Threat Intelligence through Cyber Deception: A Beginner's Guide to Honeypots
The blog introduces honeypots—decoy systems used in cybersecurity to lure attackers and gather threat intelligence. It explains their role in identifying attack patterns, tools, and vulnerabilities, while protecting real systems. A step-by-step guide to setting up a honeypot with tools like Cowrie, VirtualBox, and Kali Linux is provided, along with tips for further exploration.
- “Brute force attacks were the most repeated with 73,860 total number of attacking IPs.”
- “The default credentials (username: root, password: root) was counted over 5.5 million times in brute-force attempts.”
- “Port 445 and 22 were the most targeted ports, this corresponds to Windows and Linux remote administration services.” [1]
These are only a few findings of the Outpost24, a cyber threat landscape study using honeypots. In this blog post, we are going to introduce honeypots, how they are used and how to start using our first honeypot.
What are honeypots?
A honeypot is an intentionally vulnerable computer system that imitates the behaviour of a normal system to lure away the cybercriminals from legitimate servers. In other words, it is a cyber decoy system that attracts adversaries and distracts them from our main network infrastructure. While the attacker is busy attacking the fake system, i.e. the honeypot, it will generate logs from their activity and tracks every move they make. This lets cyber analysts use these logs and extract insightful information about attackers, attack trends and most common techniques.
Why use honeypots?
Honeypots can be a great source of threat intelligence from different perspectives. Honeypots can reveal attack trends and patterns during important events such as presidential elections. They can identify what tools attackers use, what attacks they are interested in and what vulnerable services they are looking for to exploit. More importantly, they can store different artifacts and Indicators of Compromise (IoC) such as malware, malicious URLs and common credentials used for brute force attacks, etc. All these information can then be processed and analyzed to form useful threat intelligence to identify, understand and respond to potential existing threats.
How to use honeypots?
From a research point of view, honeypots can be deployed to collect as much data to get more up-to-date knowledge about cybercriminals and their behaviour. On the other hand, a production honeypot can be deployed in a real enterprise network to distract potential hackers from the legitimate computer systems. In this case, to secure a specific system, organizations can deploy a replica of the system that emulates the same services. Then, they can use the collected logs to extract intel and fortify the defence mechanism for that system.
How does a honeypot look like?
From a network perspective, a honeypot looks like any other network endpoint, identified by an IP address. The adversary finds the live host and scans for open ports to see what services are available on the system. In case they find a service of interest, the adversary may choose to do a service version detection scan to find the version of the service the honeypot is running. Interestingly, the service that the honeypot is running is intentionally vulnerable, which intrigues the attacker to try and exploit the vulnerability and gain an initial access to the system. Having access to the honeypot, the attacker tries to download malicious malware and run malicious payloads to exploit the system further. In the meantime, all the activities are logged and stored in a database.
How to get started with honeypots
One of the best ways to get started with honeypots is to deploy and use the well-known Cowrie honeypot. Cowrie is a medium to high interaction SSH and Telnet honeypot designed to log brute force attacks and the shell interaction performed by the attacker. In medium interaction mode (shell) it emulates a UNIX system in Python, in high interaction mode (proxy) it functions as an SSH and telnet proxy to observe attacker behavior to another system. [2]
Most of the open-source honeypots can be easily deployed as Virtual Machines (VM). Therefore, in this step-by-step guide, we will discuss how to create an environment to run your honeypots.
- First, you need a hosted hypervisor such as VirtualBox to run your VMs [3]. It can be installed on all major Operating Systems (OS).
- Second, you need two VMs for your experimental environment, one for the honeypot and another for the attacker machine. You can use Ubuntu [4] for your honeypot and Kali Linux [5] for your attacker VM.
- Third, you need to create a NAT network on your VirtualBox and add your VMs to it [6]. Now, you have a proper setup to install and explore your honeypot.
How to use Cowrie
First, make sure you update your system using the following commands:
$ sudo apt update
$ sudo apt upgrade
Next, you need to install Cowrie on the Ubuntu VM following the documentation [7]. Then, find the IP address of your Ubuntu VM.
$ ip a
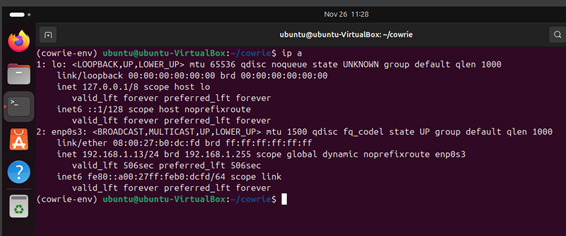
Make sure to write down the IP address. In this case, 192.168.1.13.
