
Securing Modern Digitized Supply Chains
The use of recent disruptive technologies such as blockchain networks, cloud computing infrastructure and machine learning has made the supply chains more effective and efficient, but exposed them to different cyber vulnerabilities. Securing modern supply chains has become an essential, but a complicated task, with attacks such as SolarWinds.
Every product and service in modern-day markets gets involved with a set of stakeholders such as suppliers, manufacturers, customers, and service providers before they are delivered as a final product or a service. Stakeholders span multiple geographical areas, where collaboration is required for them to manage the supply chain. Therefore, modern Supply Chain Management (SCM) is often achieved through different digital services such as IT systems, networks, and software.
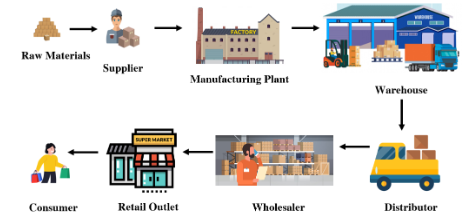
General overview of the supply chain [1]
Even though digitization has improved the efficiency and accuracy of SCM process, it also exposes the supply chain to several cyber threats such as information security threats, network security threats, and software security threats. SolarWinds in 2020 and Kayesa in 2021 attacks are considered as largest supply chain attacks in the recent past that exploited software vulnerabilities of the supply chains. Around 18,000 organizations and government entities that were using SolarWinds’s Orion software were infected. Their sensitive information related to user IDs, passwords, financial records, and source code was exposed to the attackers. Also, around 1500 companies that were using Kaseya VSA software got affected. In this attack, cybercriminals demanded a ransom of 70 million dollars from Kaseya.
As shown in Table 1, there are several ways to compromise supply chains, such as malware infection, social engineering, software or configuration vulnerabilities, and brute force attacks [2].
|
Attack Types |
Examples |
Purposes |
|
Malware Infection |
Virus, Worms, Trojan, Ransomware |
Gain unauthorized access to system and information |
|
Social Engineering
|
Phishing, Spear phishing, Whaling, Spam |
Impersonation and convincing the victim to carry out a task |
|
Brute-Force Attack
|
Password Attacks |
Guess login information and gain unauthorized access |
|
Code Injection
|
SQL injection, Buffer overflow |
Gain unauthorized access and execute unauthorized commands |
|
Misconfiguration |
Misconfigured devices/operating systems |
Gain unauthorized access and execute unauthorized commands |
|
Physical Attack |
Counterfeiting, Theft, Tampering |
Modify/destroy hardware |
Table 1: Supply Chain Attacks
Security breaches can happen at different points of the supply chain such as raw materials, suppliers, production, distribution, customer, and marketplace. Therefore, the main objective of supply chain security is to identify, analyse and mitigate the security threats that would affect the operations of the supply chain. The European Union Agency for Cybersecurity (ENISA) provides recommendations for suppliers and customers to ensure that the supply chain of products and services complies with cybersecurity practices [3].
Recommendations for suppliers:
-
Ensure that the infrastructure used to design, develop, manufacture, and deliver products, components, and services follows cybersecurity practices.
-
Implement a product development, maintenance, and support process that is consistent with commonly accepted product development processes.
-
Monitor security vulnerabilities reported by internal and external sources that include used third-party components.
-
Maintain an inventory of assets that includes patch-relevant information.
Recommendations for customers:
-
Identify and document suppliers and service providers.
-
Define risk criteria for different types of suppliers and services such as supplier & customer dependencies, critical software dependencies, and single points of failure.
-
Monitor supply chain risks and threats.
-
Manage suppliers over the whole lifecycle of a product or service, including procedures to handle end-of-life products or components.
-
Classify assets and information shared with or accessible to suppliers and define relevant procedures for accessing and handling them.
References:
[1] Rashid Hussain Khokhar, Windhya Rankothge, Leila Rashidi, Hesamodin Mohammadian, Brian Frei, Shawn Ellis, Iago Freitas, Ali Ghorbani, “A Survey on Supply Chain Management: Exploring Physical and Cyber Security Challenges, Threats, Critical Applications, and Innovative Technologies”. International Journal of Supply and Operations Management, 2024
[2] European Union Agency for Cybersecurity, “Threat Landscape for Supply Chain Attacks”, https://www.enisa.europa.eu/publications/threat-landscape-for-supply-chain-attacks.
[3] European Union Agency for Cybersecurity, “Understanding the increase in Supply Chain Security Attacks”, https://www.enisa.europa.eu/news/enisa-news/understanding-the-increase-in-supply-chain-security-attacks.