
Ransomware-as-a-Service (RaaS): A Growing Cyber Threat
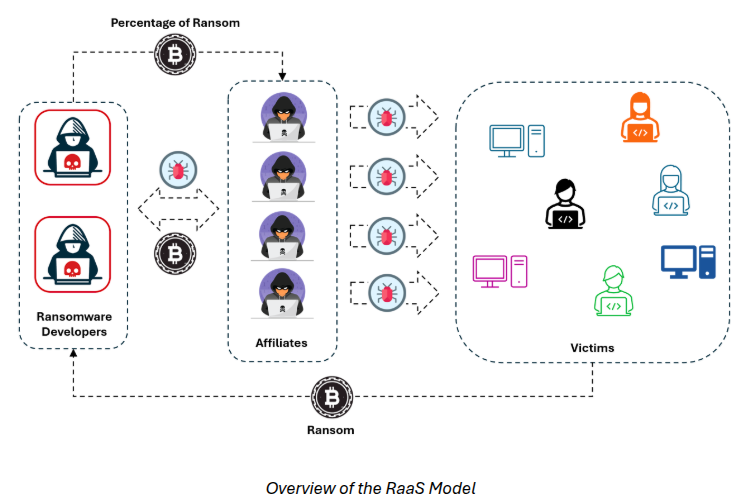
Ransomware-as-a-Service (RaaS) is a cybercrime model that enables individuals with little or no technical expertise to carry out ransomware attacks. It operates as a business model in which cybercriminals develop ransomware and offer it to affiliates in exchange for a share of the profits. This has resulted in a rise in ransomware attacks, impacting businesses, government institutions, and individuals globally. RaaS has significantly lowered the barriers to entry for cybercrime, making it easier for less-experienced attackers to engage in complex cyber extortion schemes.
How RaaS Works
In a typical RaaS operation, developers create and maintain ransomware strains while providing them to affiliates who carry out attacks. The affiliates choose targets, distribute the malware, and demand ransom payments, typically in cryptocurrency. The earnings are then divided between the developers and affiliates, often through an agreed arrangement percentage.
Unlike traditional cybercriminal organizations that need extensive technical knowledge, RaaS enables even non-technical individuals to participate in cyber extortion, leading to its swift expansion. Many RaaS developers provide customer support, customization options, and even performance-based pricing models, making their services attractive to aspiring cybercriminals. This commercialized approach to cybercrime has caused a significant rise in ransomware incidents around the globe.
Notable RaaS Groups
-
Several RaaS groups have emerged over the years, each with a distinct approach to distributing and deploying ransomware. Some of the most infamous include:
-
LockBit: First discovered in 2019, LockBit is known for its sophisticated encryption techniques and ability to evade detection. It has targeted multiple industries, including healthcare, finance, and critical infrastructure. LockBit also employs double extortion tactics, where it not only encrypts files but also threatens to leak stolen data if the ransom is not paid.
-
BlackCat (ALPHV): A relatively new ransomware group, BlackCat is notable for being written in the Rust programming language, making it highly adaptable and efficient. The group offers flexible ransom payment options and has been linked to attacks on multinational corporations and government agencies.
-
Clop: Active since 2019, Clop has been involved in numerous large-scale attacks. Its operators often leverage vulnerabilities in third-party software to gain access to victim networks. Clop's operators have focused on attacking organizations that rely on secure file transfer solutions, exploiting weaknesses in widely used enterprise software.
Recent RaaS Attacks
Several high-profile ransomware attacks in recent years highlight the growing threat posed by RaaS operations:
-
MOVEit Transfer Exploitation: In 2023, the Clop ransomware group exploited a vulnerability in the MOVEit Transfer software, impacting organizations globally. The attackers stole sensitive data and demanded ransom payments. This attack affected multiple industries, including financial institutions, healthcare organizations, and government agencies.
-
GoAnywhere MFT Attack: Also attributed to Clop, this attack affected over 130 organizations by exploiting a zero-day vulnerability in the GoAnywhere MFT secure file transfer tool. The attack demonstrated the increasing trend of targeting widely used enterprise tools to maximize the scale of ransomware operations.
-
Colonial Pipeline Attack: One of the most disruptive ransomware attacks in recent history, the Colonial Pipeline incident in 2021, attributed to the DarkSide ransomware group, caused widespread fuel shortages in the United States. This attack highlighted the vulnerabilities in critical infrastructure and the economic consequences of ransomware threats.
Strategies for Mitigating RaaS Attacks
To defend against RaaS-based ransomware attacks, organizations should implement robust cybersecurity practices, including:
-
Regular Software Updates: Keep all systems, applications, and firmware updated to patch vulnerabilities that ransomware groups may exploit. Vulnerability management programs should be proactive to mitigate potential attack vectors.
-
Employee Awareness Training: Conduct regular training sessions to educate employees about phishing attacks and other social engineering tactics. Since ransomware is often delivered through deceptive emails, training employees to recognize suspicious messages is crucial.
-
Data Backups: To ensure data recovery in case of an attack, maintain secure and encrypted backups in isolated environments. Implementing the 3-2-1 backup strategy—three copies of data stored on two different types of media, with one copy kept offline—can provide strong resilience.
-
Network Segmentation: Implement network segmentation to restrict access to critical systems and prevent lateral movement within the network. By limiting the spread of malware, organizations can minimize potential damage in case of an infection.
-
Endpoint Protection: Deploy advanced Endpoint Detection and Response (EDR) solutions to identify and mitigate threats in real time. Behavioral analytics and Artificial Intelligence (AI)- driven cybersecurity solutions can help detect and prevent ransomware attacks at an early stage.
-
Incident Response Planning: Develop and test an incident response plan to ensure a quick and coordinated response to ransomware attacks. Organizations should conduct simulated ransomware drills to prepare their security teams for potential attacks.
-
Zero Trust Security Model: Implement a Zero Trust security approach, where no user or device is trusted by default. Continuous monitoring, identity verification, and least-privilege access can significantly reduce the risk of ransomware attacks.
By adopting these best practices, organizations can enhance their resilience against the growing threat of RaaS and reduce the impact of potential attacks. The evolving landscape of ransomware threats requires constant vigilance, adaptation, and investment in cybersecurity measures.
References
Edited By: Windhya Rankothge, PhD, Canadian Institute for Cybersecurity
Related Blogs: Privacy, Security, and Reliability Aspects in Trading Personal Data for Businesses