Bosa Cyber Security is a modern, multipurpose WordPress theme crafted specifically for technology websites. It’s fast, lightweight, responsive, and beautifully designed—perfect for cyber security services, network security teams, data protection agencies, inf…
Bosa Cyber Security is a modern, multipurpose WordPress theme crafted specifically for technology websites. Its fast, lightweight, responsive, and beautifully designedperfect for cyber security servi… [+1598 chars]
The bigger threat to U.S. companies may not be a data breach, but a coordinated campaign designed to make your employees stop trusting everything they see and hear.
As strikes hit Tehran on Saturday morning, millions of Iranians got a strange push notification on their phones. The BadeSaba Calendar prayer app, which has more than 5 million downloads, had been co… [+6397 chars]
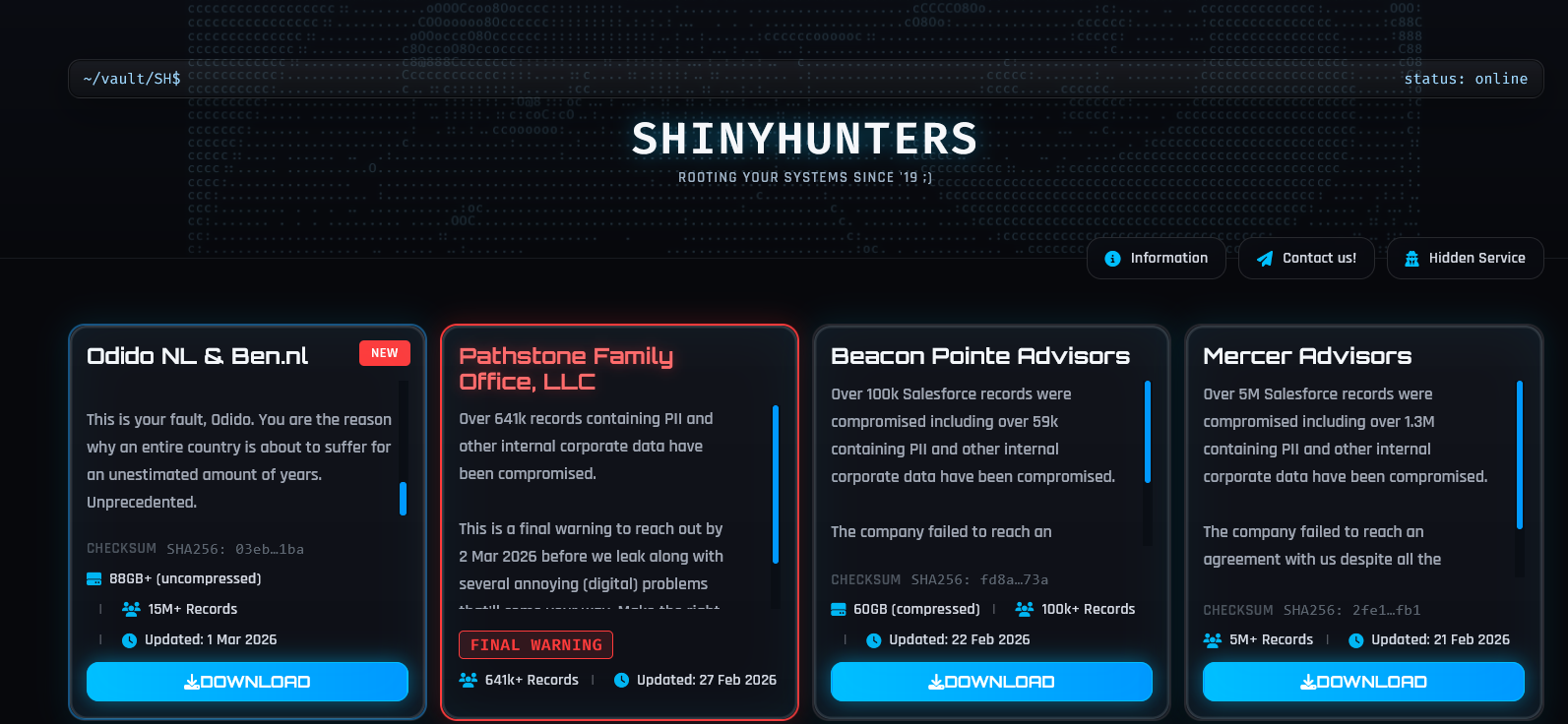
Cybercrime group ShinyHunters leaked the full Odido dataset, the Netherlands is facing the biggest data leak in its history. Odido is a Dutch telecommunications company and one of the largest mobile network operators in the Netherlands. It was formed when T-M…
ShinyHunters leaked the full Odido dataset
Odido is a Dutch telecommunications company and one of the largest mobile network operators in the Netherlands. It was formed when T-Mobile Netherlands and… [+3094 chars]
KUALA LUMPUR: The Malaysian Communications and Multimedia Commission (MCMC) is adopting a more community-friendly approach in implementing the 2026 Internet Safety Campaign (KIS) to ensure digital safety messages are conveyed more effectively at the grassroo…
KUALA LUMPUR: The Malaysian Communications and Multimedia Commission (MCMC) is adopting a more community-friendly approach in implementing the 2026 Internet Safety Campaign (KIS) to ensure digital sa… [+878 chars]
None
If you click 'Accept all', we and our partners, including 246 who are part of the IAB Transparency & Consent Framework, will also store and / or access information on a device (in other words, us… [+1046 chars]
As AI systems become more complex the risk of surpassing human comprehension, not intelligence, could lead to chaos, artificial intelligence experts warn.
As the business world comes to grips with artificial intelligence, the biggest risk may be one where those running the economy can't possibly stay ahead. As AI systems become more complex, humans are… [+7513 chars]
Google's Dark Web Report removal eliminates automated breach scanning for users, though Security Checkup and Password Manager remain available as alternative security tools.
