Enhancing Lateral Movement Detection with Graph Learning
Discover how graph learning revolutionizes lateral movement detection by modeling network relationships and training machine learning classifiers to distinguish malicious activity from legitimate paths, enhancing cybersecurity defenses against advanced threats.
What is Lateral Movement?
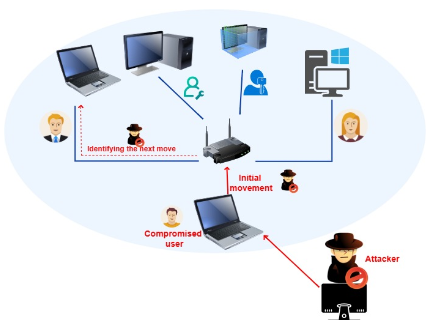
Lateral movement, a crucial phase in the Advanced Persistent Threat (APT) life cycle, refers to a strategy employed by adversaries to traverse horizontally within a network. The objective is to gain access to various systems or resources, thereby expanding their control and potential access to valuable targets. By mimicking legitimate user behavior, attackers can escalate their privileges and gain access to valuable targets, resulting in unauthorized access and potential data compromise. The serious consequences of undetected lateral movement emphasize the critical need for robust detection mechanisms.
The Challenges of Traditional Detection Techniques
Traditional methods for detecting lateral movement often fall short in the face of modern network complexities. Detecting these attacks becomes challenging for conventional detection systems due to various factors, including the complexity of pathways, the mimicking of legitimate user behavior by attackers, and limited network visibility. To address these challenges, advanced detection techniques are required to effectively and dynamically analyze multiple features within the interconnected structure of the network.
The Power of Graph Learning
Graph learning employs machine learning to facilitate a dynamic, feature-rich decision-making process that uncovers relationships among network elements. In the context of lateral movement detection, graph learning offers a transformative approach to overcoming traditional challenges. By modeling network entities as interconnected graphs, this technique captures and analyzes the relationships between nodes, such as users, devices, and actions, to extract valuable insights from their interactions.
Practical Application in Network Environments
In real-world network environments, such as intranets or industrial networks, the interconnected nature of computers creates a rich landscape for detecting lateral movement. Cybercriminals often infect a host with malware to gain remote control, using it as a springboard to traverse laterally and infiltrate other nodes in pursuit of valuable assets. Effectively identifying these movements depends on a thorough understanding of the relationships between devices, making it essential to grasp the structure of interconnected hosts.
This blog focuses on simplifying lateral movement detection within interconnected networks through node embedding and graph learning. This graph learning approach consists of two phases. In the first phase, the network structure is represented as a heterogeneous directed graph, where node embedding is used to create efficient feature vectors. In the second phase, these feature vectors are applied to train a machine learning-based classifier to establish a detection system that can distinguish malicious lateral movement paths from benign activities.
Graph Construction, Node Embedding, and Feature Vector Creation
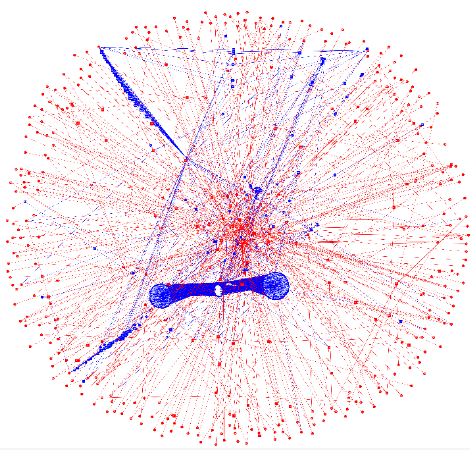
The initial step in this approach involves constructing a topological structure (a graph of interconnected nodes) that represents the relationships within the network. Each authentication request is converted into a directed heterogeneous graph representation. The directed heterogeneous graph shown in Figure 1 is constructed using authentication records, with benign activities highlighted in blue and malicious activities in red. This visualization facilitates a clear understanding of relationships among various network elements, which distinguishes normal interactions from potential threats.
After constructing a large heterogeneous graph based on all interconnected nodes within the network, a node embedding technique utilizing DeepWalk is applied to effectively traverse neighboring nodes, capturing information from both first-order and second-order proximities and embedding this data in the source node. These embedded features are then concatenated to form a final feature vector that integrates node-specific information along with additional non-embedded features derived from the metadata of the authentication paths. Subsequently, these features are utilized to train multiple machine learning classifiers to detect malicious lateral movement paths among benign paths.
A Machine Learning-Based Classifier for identifying Lateral Movement Paths
In this phase, multiple machine learning techniques are utilized to identify malicious paths among a vast number of normal paths. Approaches such as Support Vector Machine (SVM), K-Nearest Neighbors (K-NN), logistic regression, gradient boosting, and Extreme Gradient Boosting (XGBoost) are suitable choices for determining the optimal and lightweight classifier for effective detection.
Conclusion
As organizations face increasingly sophisticated cyber threats, implementing graph learning techniques for lateral movement detection is essential. By utilizing the power of graph-based representations, security teams can enhance their ability to identify and respond to potential threats in real time. Implementing these advanced methodologies will lead to more robust defenses and a proactive approach to securing sensitive data against lateral movement attacks.
Edited By: Windhya Rankothge