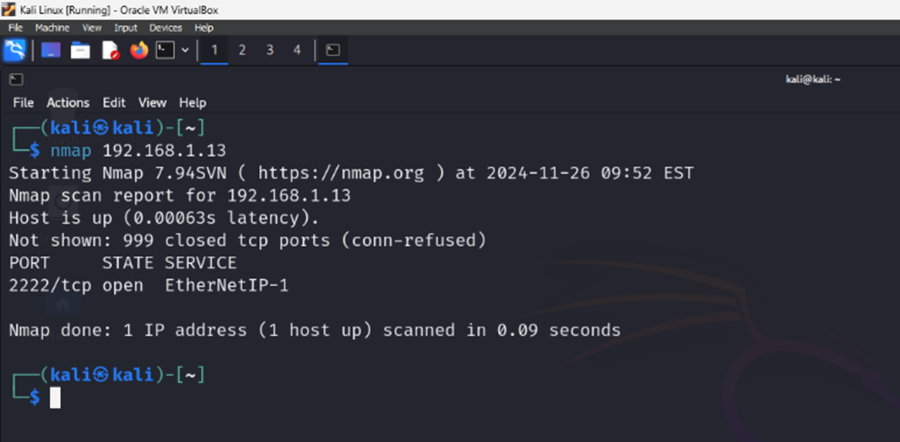
Now, you can use your Kali Linux VM to interact with Cowrie. Start by doing a simple port scan on the Ubuntu VM. We see port 2222 is open.
$ nmap 192.168.1.13
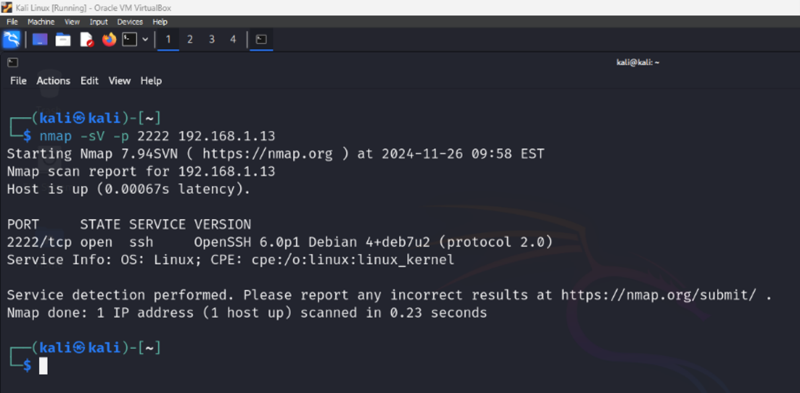
Then, do a service version detection scan that reveals the SSH protocol being served.
$ nmap -sV -p 2222 192.168.1.13
Now, download the mirai-botnet usernames and passwords database.
$ wget https://raw.githubusercontent.com/danielmiessler/SecLists/refs/heads/master/Passwords/Malware/mirai-botnet.txt
And extract the passwords from the file.
$ awk '{print $2}' mirai-botnet.txt > mirai-botnet-passwords.txt
Next, use medusa to conduct an SSH brute force attack using root as user and the extracted passwords.
$ medusa -u root -P mirai-botnet-passwords.txt -h 192.168.1.13 -M ssh -n 2222 -f
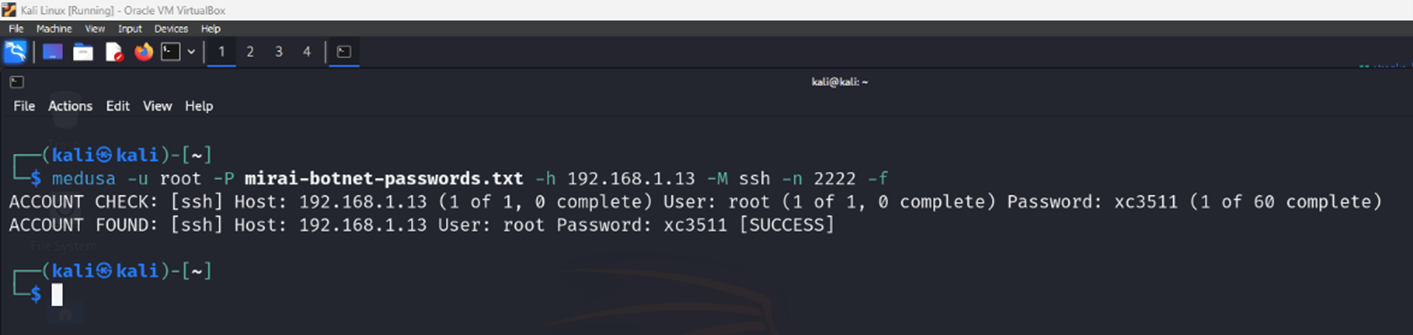
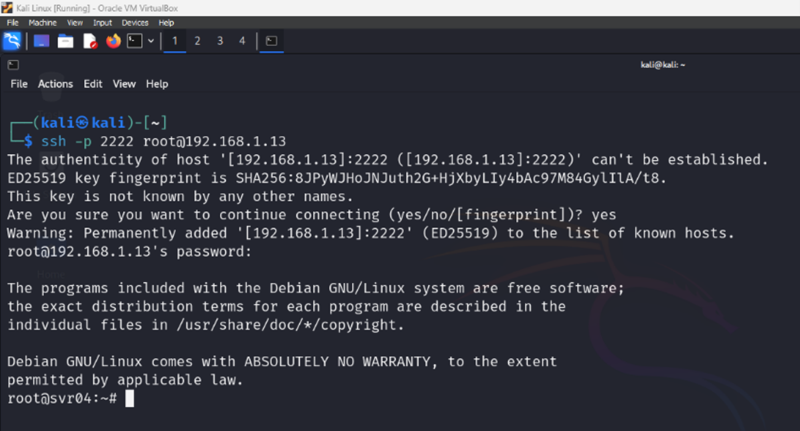
Now, use the successful credentials to login to Cowrie using ssh.
