
Can we trust an autopilot?
As with all networked computing devices, increased connectivity often results in a heightened risk of a cybersecurity attack. Vehicles are currently being developed and sold with increasing levels of connectivity and automation. After all, people’s lives depend on the proper functioning of the system[1].
Increased automation exacerbates any risk by increasing the opportunities for the adversary to implement a successful attack. Several companies, such as Tesla, equipped their product with autopilot. A perfect autopilot depends on how perfect and accurate the car sensors are. Autopilot requires the use of many sensors to detect information in the surrounding environment, categorize information according to some predetermined or learned criteria, and make predictions about potential vehicle activity.
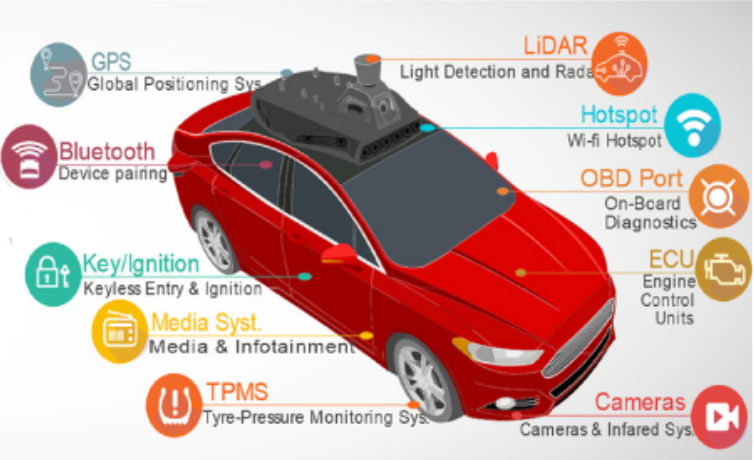
Fig.1. Autonomous vehicle navigation component [2]
The main issue that autopilot manufacturers must address is guaranteeing reliability and safety. After all, people’s lives depend on the proper functioning of the system. Unfortunately, not all automotive companies are closely monitoring the research of cybersecurity experts. Sometimes, even publicly disclosed vulnerabilities remain unpatched for years. Fig (1) shows the car sensors that are the main component of the autopilot system and they can be considered as the attack surface.
Several types of attacks can be used to which are as follows:
- A GPS-spoofing attack on the car (GPS) receiver could easily be carried out wirelessly and remotely, exploiting security vulnerabilities in mission-critical telematics, sensor fusion, and navigation capabilities. Such attack may make autopilot navigation steers car off road [3].
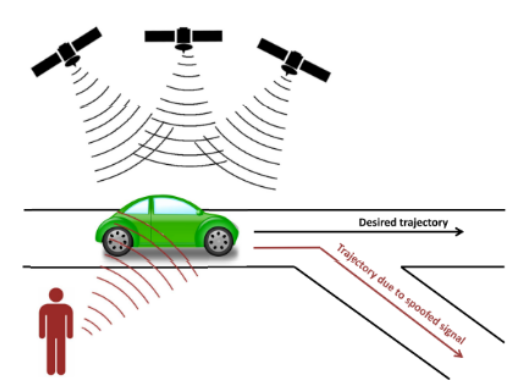
GPS spoofing attack [1].
- The jamming of GPS is a more primitive and simplistic attack. In comparison with spoofing, jamming only requires that enough radio noise on the GPS frequency (1575.42 MHz) is transmitted to prevent authentic signals from being distinguishable by the GPS receiver.
-
Engine control sensors are used to acquire data to regulate engine activity. This includes sensors such as; temperature, air flow, exhaust gas, and engine knock and are all used to acquire performance data which is used to adjust engine conditions. As connectivity increases, care needs to be taken to ensure that these primitive sensors are not vulnerable[1].
-
Tire-pressure Monitor Systems (TPMS) are ‘direct’ small devices that are located on the valve of each tire and frequently update the vehicle’s control system with tire specific information. Direct TPMS devices operate by transmitting data to one of the vehicle’s control units on general purpose (i.e., 315, 443 and 866 MHz) frequencies using either Frequency Shift Keying (FSK) or Amplitude Shift Keying ASK) to prevent spoofing. However, Ishtiaq Rouf et al. demonstrate that the signals can be identified and modified using packet sniffing techniques at a range of 40m [4].
-
Light detection and Ranging (LiDAR) sensors are used to generate a map of the vehicle’s environment for localization, obstacle avoidance, and navigation. Work conducted by Stottelaart [5] demonstrates the potential for jamming LiDAR by directly emitting light back at the scanner unit which is of the same frequency as the laser reflecting on the target[1].
-
Password and key attacks are where security restriction mechanisms are continuously tested using different values to see if they can be compromised.
-
Denial of Service attacks are where the normal service of a system is disrupted either by a single or multiple attacking machines. Different types of DoS attacks can be performed by overwhelming 1) a single network node, 2) vehicle to vehicle (V2V), or 3) vehicle to infrastructure (V2I) . All these attacks are damaging and aim to disrupt the infrastructure[1].
-
Network protocol attacks are where communication protocols are analyzed to identify potential exploitation mechanisms. In the absence of confidentiality protection, an attacker can read all data sent bus, as well as send spoofed packets, which can modify vehicular behavior.
-
Rogue updates are where software running on a vehicle’s ECUs is updated with software that was not produced by the manufacturer and has hidden vulnerabilitie
A successful attack of this kind would be confined to a singular vehicle only. However the connection mechanisms which supports the communication between vehicles and infrastructure; enables cyber-attacks to be carried out over wireless networks. A more advanced techniques are required to increase the level of trust in self-driving cars.
Ref:
1- Parkinson, S., Ward, P., Wilson, K., & Miller, J. (2017). Cyber threats facing autonomous and connected vehicles: Future challenges. IEEE transactions on intelligent transportation systems, 18(11), 2898-2915.
2- Sheehan, B., Murphy, F., Mullins, M., & Ryan, C. (2019). Connected and autonomous vehicles: A cyber-risk classification framework. Transportation research part A: policy and practice, 124, 523-536.
3- Tesla Model S and Model 3 Prove Vulnerable to GPS Spoofing Attacks as Autopilot Navigation Steers Car off Road, Research from Regulus Cyber Shows. [Online]. Available:https://www.prnewswire.com/il/news-releases/tesla-model-s-and-model-3-prove-vulnerable-to-gps-spoofing-attacks-as-autopilot-navigation-steers-car-off-road-research-from-regulus-cyber-shows-300871146.html
4- Rouf, I., Miller, R. D., Mustafa, H. A., Taylor, T., Oh, S., Xu, W., ... & Seskar, I. (2010, August). Security and Privacy Vulnerabilities of In-Car Wireless Networks: A Tire Pressure Monitoring System Case Study. In USENIX Security Symposium (Vol. 10).
5- B. G. Stottelaar. (Feb. 2015). Practical Cyber-Attacks on Autonomous Vehicles. [Online]. Available: http://essay.utwente.nl/66766/