Reverse Engineering Made Easy: A Beginner’s Guide to Interactive Disassembler (IDA) Pro
Reverse engineering is a crucial process in cybersecurity, malware analysis, and software security research, and IDA Pro stands as one of the most powerful tools in this domain. This blog post provides an in-depth look at IDA Pro, the industry-standard disassembler and debugger developed by Hex-Rays, highlighting its key features, capabilities, and why it remains a preferred choice among security researchers and analysts. From its advanced disassembly and debugging functions to graph visualization, cross-referencing, and scripting support, we will explore how IDA Pro helps in understanding complex binaries.
Overview
Interactive Disassembler (IDA) Pro, developed by Hex-Rays, is a leading tool in reverse engineering, designed to convert a machine-executable code into an assembly language source code. It supports a wide range of executable formats for various processors and operating systems, making it a preferred choice for developers, security researchers, and analysts across different platforms. IDA Pro has been established as an industry-standard tool, due to its powerful features, flexibility, and comprehensive support for debugging, disassembly, and reverse engineering tasks.
Beyond its disassembly capabilities, IDA Pro functions as a debugger for Windows PE (WinPE), Mac OS’s X Mach-O, and Linux Executable and Linkable Format (ELF) executables, allowing for comprehensive analysis across multiple platforms. Additionally, IDA Pro offers an optional decompiler plug-in that produces a C-like source code representation, facilitating easier understanding of complex programs. This feature, however, is available at an extra cost. Below is an image showing the free version of IDA Pro displaying an application in assembly code.
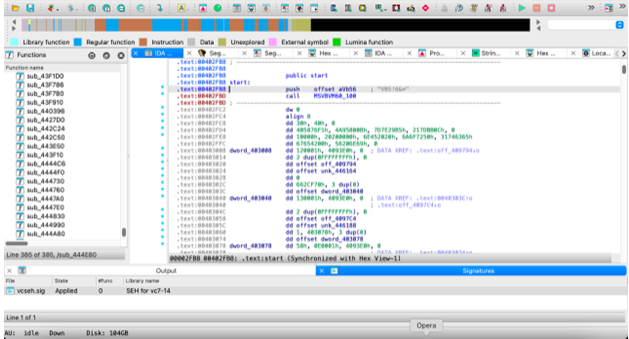 IDA Pro (for Mac) displaying an application in assembly code.
IDA Pro (for Mac) displaying an application in assembly code.
While the Ghidra, a free and open-source software developed by the National Security Agency (NSA) of the United States, also provides similar decompilation features, IDA Pro remains more powerful due to its advanced capabilities and extensive plugin ecosystem. IDA Pro offers superior performance in handling large binaries, more intuitive user interface, and a broader range of analysis features, including highly customizable scripting options and robust support for various architectures. These advantages make IDA Pro the preferred tool for professionals dealing with intricate reverse engineering tasks.
Key Features of IDA Pro
Disassembly View:
One of the fundamental features of IDA Pro is its disassembly view, which plays a critical role in reverse engineering. In this view, IDA Pro converts raw machine code into assembly language instructions, offering a human-readable representation of the program’s low-level operations. The disassembly is presented in a linear, sequential format, allowing you to meticulously inspect the individual instructions executed by the processor. This enables a deeper understanding of how a program functions at the machine level, which is essential for tasks such as vulnerability analysis, malware analysis, and understanding proprietary or obfuscated code. The disassembly view also offers various navigation tools to jump between functions, variables, and code sections, facilitating efficient exploration of complex software.
Function Identification:
A key feature of IDA Pro is its ability to automatically identify and label functions within the disassembled code, significantly aiding in the navigation and analysis of a program's structure. IDA Pro uses sophisticated heuristics to detect the boundaries of functions, recognizing patterns such as function prologues and epilogues to determine where functions begin and end. This automatic labeling allows users to easily understand the program's flow by giving meaningful names to function locations. However, IDA Pro also provides the flexibility for users to manually adjust or redefine these function boundaries as needed, ensuring more accurate or customized analysis. Users also can assign their own labels to functions for better context, improving the overall readability and interpretability of the code. This feature is invaluable for reverse engineers, as it helps to organize complex and often obfuscated code into a more manageable and understandable structure, ultimately making the reverse engineering process more efficient.
Cross-Referencing:
One of the powerful features of IDA Pro is its cross-referencing capabilities, which allow users to trace and visualize the relationships between functions, variables, addresses, and other elements of the code across the entire program. This functionality provides a comprehensive map of where specific functions or data are used, making it easier to understand how different parts of the program interact with one another. By simply selecting a function, variable, or address, users can instantly view all instances where it is referenced, whether within the same function, across multiple functions, or in different modules of the program. This feature is invaluable in reverse engineering, as it enables users to quickly identify how data flows through the program, which functions are invoked at different points, and how various program components work together. Cross-referencing also facilitates debugging and vulnerability analysis by helping users pinpoint the locations of critical operations and their connections, ultimately streamlining the reverse engineering process.
Graph View:
The Graph View in IDA Pro is an advanced visualization tool that provides a clear, graphical representation of the program’s control flow. This view displays the connections between functions and the sequence in which they are executed, allowing users to follow the program’s execution logic in an intuitive, visual format. Each function is represented as a node, and the edges between nodes depict the control flow, illustrating how the program transitions between different parts of its code. This visual structure makes it easier to understand complex code paths, particularly in larger programs or when dealing with obfuscated or highly optimized code. The Graph View can highlight conditional branches, loops, and jumps, helping users quickly identify key decision points and flow control mechanisms within the program. This feature is invaluable for debugging, as it allows users to visualize the path of execution in real-time, making it easier to spot errors, inefficiencies, or vulnerabilities. It also simplifies the process of reverse engineering by offering a high-level overview of how the program operates, so users can grasp the overall flow before diving into more detailed, line-by-line analysis in the disassembly view. The ability to switch between graph and disassembly views further enhances the workflow by offering complementary perspectives on the same program.
Plugin Support:
IDA Pro offers robust plugin support, allowing users to extend the functionality of the disassembler through third-party or custom-built plugins. These plugins can automate tasks, add new analysis capabilities, or integrate with external tools. The ability to install and use plugins enhances IDA’s versatility, making it adaptable to different reverse engineering needs. Some popular plugins can help with decompilation, visualization, and even malware analysis, providing advanced features that save time and improve workflow efficiency.
C View:
IDA Pro’s C View provides a higher-level representation of the disassembled code, translating the low-level assembly instructions into a more readable C-like pseudocode. This view is particularly useful for analysts who need to understand the functionality of a program without having to parse complex assembly language manually. The C View offers a more intuitive approach to reverse engineering, as it presents the code in a structure that is similar to the original high-level programming language, making it easier to identify logic, functions, and variables. It provides a simplified abstraction of the code while still maintaining the accuracy of the disassembly, helping users to focus on the broader program structure rather than getting lost in assembly details.
Scripting with the IDC Pro and Python:
IDA Pro supports scripting with its built-in IDC (IDA C) language and Python, allowing users to automate repetitive tasks, create custom analysis scripts, or extend the functionality of IDA. This is particularly useful for handling large and complex binaries more efficiently.
REFERENCES:
- Hex-Rays, “IDA Pro: The Interactive Disassembler,” 2025.
- Rohleder, Roman. "Hands-on ghidra-a tutorial about the software reverse engineering framework." In Proceedings of the 3rd ACM Workshop on Software Protection, pp. 77-78. 2019.
Edited By: Windhya Rankothge, PhD, Canadian Institute for Cybersecurity
Related Blogs: The CrowdStrike Outage: Analysis and Lessons Learned