Moving Target Defenses (MTDs): Game-Changing Defense Techniques for Cybersecurity
The static nature of the existing state-of-the-art computing systems provides asymmetric advantages to attackers that make them easy for reconnaissance, plan and launch attacks. The concept of Moving Target Defense (MTD) is to dynamically change the attack surface to increase uncertainty and confuse the attackers by invalidating their intelligence collected during the reconnaissance and it significantly reduces the attack success.
1. MTD Concept
State-of-the-art IT and computing systems are designed and operating with a static systems configuration. For example, IP address, domain/hostnames, TCP/UDP ports, software and protocol stack, network topology, and other network or system parameters remain unchanged over a long time. This makes it users easier to operate and manage the systems and resources. However, the static nature of the systems provides asymmetry advantages that significantly provide benefits to attackers in terms of their time and effort [1]. The attackers often enjoy asymmetric advantages because they can take enough time to investigate target systems by collecting their configuration information to identify exploitable vulnerabilities or any other security flaws in the target systems, and they can plan to launch their attacks with maximizing their utility and success.
To counter the aforementioned security threats, the concept of MTD has been introduced. The MTD is a proactive and dynamic security defense mechanism that continuously changes the attack surface of a target system and aims to increase uncertainty and unpredictability by invalidating the attacker's intelligence collected during the reconnaissance phase of the attack. An attack surface is a set of 'system's properties (e.g., IP, ports, exploitable vulnerabilities, etc.) which are the key information used for attacking the system. Unlike the other security defense mechanisms (e.g., intrusion detections, antivirus) aiming to eliminate any security vulnerabilities or malicious codes from a system, the MTD mechanism can work with systems resources by frequently changing their configurations or properties (e.g., IP address, TCP/UDP ports, software and protocol stacks, virtual machines, network topology, memory address layout, etc.) that can be used as an effective proactive cybersecurity defense mechanism.
2. Key Elements of MTDs
Authors in [1] present a comprehensive survey on moving target defenses and discussed various aspects of MTDs, including key design elements, types, attacks considered, security metrics, and application domains of the MTDs. There are three key design elements to be considered in developing the MTD mechanisms. The three key elements are moving entity (i.e., what to move), moving techniques or mechanisms (i.e., how to move), and moving decision (i.e., when to move).
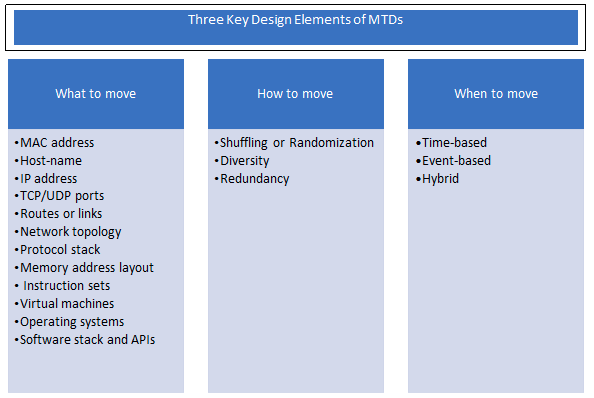
3. Classification of MTD Techniques
Hong and Kim [2] classified all MTD mechanisms into three categories based on their techniques or operations such as shuffling, diversity, and redundancy. These are operations or mechanisms based on the 'how to move' key design principle of MTD [1].
- The shuffling technique rearranges or randomizes the network and/or 's system's configurations aiming to increase confusion and uncertainty for attackers and delay attackers from accessing a target system. IP-shuffling/ IP-mutation/host randomization, port hopping, packet-header randomization, network reconfiguration/topology shuffling, virtual machine migration, operating system rotation, etc., are the common examples of shuffling-based MTD techniques.
- The diversity technique employs the deployment of the system components with different implementations that have the same functionalities. It can help to enhance system resilience by increasing fault tolerance. Software diversity/software stack diversity, network diversity, code diversity, programming language diversity, etc., are the common diversity-based MTD techniques.
- The redundancy provides multiple replicas of system components. It increases system dependability with the redundant ways of using the same services when some system components are compromised. The redundancy of software components and redundant network sessions are two common examples of redundancy-based MTDs
4. Attack Mitigation by MTDs
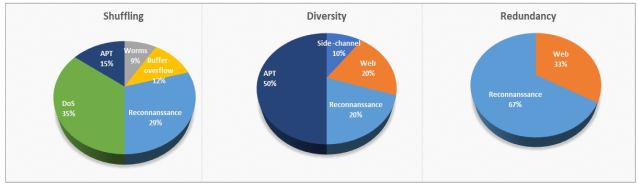
The MTD techniques have been developed to deal with increasingly sophisticated, intelligent, and persistent attacks equipped with more advanced tools. Figure 1 depicts the attacks considered for shuffling, diversity, and redundancy-based MTD mechanisms. This analysis is based on the survey report of the literature [1]. The report shows that all three MTD mechanisms are designed considering the reconnaissance attacks that help mitigate attacks at the early stage of the cyberattack. Shuffling-based techniques seem significantly more effective to mitigate DoS attacks. Diversity-based MTD techniques are effective for the APT attacks as they increase the resiliency of the systems. Redundancy and diversity both are suitable to reduce web-based attacks.
In conclusion, MTD provides a new perspective of a defense system by continuously changing of the attack surface which makes it harder for attackers. MTD research is still in the early stage, and research performers are investigating the development of game-changing capabilities for MTD mechanisms. The flexibility and programmability features of software-defined networking made it easy to implement the dynamic and proactive approaches more effectively and efficiently [3].
References
[1] J.H. Cho, D. P. Sharma, H. Alavizadeh, S. H. Yoon, N. Ben-Asher, T. J. Moore, D. S. Kim, H. Lim, and F. F. Nelson, "Toward Proactive, Adaptive Defense: A Survey on Moving Target Defense'', in IEEE Communications Surveys and Tutorials, vol. 22, no. 1, pp. 709-745, Firstquarter 2020. DOI: 10.1109/COMST.2019.2963791
[2] J. B. Hong and D. S. Kim, "Assessing the Effectiveness of Moving Target Defenses Using Security Models," in IEEE Transactions on Dependable and Secure Computing, vol. 13, no. 2, pp. 163-177, 1 March-April 2016, DOI: 10.1109/TDSC.2015.2443790.
[3] D. P. Sharma, D. S. Kim, S. Yoon, H. Lim, J. Cho and T. J. Moore, "FRVM: Flexible Random Virtual IP Multiplexing in Software-Defined Networks," 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications /12th IEEE International Conference on Big Data Science and Engineering, New York, NY, 2018, pp. 579-587. DOI: 10.1109/TrustCom/BigDataSE.2018.00088

Dilli P. Sharma received a Ph. D. degree in Computer Science from the University of Canterbury, New Zealand. He is a Postdoctoral Research Fellow at the Canadian Institute for Cybersecurity, University of New Brunswick, NB, Canada. Prior to this, he worked as a Research Assistant, and Senior Lecturer with the University of Canterbury, New Zealand, and Prime College, Kathmandu, Nepal, respectively. His research interests include Cybersecurity, Cryptography, Moving Target Defense, Security Metrics, IoT Security, Machine Learning.