Navigating Unavoidable Cyber Attacks: Insights from the American Water Incident and the Purdue Model
Cyber attacks are unavoidable. In today's interconnected world, operational technology (OT) systems are increasingly targeted by cyber adversaries. OT consists of hardware and software that control and monitor physical processes in industries like manufacturing, energy, and water treatment. Understanding the nature of these attacks, especially through frameworks like the Purdue Model, is essential for industry professionals aiming to bolster their defenses.
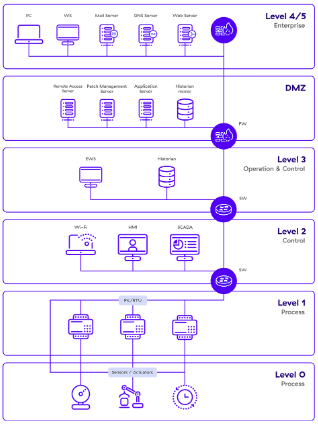
Figure 1: Purdue Model [ZScaler]
Understanding OT Attacks Through the Purdue Model
The Purdue Enterprise Reference Architecture (PERA), commonly known as the Purdue Model (Figure 1), is a hierarchical framework that segments industrial control systems (ICS) into distinct levels, each representing different operational layers:
Level 0: Physical Processes
This foundational layer includes the actual physical processes and equipment, such as sensors, actuators, and field devices that directly interact with the physical world [Fortinet].
Level 1: Basic Control
This level contains devices/microcontrollers such as Programmable Logic Controllers that provide the means to control Level 0 automatically. [Youtube].
Level 2: Supervisory Control
Monitoring and supervisory control for processes within an OT infrastructure. This includes human-machine interfaces (HMIs) and supervisory control and data acquisition (SCADA) systems [Youtube].
Level 3: Manufacturing Operations Systems
Managing production workflow to produce the desired products. This includes manufacturing execution systems (MES) and other systems that oversee production activities [Zscaler].
Level 4: Business Logistics Systems
IT networks for business users at local sites, encompassing business applications like enterprise resource planning (ERP) systems that handle business-related functions such as logistics and planning [DOE].
Level 5: Enterprise Network
Corporate-level services supporting individual business units and users, typically located in corporate data centers. This includes services like enterprise Active Directory, internal email, and document management systems [SANS].
Case Study: American Water's Cybersecurity Incident
In October 2024, American Water, the largest regulated water and wastewater utility company in the U.S., experienced a cyberattack that led to the shutdown of certain systems, including their customer billing portal. The company detected unauthorized activity on October 3 and promptly disconnected affected systems to protect customer data and prevent further harm. While water and wastewater operations remained unaffected, the billing systems were paused, and customers were assured there would be no late charges during the downtime [CBS News].
Potential Compromise Within the Purdue Model
Given the nature of the incident, it's plausible that the compromise occurred at:
Level 4 (Business Logistics Systems): The disruption of billing systems suggests that business applications, such as customer relationship management (CRM) or billing software, were targeted.
Level 5 (Enterprise Network): The need to disconnect certain systems indicates that corporate-level services, possibly including enterprise resource planning (ERP) systems or internal email, may have been affected.
Rationale Behind System Shutdowns
When a cyberattack is detected, organizations often shut down specific systems to:
-
Contain the Threat: Prevent the attacker from moving laterally within the network.
-
Protect Data Integrity: Safeguard sensitive customer and operational data from exfiltration or corruption.
-
Assess and Remediate: Allow cybersecurity teams to investigate the breach's scope and implement necessary fixes without the risk of ongoing interference.
In the case of American Water, the decision to pause billing and take the customer portal offline was a precautionary measure to ensure customer data remained secure while the incident was being addressed [CBS News].
Mitigation Strategies to Shorten Recovery Time
-
Implement Network Segmentation: Utilize the Purdue Model to segment networks, limiting an attacker's ability to traverse from IT to OT environments [Zscaler].
-
Develop and Test Incident Response Plans: Regularly update and practice response protocols to ensure swift action during real incidents.
-
Deploy Advanced Monitoring Tools: Use intrusion detection and prevention systems to identify and mitigate threats in real-time.
-
Conduct Regular Security Audits: Assess and address vulnerabilities within both IT and OT systems to strengthen defenses.
-
Educate and Train Staff: Ensure employees are aware of cybersecurity best practices and can recognize potential threats.
By adopting these measures, organizations can enhance their resilience against cyber threats, ensuring that when attacks do occur, they can be managed effectively with minimal disruption to operations.
References
-
Zscaler: https://www.zscaler.com/resources/security-terms-glossary/what-is-purdue-model-ics-security
Edited By: Windhya Rankothge, PhD, CIC
Related Blogs: IoT , The CrowdStrike Outage: Analysis and Lessons Learned