
Malware Packers: The Hidden Threat Inside Modern Cyber Attacks
Malware packers obscure malicious code, helping it evade detection by compressing or encrypting files. This blog covers types of packers, their uses, and effective methods for identifying and unpacking hidden threats.
Malware Packers
A malware packer is a software tool designed to compress, encrypt, or obscure malware, making it more difficult for antivirus programs and security tools to detect. While packers change the appearance of the malware, they don't alter its malicious behavior. Instead, they wrap the malware in layers of code to hide its signature or functionality from analysis. When executed, the packer unpacks or decrypts the malware in memory, allowing it to run undetected. Attackers often use packers to bypass standard security defenses and evade detection.
Types of Malware Packers
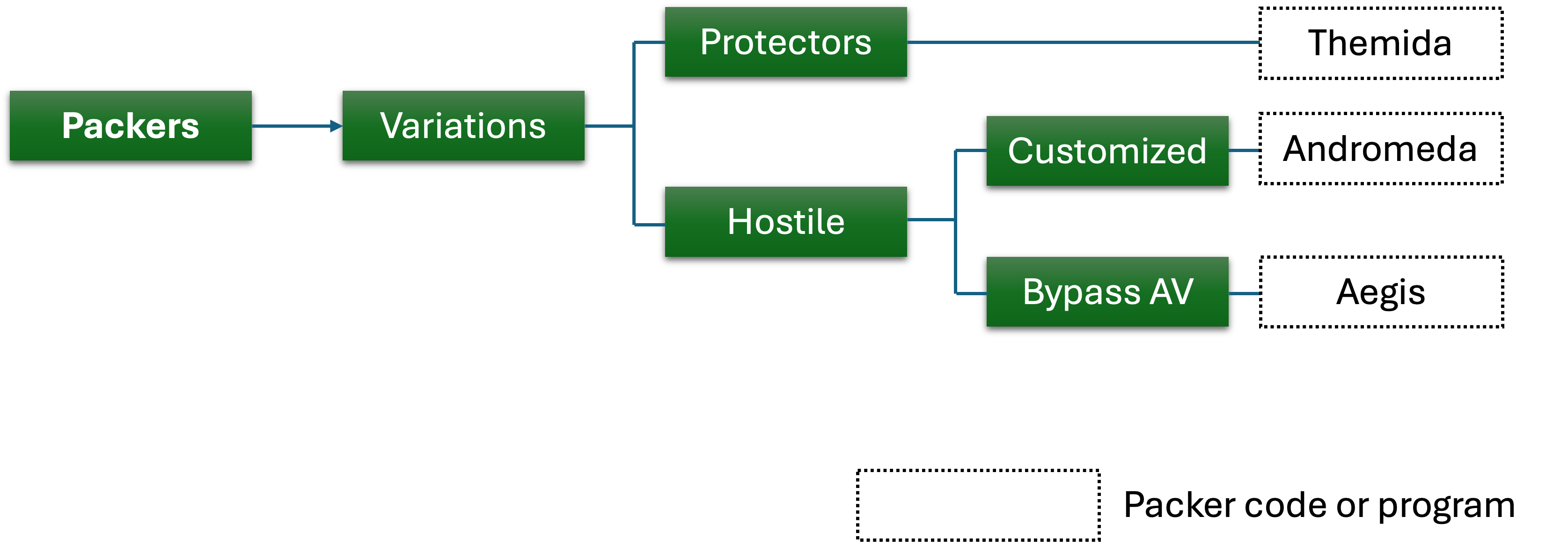
Malware packers can be classified into Hostile Packers and Protectors:
Hostile Packers (Malicious Packers): These packers are used by attackers to conceal malware, making it harder to detect by antivirus software and security tools. Hostile packers employ techniques such as encryption, polymorphism, or metamorphism to hide the true nature of the malware and evade detection, allowing malicious code to bypass security systems.
Protectors (Non-Malicious Packers): These packers are used for legitimate purposes such as reducing file sizes, protecting intellectual property, or improving software performance. They are commonly used by developers to compress or safeguard executable files without any harmful intent.
The key difference lies in their purpose: Protectors serve legitimate functions, while Hostile Packers are designed to disguise and deliver harmful software. The following figure illustrates the types of packers.

Mitigation of Malware Packers
Mitigating packers, especially hostile ones, involves two key processes: Identification and Unpacking
Here’s a breakdown of the strategies:
Identification of Packers:
Identifying packers involves detecting the presence of compressed or encrypted code and other essential artifacts within executables. Common techniques include:
-
Signature-Based Detection:
Security tools use a database of known packer signatures to identify specific packers. While effective for well-known packers, it may struggle with custom or unknown variants. -
Heuristic Analysis:
This method identifies unusual patterns or suspicious behavior, such as runtime memory manipulation, anti-debugging techniques, or obfuscated code, which are typical signs of packed files. -
Entropy Analysis:
Packers increase the randomness (or entropy) of files. High entropy levels can be an indicator of packed or encrypted code, signaling potential malware. -
Machine Learning Models:
Advanced security solutions use machine learning to detect patterns and anomalies in file structures as in [2], that could indicate packing, improving detection of custom or unknown packers.
Unpacking of Packers:
Once a packed file is identified, the next step is to unpack it to reveal the hidden payload. Techniques for unpacking include:
-
Automated Unpacking Tools:
Tools such as UnpacMe, UPX (for specific packers), or custom unpackers are designed to reverse the packing process. These tools attempt to extract the original malware by removing the packing layers. -
Memory Dumping:
Some packers only unpack the malware during execution. By running the malware in a controlled environment and dumping the memory contents at key points, analysts can capture the unpacked malware directly from memory. -
Emulation:
By emulating the malware's execution in a sandbox, the packer can be forced to unpack itself. The malware is then analyzed post-unpacking without the need for full execution on a live system. -
Manual Reverse Engineering:
For sophisticated packers that evade automated tools, analysts may use reverse engineering techniques. This involves using debuggers (e.g., IDA Pro, Ghidra) to step through the code, identify the unpacking routines, and manually extract the hidden malware.
REFERENCES:
-
Alkhateeb, Ehab, Ali Ghorbani, and Arash Habibi Lashkari. "A survey on run-time packers and mitigation techniques." International Journal of Information Security 23, no. 2 (2024): 887-913.
-
Alkhateeb, Ehab, Ali Ghorbani, and Arash Habibi Lashkari. "Identifying Malware Packers through Multilayer Feature Engineering in Static Analysis." Information 15, no. 2 (2024): 102.
Edited By: Windhya Rankothge