$ ssh -p 2222 192.168.1.13
Use a few initial commands to identify the user, hostname and OS information. Also, download the mirai-botnet text file to Cowrie as a sample malware. (Here we don’t want to download actual malware. We only need to see how Cowrie logs and stores the downloaded files.)
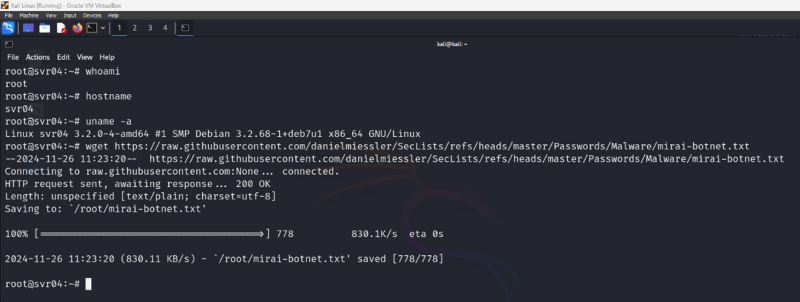
We are done with the attacker Kali Linux. Now, let’s move to Ubuntu to see how Cowrie logged our activity. First, view the log file and scroll down to see a line for each interaction or command you have run on Cowrie.
$ less var/log/cowrie/cowrie.log
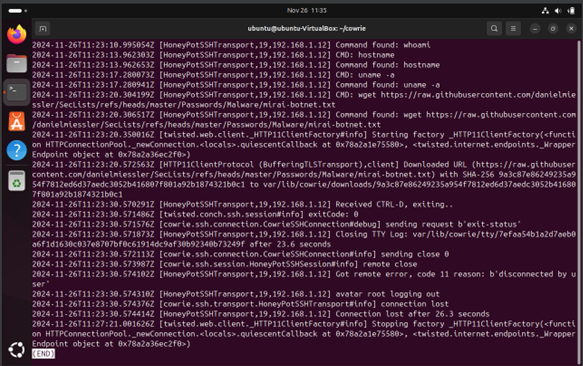
Now, view the downloaded file and its content.
$ ls var/lib/cowrie/downloads
$ tail var/lib/cowrie/downloads/<filename>
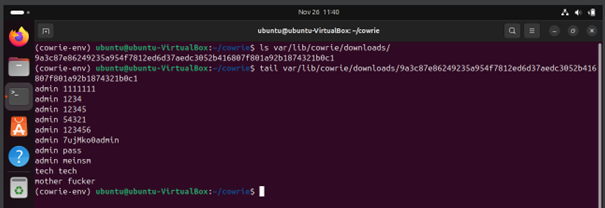
You can also explore other files for other configurations, changing the credentials, modifying the banners, etc. All files of interest are available on the Cowrie’s GitHub Website.
Next Steps
You can explore other open-source honeypots and use the same setup to deploy other projects and understand the nature of other honeypots providing different services. One great resource for this is the T-pot project [8] that introduces several interesting honeypots for a large range of services.
References
[1] https://outpost24.com/blog/honeypot-findings-from-over-42-million-attacks/
[2] https://github.com/cowrie/cowrie
[3] https://www.nakivo.com/blog/use-virtualbox-quick-overview/
[4] https://ubuntu.com/tutorials/how-to-run-ubuntu-desktop-on-a-virtual-machine-using-virtualbox
[5] https://www.kali.org/docs/virtualization/install-virtualbox-guest-vm/
[6] https://www.techbeatly.com/how-to-create-and-use-natnetwork-in-virtualbox/
[7] https://cowrie.readthedocs.io/en/latest/INSTALL.html
[8] https://github.com/telekom-security/tpotce
Edited By: Windhya Rankothge