Cryptography Libraries: Traditional vs. Quantum-Resistant Solutions
This blog explores the evolving landscape of cryptography, comparing traditional libraries like OpenSSL and libsodium with emerging quantum-resistant solutions such as CRYSTALS-Kyber and PQClean. It highlights their features, performance, and security to help developers navigate immediate and future data protection needs in an era of advancing quantum computing.
In a world where data security is paramount, cryptography is the bedrock for protecting sensitive information and securing communication. Traditional cryptographic libraries, such as OpenSSL and libsodium, are essential for encrypting data and ensuring privacy. However, the rapid advancement of quantum computing presents a challenge to these conventional algorithms. Quantum-resistant libraries, including PQClean and CRYSTALS-Kyber, are emerging to protect against quantum-based threats. This blog post explores leading libraries for both traditional and quantum security, providing a comparative analysis with illustrative charts.
Traditional Cryptography Libraries
Traditional cryptography libraries use symmetric and asymmetric cryptographic algorithms like AES, RSA, and SHA-256 to provide confidentiality, integrity, and authentication. Below are some of the most widely used libraries.
- OpenSSL:A C/C++ library with bindings for Python, Ruby, and more, OpenSSL supports SSL/TLS, AES, RSA, and digital signatures. Ideal for web servers, SSL certificates, and secure communication [10].
- Bouncy Castle:Primarily for Java and C, Bouncy Castle provides encryption, digital signatures, and algorithms like AES and RSA, perfect for enterprise and cross-platform security applications [2].
- libsodium: With a simplified API, libsodium (C/C++ with bindings for Python, JavaScript, etc.) excels in elliptic curve cryptography and random number generation, suited for embedded and cloud systems [5].
- WolfSSL: A lightweight SSL/TLS library in C, WolfSSL is optimized for IoT and real-time applications where security and low latency are key [12].
- MIRACL: Specializing in elliptic curve cryptography, MIRACL (C/C++) is popular in financial and IoT applications needing high-speed and secure encryption [6].
Figure 1 shows a side-by-side comparison of traditional cryptographic libraries based on language support, performance, and security scores: This visual highlights each library’s adaptability (languages supported), performance in speed and efficiency, and overall security level.
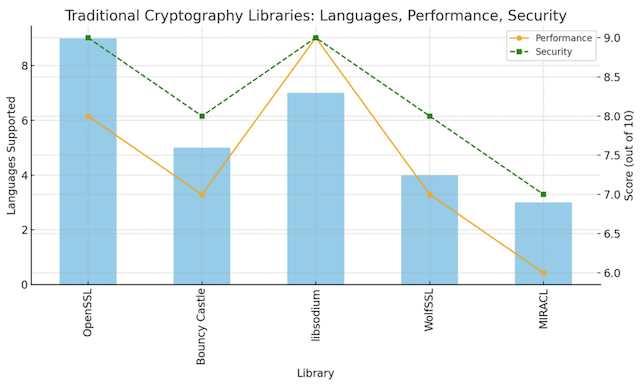
Figure 1: Comparison of popular traditional libraries like OpenSSL and libsodium, focusing on language support, performance, and security features.
Quantum-Resistant Cryptography Libraries
As quantum computing advances, so does the need for quantum-resistant cryptography. Quantum computers, capable of breaking traditional cryptographic algorithms, have spurred the development of libraries that incorporate quantum-safe algorithms.
- Open Quantum Safe (OQS): A C/C++ library featuring quantum-safe algorithms for encryption and signatures, OQS is ideal for applications that require long-term, future-proof data security [9].
- libquantum: Primarily in C, libquantum is used for simulating quantum algorithms, serving as a key tool in academic research and testing quantum-based cryptographic models [4].
- PQClean: A C library with Python bindings, PQClean provides standardized post-quantum algorithms like CRYSTALS-Kyber and NTRU, suitable for quantum-resistant security in applications and research [11].
