Quantum Security Risk Assessment and Mitigation
Advancements in quantum computing are transforming cybersecurity, exposing vulnerabilities in current cryptographic systems. Quantum algorithms such as Shor's can break RSA (Rivest–Shamir–Adleman) and ECC (Elliptic curve cryptography), while Grover's weakens AES (Advanced Encryption Standard). To address these threats, the National Institute of Standards and Technology (NIST) is developing Post-Quantum Cryptography (PQC) standards. Additionally, risk assessment frameworks such as STRIDE help identify and mitigate vulnerabilities in cryptographic systems. This article explores the algorithmic-level risk assessment of these vulnerabilities, aligns them with the NIST Cybersecurity Framework (NIST CSF) and STRIDE model, and discusses mitigation strategies, including the migration to quantum-safe cryptography to ensure future-proof systems.
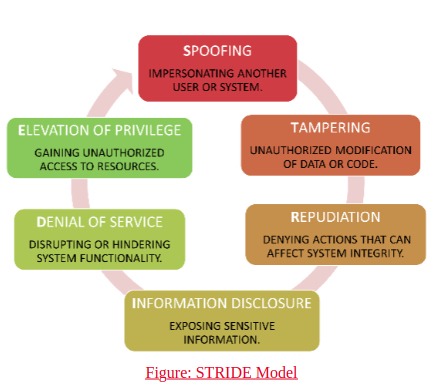
STRIDE Model: A Framework for Risk Assessment
The STRIDE model stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service and Elevation of Privilege, and a useful framework for evaluating potential security threats. It helps organizations assess risks and plan appropriate mitigations. When applied to quantum threats, STRIDE helps identify potential vulnerabilities in cryptographic infrastructure that could be exploited by quantum computers.
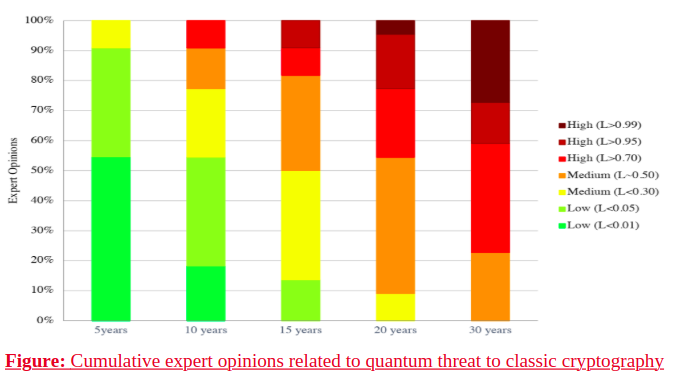
Quantum Threat Timeline and Expert Opinions
The Global Risk Institute's Quantum Threat Timeline Report predicts a greater than 50% likelihood, that large-scale quantum computers capable of breaking classical cryptography will emerge within the next 15 years, providing a critical window for organizations to transition to quantum-resistant systems. Expert consensus agrees that quantum threats to classical cryptography are inevitable, with specific risks for different cryptographic systems. Asymmetric algorithms such as RSA (Rivest–Shamir–Adleman) and ECC (Elliptic curve cryptography) face a high likelihood of quantum attacks due to Shor’s Algorithm, potentially within 15-30 years. Symmetric encryption algorithms such as AES (Advanced Encryption Standard) have a medium likelihood of impact, with Grover’s Algorithm requiring upgrades from AES-128 to AES-256 for equivalent security within 15-20 years. Hash algorithms such as SHA-256 and SHA-512 also face medium threats from Grover’s Algorithm, which could reduce their security strength, though large hash sizes mitigate risks.
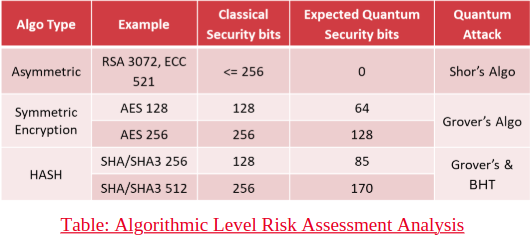
Algorithmic Level Risk Assessment Analysis
This analysis examines the risk posed by quantum threats to cryptographic algorithms, including asymmetric cryptographic algorithms, symmetric encryption algorithms, and hash algorithms, highlighting vulnerabilities and potential impacts.
1. Asymmetric Cryptographic Algorithms:
Algorithms Affected: RSA, ECC, DHE (Diffie-Hellman Key Exchange), and other asymmetric cryptographic algorithms.
