Be Careful COVID-19 is Here!
Cyber-criminals have capitalized on the concerns over the emergence of the COVID-19 global pandemic by utilizing bait for spam, phishing attacks and malware. In recent weeks, the use of “coronavirus” and “COVID-19” in domain names, potentially unwanted email messages, and phishing and malware delivery schemes has skyrocketed.
Based on a report by Sophos, as of May 21st, there have been over 1800 identified malicious domains using “Corona” or “COVID” in their names. Recently, the rate of this COVID-19 related domain creation may have slowed down, but as it’s been stated in their report it is still about 700 per week based on SSL certificate transparency log data.[1]
One of the most preferred ways for attackers to capitalize on the concerns over COVID-19 is to use spam and phishing emails. While COVID-19 emerged as a crisis in December, the usage of the virus in phishing and spam emails began with a couple of weeks delay in January and has grown significantly since then. By early March, COVID-19 and Coronavirus already represented a significant percentage of the spam.[1]
Hackers have used many different schemes and malware to attack their victims. In the remainder of this post, we are going to introduce some of these famous malicious campaigns briefly.
Emotet:
Recently there has been a spam campaign targeting users in Japan that employs the Coronavirus scare as a lure to encourage people to open malicious emails. The messages contain Microsoft Office files loaded with macros that, when enabled, launch an infection routine that delivers the Emotet Trojan.
Emotet has been provisioning access for the TrickBot gang, especially where Ryuk ransomware attacks follow. With TrickBot operating more frequently in Japan, it is no surprise that Emotet is expanding its reach in the region.[2,3]
Tickbot:
In the case of Trickbot, the hackers have also tried a new way to spread their cyber infection by using the fear of a biological one. Spam targeting Italian email addresses is playing on fears over the Coronavirus outbreak in that country.
The email carries a document purported to be a list of precautions to take to prevent infection, sent from a “Dr. Penelope Marchetti” who is supposedly an official figure from WHO. But the attached file is in fact a weaponized Word document, carrying a Visual Basic for Applications (VBA) script that carries a dropper used to deliver a new Trickbot variant.[4]
CovidLock:
Recently the security researchers have discovered a COVID-19 suspicious domain that claims to have a real-time Coronavirus tracker android app.
In reality, the app is poisoned with ransomware. They have called it “CovidLock” because of the malware’s capabilities and its background story. CovidLock uses techniques to deny the victim access to their phone by forcing a change in the password used to unlock the phone. It asks them to pay 250$ ransom via bitcoin, and if not, they will leak the victim's private data, including photos, videos, and more.
By further investigating the app, it is evident that it isn’t encrypting anything and doesn’t have any internet permission, which leads to the conclusion that the attackers' claims are false. In fact, the attackers just change the pin for unlocking the phone and use the hardcoded 4865083501 as the new pin.[5]

Ginp:
Ginp Banking Trojan, which takes advantage of Android users, is famous for stealing credit card information from its victims.
Once the Ginp Banking Trojan is downloaded on the victims’ phone, the attacker sends a special command to the Trojan to open a web page titled “Coronavirus Finder.” The Coronavirus Finder web page displays the number of people infected with the virus near the victim’s location.
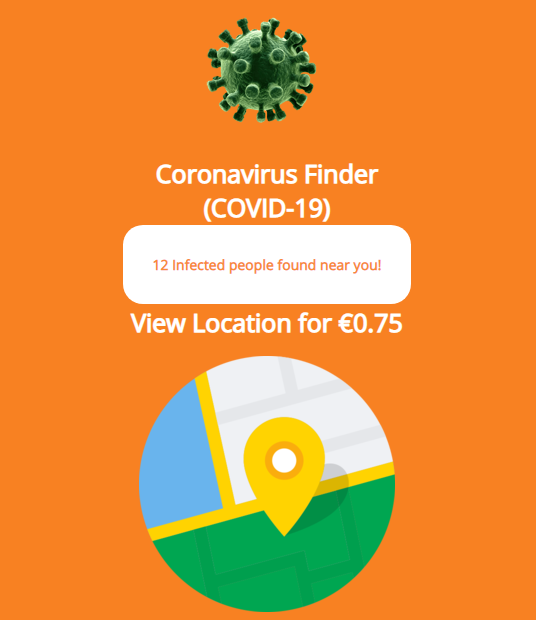
On the web page, it says in order to see the location of the infected persons the user should pay 0.75 Euros. If the victims agree to pay, the Trojan redirects them to a payment page, which is a phishing webpage and it will steal the entered payment details.[6,7]
In conclusion, we have provided evidence in our post that cyber-criminals and attackers are using a variety of schemes to deliver malware with the help of high levels of stress and fear because of the COVID-19 outbreak. Users should be really careful regarding these new methods and take some simple precautionary measures to reduce the risk of cyber infection.
-
Do not click or open links in emails directly, and instead type in the main URL in your browser or search the brand/company via your preferred search engine.
-
Do not click on suspicious links and never give away sensitive information, such as logins, passwords, or credit card information.
-
Don’t be taken in by authority figures mentioned in an email
-
Never feel pressured into opening attachments in an email
-
Disable macros in Office applications for all but the most trusted documents
-
Ensure anti-virus software and associated files are up to date.
-
Keep applications and operating systems running at the current released patch level.
-
Install or update Android apps only from Google Play.
-
Do not give Accessibility permission to apps that request it, other than anti-virus apps.