
Security of Distributed Energy Resources: Data Integrity Attack Targeting Offshore Wind Farms
This blog highlights the cybersecurity risks of Distributed Energy Resources (DER) like wind and solar power. It discusses vulnerabilities in communication networks, focusing on a data integrity attack targeting offshore wind farms, which can destabilize grids and cause economic losses. The blog emphasizes the urgent need for enhanced security in DER systems to protect modern energy infrastructure.
Distributed Energy Resources
Distributed energy resources (DER) play a crucial role in modern smart grid environments. Renewable energy sources like wind, solar, and thermal power have been increasingly utilized in power generation to enhance energy efficiency and comply with carbon emission standards. The cumulative DER capacity in the United States is projected to reach 387 gigawatts by 2025, as highlighted in our inaugural comprehensive DER outlook report [1]. The cumulative DER capacity additions by resource and customer type are illustrated in Figure 1. The DER landscape in the U.S. is undergoing significant diversification, moving away from its previous reliance on nonresidential load management, which constituted two-thirds of the new DER capacity in 2015 but is expected to represent less than half by 2025. The report reveals that solar energy, electric vehicle (EV) infrastructure, and residential load management now dominate the DER landscape, collectively accounting for over 90% of the DER capacity installed between 2016 and 2025. Additionally, the cumulative DER investments in the U.S. are anticipated to surpass $110.4 billion from 2020 to 2025. The growth in solar, EV infrastructure, battery storage, and grid-interactive water heaters is expected to drive spending to unprecedented levels by 2025. The expansion of distributed energy resources (DER) is not limited to the United States; it is a global technology growth, with countries around the world actively driving significant growth in this sector.
In nature, DER has a complex and decentralized architecture. This decentralization of power generation and the digitization of control and monitoring strategies make the DER systems more complex and vulnerable. The nature of the data-driven communication networks used in DER systems expands the attack vectors towards the grid. Any attack which occurs in DER systems has the potential to cause severe damages such as sudden electricity fluctuation which make the entire grid unstable and amplifies up to sudden blackouts.
Thus, the security of these DER-integrated cyber-physical systems is essential for a reliable and resilient energy grid. The importance of addressing the cybersecurity of DER systems has significantly increased due to the new interconnection and interoperability standards. IEEE Standard 1547 requires DER devices to be accessible remotely for monitoring and control and interoperability standards require DER devices to communicate and seamless operations together. Remote monitoring and controlling capabilities allow remote users to modify or intervene in the behavior of DER devices. While these standards add sophisticated features to the systems they vastly increase the attack surface and cybersecurity is more challenging. Since DER communications mostly occur over public and insecure private networks, the integration of DER devices drastically increases the impact towards the grid as well. Although individual DER devices have limited active and reactive capacities and employ minimal impact on the grid, their collective influence is a significant portion of the grid’s generation capacity.
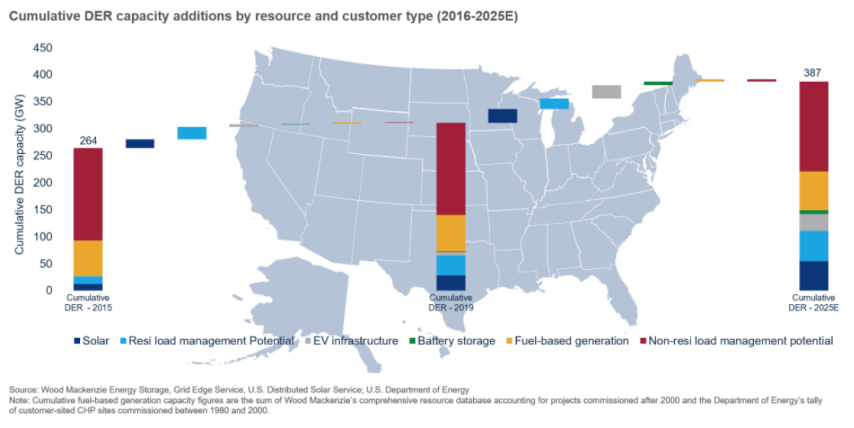
Figure 1: Cumulative DER Capacity Additions by Resource and Customer Type [1]
Attacks on DER communications could lead to severe disruptions in grid stability, causing voltage and frequency imbalances, power outages, and potentially damaging equipment both on the grid and at customer premises. Such attacks could also undermine energy reliability and resilience, leading to cascading failures across interconnected networks and substantial economic and operational impacts on the power system.