Quantum Threat: Shor's Algorithm presents a significant risk to asymmetric cryptography by efficiently solving problems such as integer factorization and the discrete logarithm problem. RSA and ECC algorithms are vulnerable to spoofing, tampering, repudiation for digital signatures, and information disclosure for KEM/ENC. DHE is also susceptible to spoofing and information disclosure.
Risk Assessment:
- Likelihood in 15 years: Medium (Practical quantum computers may be viable in 15–30 years, depending on breakthroughs)
- Impact: High (If Shor’s Algorithm becomes practical, it would compromise all existing asymmetric encryption algorithms.)
- Risk: High
Mitigation Strategies:
- Transition to NIST-recommended post-quantum algorithms (e.g., lattice-based or code-based cryptography).
- Implement hybrid solutions combining classical and post-quantum algorithms for enhanced security during the transition phase.
2. Symmetric Encryption Algorithm
Algorithms Affected: AES and other symmetric encryption algorithms
Quantum Threat: Grover's Algorithm offers a quadratic speedup in brute-force searches, which impacts symmetric encryption such as AES. While it does not completely break AES, it reduces its security level, primarily exposing it to information disclosure threats.
Risk Assessment for AES 128:
- Likelihood in 15 years: Medium
- Impact: High (If the quantum security strength is reduced below 64 bits, AES 128 may become insecure.)
- Risk: Medium
Risk Assessment for AES 256:
- Likelihood in 15 years: Medium
- Impact: Low (AES 256 will remain secure with Grover's algorithm due to its higher security strength.)
- Risk: Low
Mitigation Strategies: Increase key sizes for AES (AES 256 remains secure with Grover’s algorithm), or consider transitioning to post-quantum alternatives for high-security applications.
3. Hash Algorithms
Algorithms Affected: SHA-256, SHA-512, and other hash algorithms
Quantum Threat: Grover’s Algorithm reduces the effective bit strength of hash functions, accelerating attacks such as collision finding and pre-image attacks. For SHA, this leads to risks like spoofing, tampering, and information disclosure.
Risk Assessment for SHA-256/SHA3-256:
- Likelihood in 15 years: Medium
- Impact: Medium (Quantum security strength reduced below 128 bits but above 63 bits.)
- Risk: Medium
Risk Assessment for SHA-384/SHA-512/SHA3-512:
- Likelihood in 15 years: Medium
- Impact: Low (The larger bit sizes provide greater security even against quantum threats.)
- Risk: Low
Mitigation Strategies: Use larger hash functions (e.g., SHA-512 or SHA3-512) to ensure sufficient security.
Quantum-Resistant Solutions and Migration Options
Three main approaches are explored to secure data against quantum threats: Post-Quantum Cryptography (PQC), Quantum Cryptography, and Hybrid Approaches.
-
Post-Quantum Cryptography (PQC): NIST has standardized PQC algorithms, such as lattice-based cryptography and hash-based signatures, to secure data against quantum threats. These algorithms are compatible with classical systems, though some may face performance challenges in high-performance applications.
-
Quantum Cryptography: Quantum cryptography offers highly secure communication using quantum mechanics, making it immune to quantum attacks. However, it requires specialized devices, lacks support for digital signatures, and is limited in speed and distance.
-
Hybrid Approach: The Hybrid Approach combines classical and quantum-resistant algorithms, ensuring backward compatibility during the transition to quantum-safe systems. While offering dual security, it introduces increased computational overhead, higher storage, and bandwidth requirements.
Conclusion and Recommendations
Quantum computing poses a significant threat to classical cryptography, and organizations must prepare for its impact. The NIST Cybersecurity Framework and STRIDE model provide effective risk assessment and mitigation strategies. Key recommendations include staying updated on quantum threats, transitioning to post-quantum cryptography once NIST standards are finalized, using a hybrid approach for transitional security, and planning for quantum-safe migration. By preparing now, organizations can ensure the resilience of their cryptographic systems in the face of quantum advancements.
References
[1] NIST (2017). Post-quantum cryptography.
[2] Mosca, M., & Piani, M. (2024). Global Risk Institute: Quantum Threat Timeline Report 2024.
Edited By: Windhya Rankothge, PhD, Canadian Institute for Cybersecurity
Related Blogs: Cryptography Libraries: Traditional vs. Quantum-Resistant Solutions , Advancing Cryptographic Agility: Embracing Hybrid Approaches for the Quantum Era