Google has officially discontinued its Dark Web Report feature, a free tool that once scanned known dark web breach dumps for personal information tied to a user's Google account. The service deliver… [+6516 chars]
A data breach at Canadian Tire exposed personal data from over 38 million accounts, including contact details and encrypted passwords. More than 38 million accounts were affected by an October 2025 data breach at Canadian retail giant Canadian Tire (CTC). The…
Canadian Tire 2025 data breach impacts 38 million users
More than 38 million accounts were affected by an October 2025 data breach at Canadian retail giant Canadian Tire (CTC). The incident marks on… [+1767 chars]
Leverage trigger events and learn to identify, track, and capitalize on high-intent signals for a 5x increase in conversion rates. See more.
Trigger Events and learn what a trigger event is and how to leverage business shifts to accelerate sales. Learn to identify, track, and capitalize on high-intent signals for a 5x increase in conversi… [+21033 chars]
The cheap vacation illusion that could cancel your trip and freeze a stranger’s bank account
<ul><li>Buyers of cheap travel deals often face canceled bookings and lost money</li><li>Fraudulent travel reservations can appear legitimate until banks freeze accounts unexpectedly</li><li>Cardhold… [+3777 chars]
The DOJ has sued Utah, Oklahoma, West Virginia, Kentucky, and New Jersey, demanding they hand over complete voter rolls with sensitive personal information. This action is part of a broader campaign where the Trump administration has now sued nearly 30 states…
<ul><li>The DOJ has sued Utah, Oklahoma, West Virginia, Kentucky, and New Jersey, demanding they hand over complete voter rolls with sensitive personal information.</li><li>This action is part of a b… [+4473 chars]
Reuters:
Coupang reports Q4 revenue up 11% YoY to $8.8B, below $8.9B est., and a net loss of $26M, versus $131M net profit in Q4 2024, hurt by fallout from a data breach — E-commerce giant Coupang (CPNG.N) swung to a fourth-quarter loss on Thursday and repo…
About This Page
This is a Techmeme archive page.
It shows how the site appeared at 12:40 AM ET, February 28, 2026.
The most current version of the site as always is available at our home page.
To… [+72 chars]
CASTRIES, Saint Lucia, Feb. 27, 2026 (GLOBE NEWSWIRE) -- 2328.io today announced the global launch of its infrastructure-grade cryptocurrency payment platform designed for online businesses operating in cross-border and digital-native markets.
