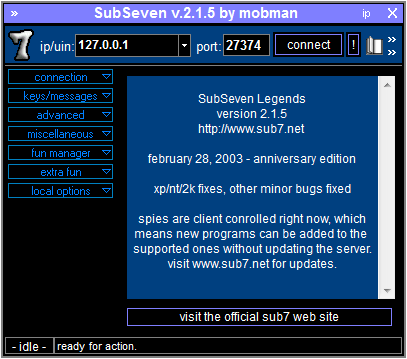
SubSeven (Sub7) was one of the popular legacy RAT programs which started in 1999. Sub7 was created by someone under the name MOBMAN and was an advanced RAT which mainly operated between the years 1999-2002. Before the year 2004, most RAT programs involved a direct connection—a traditional client\server connection. Normally, the attacker created a server file (trojan file) and sent it to the victim. Once the victim executed the file and if the file was successfully deployed, the attacker had total control of the victim’s machine. In the year 2004, Beast RAT was the first RAT to implement the reverse connection concept and the main idea behind reverse connection was to bypass firewall restrictions on open ports. The below figures give details about how an attacker could establish a connection with the victim’s machine using direct or reverse connection.

Reverse Connection

Direct Connection
-
Advanced stealth techniques and firewall bypass.
From the year 2004 and afterwards, a new era of RAT creation was based on reverse connection and the development in programming languages caused RAT development to increase substantially with examples being multithreading, advanced screen capturing, firewall bypassing techniques and code obfuscation. Interestingly, attackers favorite programming languages to create RAT programs were Delphi and pure C++, because they do not require dependencies files to run the executable file. In addition, process injection techniques are another widely used methods to evade firewalls protection used in many RAT programs. -
Obfuscation and ransomware.
Among the latest RAT features are obfuscation and ransomware. Code obfuscation refers to making the code obscure and recent RAT programs involve code obfuscation techniques to make the trojan difficult to detect by Anti-virus programs, and techniques such as dead code, packing, code shuffling and many others are used. In addition, some RATs are equipped with a ransom that can be deployed at any time.
The below are some RAT programs and main features:
-
Beast RAT (2004) which was the first RAT to use reverse connection.
-
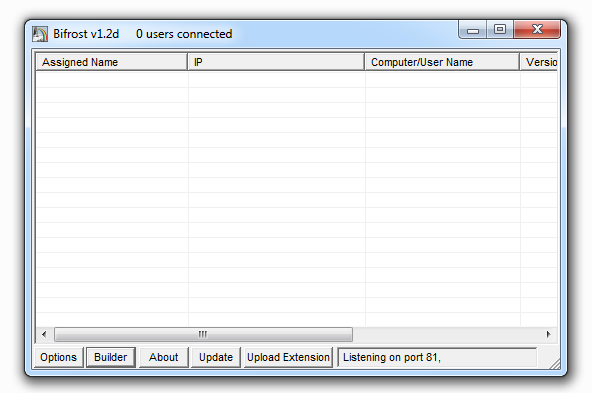
Bifrost RAT (2004) which implemented a new method to bypass firewall, namely FWB#++ (Code injection, API unhook, kernel patch) among others are Flux RAT and Optix Pro RAT.
-
Flux RAT which proposed new screen capture and password sniffing features.
-
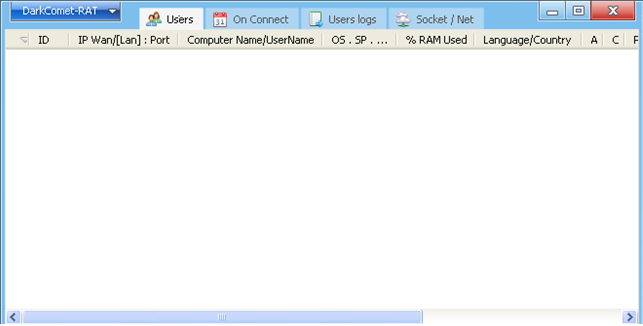
DarkComet RAT (2008) which introduced Downloading Database.
-
LimeRAT (2019) which introduced ransom payload.
RAT Prevention
In conclusion, we suggest the below best practices for avoiding a RAT attack:
-
Always have a good Anti-Virus software installed in your system. Recommended and best anti-virus programs can be found here: https://www.av-test.org/en/ .
-
Keeping your system updated.
-
Never clicking on untrusted links or execute untrusted software.
-
Being aware of phishing and spam emails.
Preview (Thumbnail) on RAT interfaces.