
The Three Most Sophisticated Phishing Attacks
The blog discusses the definition of phishing and the most popular three sophisticated phishing attacks.
Phishing Definition
Phishing is a type of social engineering in which an attacker designs a well-crafted message (email, chat, voice, attachment, etc.) to fake a human victim into deploying malicious content (script, application, etc.) or reveal highly sensitive information.
Unquestionably, phishing is by far the most prominent type of attack performed by threat actors.
Types of phishing and counter measurements
There are dozens of phishing types that attackers use. In the following, we are presenting the most known three types of phishing attacks.
 Email Phishing
Email Phishing
Email phishing is the most effective and known type of phishing attack. Malware authors and malicious actors send emails to advise a victim to take action by using social engineering techniques. Sometimes, even highly skilled cybersecurity professionals can fall into phishing attacks if they are well crafted.
How to anticipate Email phishing:
- Use a sense of urgency:
Most phishing emails use a sense of urgency to develop a quick response from the victim. (For instance: an attacker employs a Facebook login page and asks the user to navigate to that page and in between asks for critical password change scenarios). The below figure demonstrates an attacker scenario.
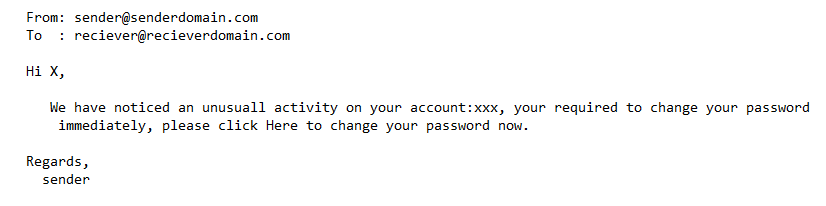
- Downloadable files:
Downloadable files, by all types, can be potentially dangerous to the user machine. Having an attachment within an email requires an isolated and secured environment to navigate. Sometimes a trustable sender (e.g., your brother, niece, or your friends, etc.) machine could be compromised, and an attacker is initiating or creating a phishing e-email on behalf. The below figure demonstrates the attachment attack.
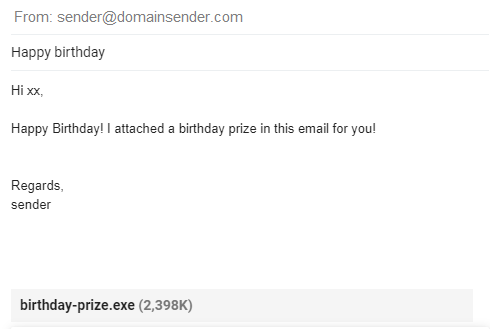
- Trusted emails:
It can be helpful sometimes to understand the domain sender to trust the sender. However, spoofing emails is widely used. See here for more information about spoofing emails.
 Vishing
Vishing
A common phishing technique employs voice for deceiving the victim into information theft or compromise. Usually, this type of attack targets online banking and other financial advantages.
How to anticipate a vishing attack:
- Use a sense of urgency:
A caller will ask for an urgent response via calling (e.g., caller: your bank account was compromised and requires immediate actions, please provide me with your full name, address, bank account details, and your social insurance number.)
- The caller asks for personal information:
A caller usually will ask for confidential personal information, such as birth date, address, social insurance number, etc.
 Whaling
Whaling
Also known as CEO fraud. It is a type of phishing where cybercriminals masquerade at a senior level in a company and direct other seniors or managers to perform immediate actions, such as financial transfer.
How to anticipate a whaling attack:
- Spoofing email:
Email spoofing is widely spread, and such an attack is extremely catastrophic due to the amount of trust gained from the sender that appears genuine. See here for more information about spoofing emails.
- Bank transfer request:
Whaling usually employs urging the victim to execute a financial transfer to gain economic interests.
- Sophisticated attack:
Attackers initiate advanced techniques to compromise the victim machine (e.g., SIM swap scam)