
Secure Your Organization with Social Engineering Pen Testing
Are you struggling to keep up the security pace of your organization? If so, this article is for you! In today's era of rising global cybersecurity threats, Social engineering tests can prove beneficial for companies to stress-test their weakest links and resolve any underlying issues to avoid security breaches. One of the practical techniques is penetration testing (also known as "pen testing").
WHAT IS PENETRATION TESTING?
Penetration testing, also known as ethical hacking, is a direct test of software systems, hardware, websites, resources, including employees and assets of an organization. It helps to identify security weaknesses by exploiting them before the attackers. It is a defensive measure taken by organizations to boost their security. Penetration testing involves simulating an actual break-in by attackers.
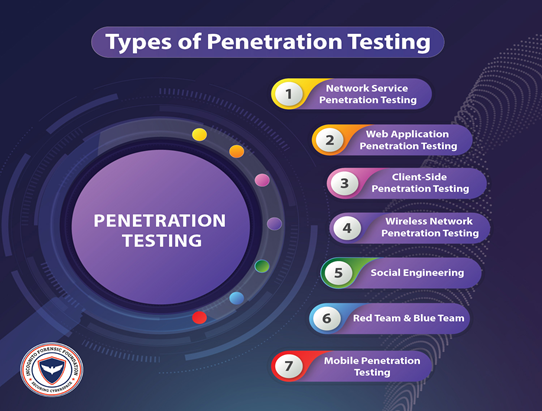
There are different methods to carry out penetration testing. The one that we'll be focussing on in this article is the social engineering test, keeping in mind that the significant aspect of cybersecurity are humans, and unsuspecting employees can be used to take data and use them for malicious intents.
SOCIAL ENGINEERING ATTACKS
Social engineering can be defined as manipulating someone to disclose classified or confidential information that can be used for unlawful purposes. It refers to the wide range of malicious attacks carried out through interaction with humans. These attacks can happen anywhere, online as well as in-person. Psychological data is used to manipulate and exploit people. As much as 98% of cybercrime attacks involve this method. Social engineering attacks at some points have targeted a staggering figure of 43% of IT professionals.
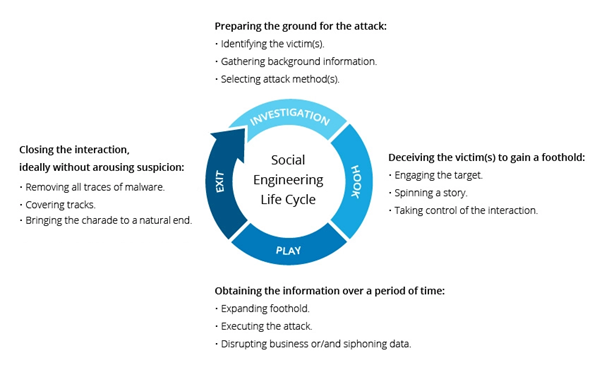
Social engineering attacks generally consist of a four-step life cycle. The first step involves preparation for the attack, including victim identification and gathering information. The second step is based on deception through target engagement. In the third step, the attacker expands their foothold and finally gains access to information used to execute the attack. In the final stage, the attacker makes sure to exit without leaving any suspicion by covering their tracks and removing traces of malware.
WHAT ARE SOME SOCIAL ENGINEERING ATTACK TECHNIQUES?
Just like other cyber threats, social engineering has various forms which are ever-evolving. Here we have discussed some of the techniques a social engineer uses to carry out these attacks and some red flags to avoid becoming a victim.
1- Phishing:
Phishing is a social engineering attack involving emails or other forms of communication such as text messages, calls, etc., to lure users into giving up sensitive information or opening malware.
- Spear-phishing attacks target specific individuals or organizations. They are specifically designed to get a particular target to respond.
- Vishing, also known as "voice phishing", occurs through phone calls and tricks users into giving sensitive and personal information or falling prey to scams
- Smishing is SMS phishing. It involves sending out text messages to gain information
2- Scareware:
Scareware manipulates users into downloading or accessing malware-infested software. It uses pop-up ads redirecting users to malicious websites or links.
3- Impersonation:
This technique involves the attacker pretending to be some trusted contact. For example, the attacker may pretend to be a company's executive and fool the victim into giving up important data or making financial transactions.
4- Dumpster diving
Dumpster diving involves going through an individual's trash and other items insight to gain access to sensitive information, including passwords, financial news, and important data that could be used to attack computer networks.
5- USB drop:
In a USB drop attack, attackers leave a USB with malicious code lying around for victims to plug into their computers. This results in the users' computers being infected by viruses and helps gain access for the cybercriminal.
6- Tailgating:
Tailgating is also known as piggybacking. This refers to any unauthorized person following an authorized person, either forcefully or accidentally, to access confidential data and documents.