- Sphincs+: C-based, Sphincs+ is a hash-based, quantum-resistant digital signature library, ideal for document and software signing where secure signatures are essential [1].
- CRYSTALS-Kyber: This C library provides quantum-safe key exchange mechanisms and is used for secure communications in sectors like finance and defense [7].
- FrodoKEM: FrodoKEM is a C-based, lattice-based key exchange library offering quantum resistance, ideal for applications requiring robust data protection in finance and healthcare [3].
- NTRUEncrypt: A lattice-based encryption library in C, NTRUEncrypt is designed for quantum-safe data security, commonly used in finance and government sectors [8].
Figure 2 compares quantum and post-quantum libraries based on language support, performance, and security features. This chart emphasizes the current limitations in language support but highlights the strong security capabilities essential for a quantum-resilient future:
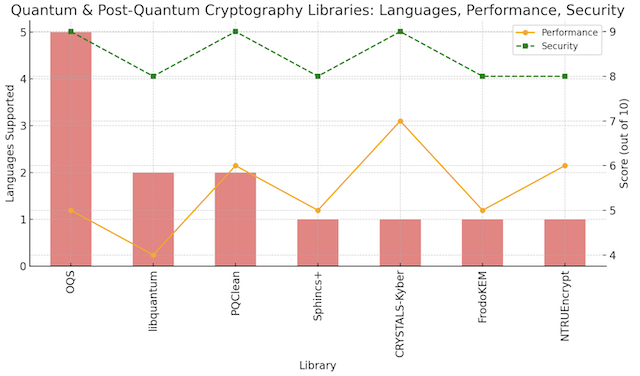
Figure 2: Comparison of quantum-safe libraries like OQS and CRYSTALS-Kyber, highlighting language support, performance, and future-proof security.
Conclusion
As technology evolves, so must the tools we use to secure it. Traditional cryptographic libraries, like OpenSSL and Bouncy Castle, offer tried-and-tested solutions for current security needs. However, with the rise of quantum computing, it is increasingly important to consider quantum-resistant options, like OQS and CRYSTALS-Kyber, to future-proof sensitive data. For developers, the choice between traditional and quantum-safe libraries will depend on both immediate security needs and long-term planning. As quantum-safe libraries become more optimized, they are likely to become essential components of secure digital infrastructure, especially in fields requiring enduring data protection.
References
[1] D. J. Bernstein et al. Sphincs+: Stateless Hash-Based Signatures for Post-Quantum Security. https://sphincs.org/. Accessed 2024.
[2] Bouncy Castle. The Legion of the Bouncy Castle. https://www.bouncycastle.org/. Accessed 2024.
[3] FrodoKEM. FrodoKEM: Learning With Errors Key Encapsulation. https://frodokem.org/. Accessed 2024.
[4] libquantum. libquantum - A C Library for the Simulation of Quantum Mechanics. https: //github.com/libquantum/libquantum. Accessed 2024.
[5] libsodium. Libsodium: A Modern, Easy-to-Use Crypto Library. https://libsodium.org/. Accessed 2024.
[6] MIRACL. MIRACL: The World’s Fastest Crypto Library. https://github.com/miracl/ core. Accessed 2024
[7] NIST PQC. CRYSTALS: Cryptographic Suite for Algebraic Lattices. https://pq-crystals. org/. Accessed 2024.
[8] NTRU. NTRUEncrypt: Public Key Cryptosystem for Quantum Safety. https://ntru.org/. Accessed 2024.
[9] Open Quantum Safe (OQS). Open Quantum Safe Project. https://openquantumsafe.org/. Accessed 2024.
[10] OpenSSL. OpenSSL Project. https://www.openssl.org/. Accessed 2024.
[11] PQClean. PQClean: Clean and Verified Post-Quantum Cryptography. https://github. com/PQClean/PQClean. Accessed 2024.
[12] WolfSSL. WolfSSL Embedded SSL/TLS Library. https://www.wolfssl.com/. Accessed 2024.
Edited By: Windhya Rankothge