
Cuckoo Sandbox for Malware Analysis
In this blog, I am going to discuss malicious software (Malware) analysis and will reference Cuckoo sandbox as a malware analysis software that enables an analyst to accomplish a malware analysis task.
There is an increasing rate of using Malware by cybersecurity attackers to infect targeted systems which in turn makes the analysis of malware a necessity for security analysts. For instance, worms are a family of malware that exploit vulnerabilities to expand their infection and they perform malicious operations such as stealing users’ confidential information [1]. Gamarue is a worm that acts as a distributor of other malware (e.g. clickers, downloaders, etc.) after infecting a targeted system [1]. Therefore, a security analyst needs malware analysis to acquire knowledge about how the attackers think and act and it is required that the analysts have advanced technologies and tools to analyze malware. A sample of the technologies that are helpful to analysts will be discussed further.
A sandbox helps security analysts examine a malware in an isolated environment and monitor the malware’s activities. Cuckoo sandbox [2] is an instance of an open source security sandbox. Cuckoo sandbox supports various operating systems such as Microsoft Windows operating system, Android, etc. and allows for analysts to conduct an automated malware analysis [2]. After submitting a sample of malware for the analysis, Cuckoo sandbox executes the malware in an isolated environment and generates a helpful report which is used for analyzing malware behavior [2].
Cuckoo sandbox has two main components, a host and a guest virtual machine. These components need to be configured during the installation of the sandbox, and before running sample of malware. After the installation, the analyst can submit a sample of malware analysis request from the host and Cuckoo sandbox will execute the malware inside of the guest virtual machine (VM). The analyst may submit a malware analysis request from a host which is running Linux operating system into a guest VM which is running Windows operating system, if the malware requires to execute in Windows operating system.
When a malware executes in an infected system, the malware may impact various components of the system. Memory-based malware try to access contents of RAM to steal and compromise user’s confidential information and network-based malware compromise the incoming and outgoing network traffic. Therefore, it is necessary that a sandbox addresses various types of malware analysis such as memory and network analysis.
Cuckoo sandbox supports the memory analysis and enables the analyst to extract potential traces of execution of malware, from RAM. It also provides the analyst the capability to acquire a dump from network traffic for further analysis. For the memory analysis it employs the Volatility framework and for acquiring an image from the network traffic it uses tcpdump [3]. If you are interested in further information, please visit [4].
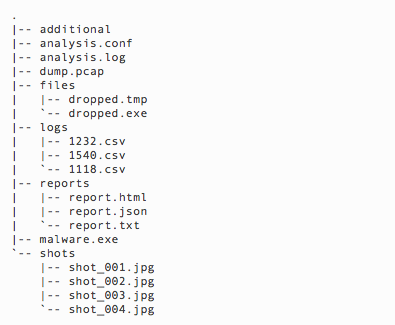
Figure 1: A sample of analysis results[5]
The Volatility framework contains different kinds of plugins for examining the content of RAM. For example, it provides the list of running processes when a malware is running on the infected machine. Thus, the analyst can examine potential processes that were executed by the installed malware on the infected system and even identify the directories that malware use for the installation or even logging user’s information for further malicious usages.
When an instance of analysis in Cuckoo is completed, Cuckoo generates a set of results. Figure 1 represents a sample of these results. Cuckoo generates directories and files that are related to the analysis such as ‘files/’ (generated or removed files by malware), ‘additional/’ (generated files by other means except the malware), ‘dumped.pcap’ (the dumped network traffic), ‘shots/’ (the screenshots during the analysis), ‘reports/’ (the abstract reports by Cuckoo), and ‘logs/’ (behavioural tracing information about monitored processes), etc [5].
Cuckoo also provides a set of configuration files for the analyst to customize for further analysis. It also provides informative documents to help users during the installation and customization of an instance of sandbox.
In conclusion, the technology of sandbox for malware analysis is an important aspect that security analysts need to apply during their analysis tasks to understand how malware operates. Cuckoo sandbox is a promising software that provides an isolated environment for malware analysis and enables security analysts to accomplish their analysis.