A Data Integrity Attack Targeting VSC-HVDC-Connected Offshore Wind Farms
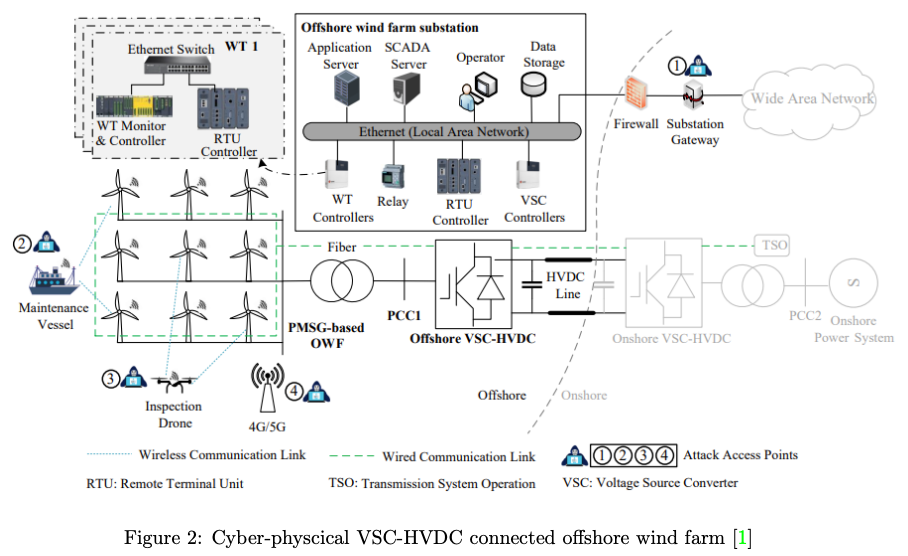
Chen et al. [2] Concordia University, and Hydro-Quebec recently exploited a critical vulnerability in an offshore windmill. Offshore wind farms, especially those utilizing the cost-effective VSC-HVDC connections, rely heavily on complex communication networks. These networks connect the wind farms to the mainland grid, manage communication between turbines, and facilitate interaction with maintenance crews and drones. Unfortunately, this intricate system creates multiple entry points for cyberattacks.
The study identifies a potential attack scenario where malicious actors could infiltrate the wind farm’s local area network and manipulate sensor data. This tampered data could lead to electrical disturbances within the wind farm itself. With all turbines operating at maximum capacity, these disturbances could trigger poorly controlled power oscillations. If the attackers can manipulate the timing and frequency of these disturbances, they could amplify the oscillations and potentially destabilize the entire power grid.
Such a targeted manipulation could also result in severe impacts on the wind farm’s energy output, reducing its efficiency and reliability and potentially causing significant economic losses. Additionally, by compromising data integrity, attackers may erode trust in automated monitoring and control systems, resulting in increased manual oversight and slowing response times during critical events. Ultimately, the lack of adequate security measures in this interconnected system underscores the risk of severe and potentially cascading failures, highlighting the urgent need for enhanced cybersecurity in offshore wind energy infrastructure. Existing redundancies may not be sufficient to protect against such cyber-induced disruptions.
Impact of the Attack
The offshore VSC (Voltage Source Converter) is used as the synchronization source, supporting the regular operations of the offshore wind farm (OWF), which itself functions as a passive network. Through data integrity attacks, the proposed attacks reduce the control effectiveness of the VSC at the primary connection point (PCC1), causing disruptions in the wind farm’s normal functionality. This disruption exhausts the system’s damping capability which causes problems in controlling oscillations. As these oscillations intensify beyond acceptable limits, the stability of the system is compromised, risking both physical damage to equipment and tripping of protection devices.
In extreme cases, these attacks could cause the entire OWF to trip. Given that power systems typically operate with optimal dispatch, this sudden drop in power generation disrupts the balance, leading to financial losses. Additionally, attackers could target multiple OWFs simultaneously. For power systems with significant wind generation, the loss of high-capacity OWFs would create a severe power imbalance, potentially triggering widespread instability throughout the grid.
Need for Security in DER
With the drastic growth of DER, the traditional power grid is going through a revolutionary change in many aspects. The traditional utility-centric architecture is moving towards a distributed smart grid with the deployment of DER. Integration of new energy resources is decreasing the control of automation which utilities had earlier. Consequently, DER deployments add attack surface and risks to the smart grid due to the energy resources, access points and other related infrastructure operating beyond the conventional administrative domain [3]. Thus, the cybersecurity of DER systems is crucial for an accurate and reliable power grid.
References
[1] B. K. D. of Grid Edge Research. (2020) The next five years will see massive distributed energy resource growth. [Online]. Available: https://www.woodmac.com/news/editorial/der-growthunited-states/
[2] J. Chen, H. Du, J. Yan, R. Zgheib, and M. Debabbi, “A data integrity attack targeting vsc-hvdcconnected offshore wind farms,” in 2023 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), 2023, pp. 1–6.
[3] I. Zografopoulos, N. D. Hatziargyriou, and C. Konstantinou, “Distributed energy resources cybersecurity outlook: Vulnerabilities, attacks, impacts, and mitigations,” IEEE Systems Journal, 2023.
Edited By: Windhya Rankothge