
Trust No One: Why Zero Trust Is the Future of Cybersecurity
In today's digital landscape, cyber threats are becoming more advanced, rendering traditional security models inadequate for safeguarding sensitive data and digital infrastructure. Organizations can no longer depend on perimeter-based security measures that presume trust within the network [1]. Enter Zero Trust Architecture (ZTA)—a groundbreaking security framework that eradicates implicit trust and mandates continuous verification at every point of network access.
What is Zero Trust Architecture?
Zero Trust is a cybersecurity model founded on the principle of "Never Trust, Always Verify" [2]. Unlike traditional security models that inherently trust users and devices within a network, Zero Trust demands rigorous identity verification for every user, device, and application seeking access to resources, irrespective of their location—whether inside or outside the corporate network.
ZTA assumes that attackers may already be within the network and therefore, every request must be verified before granting access [3]. This proactive approach significantly reduces the risk of unauthorized access, insider threats, and lateral movement of attackers within the system.
Key Principles of Zero Trust
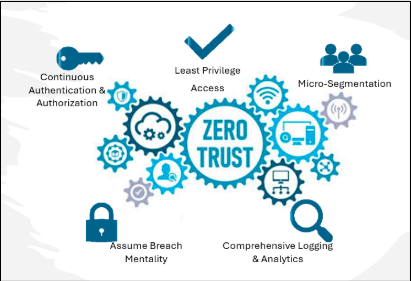
The Zero Trust security model is built on several core principles [4]:
-
Continuous Authentication & Authorization: Users and devices must be verified continuously through multi-factor authentication (MFA) and adaptive access controls.
-
Least Privilege Access: Users and applications are granted the minimum level of access necessary to perform their tasks, reducing the attack surface.
-
Micro-Segmentation: The network is divided into smaller segments to restrict unauthorized movement within the system. Even if attackers gain access, they cannot easily move laterally across the network.
-
Assume Breach Mentality: Organizations operate under the assumption that a breach has already occurred, leading to proactive monitoring, threat detection, and response mechanisms.
-
Comprehensive Logging & Analytics: Continuous monitoring and analysis of user behavior help detect and respond to anomalies in real-time.
Why is Zero Trust Important?
Zero Trust is rapidly becoming the gold standard for cybersecurity due to the evolving nature of cyber threats. Traditional network security models are based on a “castle-and-moat” approach [5], which fails to address modern attack vectors such as:
-
Insider Threats: Malicious or compromised employees can exploit trust-based models [6].
-
Remote Work & Cloud Computing: Employees accessing corporate resources from various locations create vulnerabilities [7].
-
Supply Chain Attacks: Third-party vendors and contractors introduce security risks [6].
-
Ransomware & Advanced Persistent Threats (APTs): Attackers use sophisticated methods to infiltrate networks and evade detection [6].
How to Implement Zero Trust?
Organizations looking to transition to a Zero Trust model can follow these steps:
-
Identify Critical Assets & Data: Determine what resources need to be protected and classify sensitive information [8].
-
Enforce Strong Identity & Access Management (IAM): Implement MFA, single sign-on (SSO), and strict access controls [9].
-
Adopt Network Segmentation & Least Privilege Access: Apply micro-segmentation and restrict access to only what is necessary [10].
-
Monitor & Analyze Activity in Real-Time: Use advanced security analytics and AI-driven threat detection to identify anomalies [11].
-
Automate Security Policies & Response: Utilize automated security tools for policy enforcement, anomaly detection, and incident response [12].
-
Educate & Train Employees: Foster a security-conscious culture by training employees on Zero Trust principles and cyber hygiene.
Challenges in Adopting Zero Trust
While Zero Trust offers robust security advantages, implementing it comes with challenges [13] such as:
-
Complex Integration: Legacy systems may not easily integrate with Zero Trust principles.
-
User Experience: Continuous verification may lead to friction in user accessibility.
-
Resource Intensiveness: Requires investment in new technologies and training.
-
Resistance to Change: Employees and IT teams may resist a shift from traditional security models.
Final Thoughts
Zero Trust Architecture is more than just a cybersecurity strategy; it is a fundamental shift in how organizations approach security in today’s threat landscape. By enforcing strict verification, limiting access privileges, and continuously monitoring activities, Zero Trust helps organizations stay resilient against evolving cyber threats.
As organizations increasingly move to cloud-based environments, remote work, and third-party integrations, the adoption of Zero Trust will become not just an option, but a necessity. The key to successful implementation lies in strong identity management, real-time monitoring, and a security-first mindset.
In the modern digital world, trust is a vulnerability—Zero Trust is the solution.
Reference
[8] “The Five Steps to Approaching Zero Trust.” Accessed: Mar. 30, 2025. [Online]. Available:
[12] “How to Implement Zero Trust | Zscaler.” Accessed: Mar. 30, 2025. [Online]. Available:
Edited By: Windhya Rankothge, PhD, Canadian Institute for Cybersecurity
Related Blogs: ”Trust, but verify”: Safety and Security in Critical System , Can we trust an autopilot?