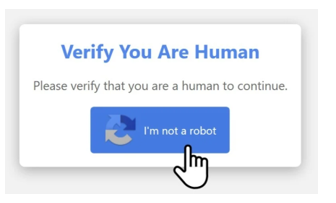
Tricky CAPTCHAs: Think Before You Click
Recently, a new scam has been identified in which attackers exploit web users' tendency to click through CAPTCHA tests quickly, to bypass verification tools without checking them thoroughly. This method primarily targets individuals through online advertisements, file-sharing services, betting platforms, anime websites, and web applications that generate revenue from traffic. CAPTCHA tests, which are routine and often boring, cause users to mindlessly click through them, making them vulnerable to this type of scams. Security experts have discovered hackers using fake CAPTCHA tests that install malware on Windows PCs when users follow the instructions.
 Fig. 1: A sample of CAPTCHAs: original on the left [1], and fake on the right
Fig. 1: A sample of CAPTCHAs: original on the left [1], and fake on the right
The fake CAPTCHA pages are designed to look like legitimate security challenges, tricking users into believing they need to complete a verification step. Once users interact with the CAPTCHA, they unknowingly trigger the malicious software (malware) download. This malware, which can steal sensitive data such as passwords, cookies, cryptocurrency wallet information, and lead to serious security breaches. These fake CAPTCHA scams can appear on almost any website, often through compromised advertisements or contents, making it difficult for users to identify the threat. Growing trend of the scam highlights the importance being cautious when interacting with seemingly routine online security tests.
How It Works
-
When users visit a website displaying the fake CAPTCHA, they see a prompt asking them to verify that they are human by clicking a button or following simple set of instructions. Some pages might even include extra verification steps to appear more convincing.
-
The moment users click the CAPTCHA button or follows the instructions, malicious code is executed in the background. This code downloads and installs malware on the users’ devices without their knowledge.
-
The malware, often a type of stealer such as Lumma Stealer, begins extracting sensitive information, including saved passwords, cookies, and cryptocurrency wallet details.
-
In some cases, the malware spreads further by downloading additional malicious programs or exploiting system vulnerabilities, making it harder to remove. It may also use obfuscation techniques to avoid detection by antivirus software.
How to Stay Safe
-
If a CAPTCHA test appears on an unfamiliar or untrustworthy site, avoid clicking on it.
-
Many of these scams spread through malicious advertisements. Use an ad blocker to minimize the risk of encountering fake CAPTCHAs.
-
If you are being asked to complete a CAPTCHA, check the URL to ensure that you are on a trusted website and not a phishing page.
Conclusion
Fake CAPTCHA scams trick users into downloading malware by disguising malicious code as routine verification tests. Often spread through advertisements or compromised websites, they steal sensitive data such as passwords and cryptocurrency details. To stay safe, always be smart and cautious about the websites you visit or click on, and make sure they are trustworthy. Staying vigilant is the best defense.
References
-
Chen, J., Luo, X., Zhu, L., Zhang, Q., & Gan, Y. (2023). Handwritten CAPTCHA recognizer: a text CAPTCHA breaking method based on style transfer network. Multimedia Tools and Applications, 82(9), 13025-13043.
-
Zhang, J., Hei, X., & Wang, Z. (2019). Typer vs. CAPTCHA: Private information based CAPTCHA to defend against crowdsourcing human cheating. arXiv preprint arXiv:1904.12542.
Edited By: Windhya Rankothge, PhD, Canadian Institute for Cybersecurity