CASTRIES, Saint Lucia, Feb. 27, 2026 (GLOBE NEWSWIRE) -- 2328.io today announced the global launch of its infrastructure-grade cryptocurrency payment platform designed for online businesses operating… [+4941 chars]
The payments giant PayPal says a cybersecurity incident left highly sensitive customer information exposed for around six months. In a data breach notice submitted to the Commonwealth of Massachusetts, PayPal says it’s resetting affected customers’ passwords …
The payments giant PayPal says a cybersecurity incident left highly sensitive customer information exposed for around six months.
In a data breach notice submitted to the Commonwealth of Massachuset… [+1855 chars]
Germany's Federal Office for Information Security (BSI) approved Apple's iPhone and iPad devices as long as they're running iOS 26 and iPadOS 26 or better.
According to the press release, NATO found that Apple chips offer enough security and privacy, combined with iOS updates, that members of the organization can check restricted documents for the first… [+1101 chars]
Is your AI assistant safe? Oasis Security researchers have found a critical ClawJacked vulnerability in OpenClaw that allows hackers to hijack AI agents through a simple browser tab.
It has been a whirlwind few months for Peter Steinberger and his creation, OpenClaw. The AI tool, which acts as a personal assistant for developers, exploded in popularity, racking up 100,000 GitHub … [+4270 chars]
NATO, the North Atlantic Treaty Organization, has authorized Apple mobile devices for use with classified information within the organization, according to Apple. This makes the iPhone and the iPad the first (and currently only) consumer devices to meet NATO'…
Apple's mobile devices may soon help secure world peace.
Apple announced this week that the iPhone and iPad were approved to handle secure and classified information for NATO, requiring no additiona… [+1209 chars]
NEW DELHI: The National Human Rights Commission has issued notices to all states and Union territories, as well as certain central government departments, over alleged risks to children’s privacy arising from a collaboration between a US-based artificial inte…
NEW DELHI: The National Human Rights Commission has issued notices to all states and Union territories, as well as certain central government departments, over alleged risks to children’s privacy ari… [+3077 chars]
Apple's iPhone and iPad devices running iOS and iPadOS 26, respectively, have become the first consumer-grade mobile devices officially approved to handle classified NATO information. This certification, announced by Apple following an evaluation by Germany’s…
Apple's iPhone and iPad devices running iOS and iPadOS 26, respectively, have become the first consumer-grade mobile devices officially approved to handle classified NATO information. This certificat… [+2363 chars]
The why and how of securing AI infrastructure - today's threats make it no longer optional.
I believe that 2026 will be a defining year for cybersecurity.
Sometime during the year, AI-powered threats will have the ability to adapt in real time. This will force organizations to defend again… [+7202 chars]
When it comes to any financial system, trust and security are paramount. Without them, participation […]
When it comes to any financial system, trust and security are paramount. Without them, participation slows, liquidity dries up, and even the most innovative technology struggles to gain mainstream ac… [+9499 chars]
If a hacker or scammer has access to your email, every account connected to it is at risk. We show you how to protect yourself fast.
There's a good chance you've been using the same email address everywhere online. For example, the address you use for your ba…
There's a good chance you've been using the same email address everywhere online. For example, the address you use for your bank account is likely the same one you use for your streaming accounts. Th… [+8875 chars]
If a hacker or scammer has access to your email, every account connected to it is at risk. We show you how to protect yourself fast.
There's a good chance you've been using the same email address everywhere online. For example, the address you use for your ba…
There's a good chance you've been using the same email address everywhere online. For example, the address you use for your bank account is likely the same one you use for your streaming accounts. Th… [+8875 chars]
A fake site about hot dog-eating capabilities may seem funny, but behind the laughs lies a series of serious cybersecurity failures.
When Microsoft cut off support for the millions of PCs still running Windows 10, the goal was to force people to either upgrad…
When Microsoft cut off support for the millions of PCs still running Windows 10, the goal was to force people to either upgrade to Windows 11 or buy new PCs that came preinstalled with it. Predictabl… [+6544 chars]
A fake site about hot dog-eating capabilities may seem funny, but behind the laughs lies a series of serious cybersecurity failures.
When Microsoft cut off support for the millions of PCs still running Windows 10, the goal was to force people to either upgrad…
When Microsoft cut off support for the millions of PCs still running Windows 10, the goal was to force people to either upgrade to Windows 11 or buy new PCs that came preinstalled with it. Predictabl… [+6544 chars]