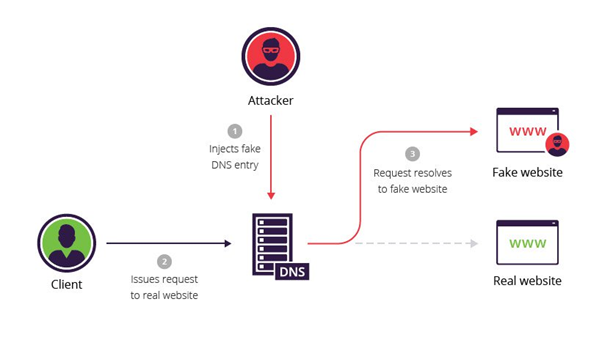
7- DNS spoofing:
This attack technique involves redirecting users to fraudulent websites that are made to look real by using altered Domain Name Server records.
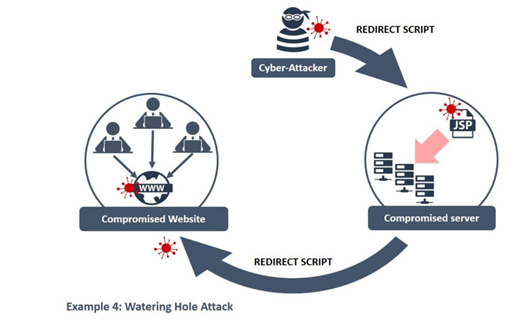
8- Watering hole attacks:
In this strategy, the cybercriminal figures out the websites and links commonly opened by an individual or organization and infect them with viruses.
WHY SHOULD YOU PERFORM SOCIAL ENGINEERING TESTING?
Now that we have identified some common types of social engineering attacks, we know that users are supposed to be the weakest links in the company. Therefore, it is important to check which users are susceptible to falling prey to the aforementioned attacks. It is necessary to discuss types and methods of social engineering penetration tests to identify the vulnerabilities and reciprocate them before being exploited by cybercriminals.
Vigorous on-site and off-site testing should be performed to identify all weaknesses and loopholes.
ON-SITE TESTING
On-site testing includes tests performed to identify physical security loopholes of organization setups and employee handling. In addition, on-site testing includes simulating attacks such as tailgating, USB drops, impersonation, and dumpster diving.
OFF-SITE TESTING
Off-site tests are conducted remotely and test user cybersecurity awareness. Off-site setting includes phishing attacks, scareware, DNS spoofing, and watering hole attacks.
METHODS INVOLVED IN SOCIAL ENGINEERING PEN TESTING
1. Information Gathering:
Information gathering can be conducted through various methods like active reconnaissance. You gather information while engaging with the person directly. Passive reconnaissance can gather information indirectly, often through social media websites where the victim is usually socializing.
2. Careful Selection of Victims
Now the most important step is selecting the vulnerable victims. They have little knowledge of these attacks and have important data in hand that can be handed to malicious users easily. These users are either recently fired mistreated employees, or employees who have posted reviews of the company on Glassdoor or other websites, where pay, environment, and reviews are public for everyone to see.
3. Victim engagement
The goal here is to engage with victims using active and passive reconnaissance and without raising any alarms. In this way, you get more information about your subjected victims and plan directed attacks towards them.
STEPS INVOLVED IN SOCIAL ENGINEERING PEN TEST:
Carrying out a social engineering penetration test is a multi-step procedure involving:
- Test planning
- Open-source intelligence gathering
- Vector identification
- Penetration attempts
1. TEST PLANNING
This is the first and one of the most important steps to ensure the proper execution of any social engineering test. It involves planning how the test will be carried out and defining the scope.
Test planning is usually carried out systematically in a meeting between the company executives and the person carrying out the test. It is best to involve a minimum number of people in the meeting to keep the testing confidential and fair. The scope of the methods and attacks is clearly defined in a contract to record that all testing performed is legally authorized.
2. OPEN-SOURCE INTELLIGENCE GATHERING
Before carrying out any tests, data is collected to familiarise with targets under testing. Data is collected through research and survey as well as through open sources publicly available.
3. VECTOR IDENTIFICATION
This step involves mentioning the social engineering techniques that will be deployed along with linking them to specific related groups. Some examples are:
- Testing security guards using impersonation and tailgating techniques to see if they can catch the person impersonating someone else while entering the building
- People from the accounts department can be tested using a phishing test. Malicious emails will be sent out requesting financial information to see if they fall prey to them and give out the confidential data
4. PENETRATION ATTEMPTS
This step involves executing the test based on the defined scope and plan. It is necessary to properly document all the findings in a report for evidence.
The evidence can be collected in the form of recorded phone calls, hidden camera videos, and mailing history.
5. REPORTING
Reporting includes all evidence, vulnerabilities found, and recommendations for alleviation. In addition, remedies for mitigation are thoroughly discussed in the final report.
6. FOLLOW-UP
After the initial testing and reporting are carried out, the company is given some time to work on their issues and resolve them according to the recommendations. Then, another test is conducted after the said time has elapsed, and the same cycle is followed till the maximum shortcomings are addressed.
To avoid falling prey to social engineering attacks, companies should train their employees and conduct awareness seminars addressing all red flags. Social engineering tests can prove beneficial for companies to stress-test their weakest links and resolve any underlying issues to avoid security breaches. It is essential to maintain the confidentiality of these tests while they're being carried out to ensure maximum transparency.