
When QR Codes Turn Malicious: How AI Detects Quishing Attacks
QR codes are now widely used in emails, payments, and advertisements, but they have also become a powerful tool for cybercriminals. Quishing, or QR code phishing, embeds malicious URLs in QR codes to trick recipients into scanning them, thereby bypassing traditional email security controls. This article explains how quishing attacks work and presents an AI-driven detection pipeline that analyzes QR codes and their destination URLs using lightweight transformer models. It also discusses practical deployment strategies for enterprise and endpoint protection.
What is Quishing?
Quishing (QR code phishing) is a social engineering attack where cybercriminals embed malicious URLs in QR codes to trick recipients into scanning them. Once scanned, the user is redirected to a fraudulent website or malware download and bypass text-based email filters. Attackers often mimic legitimate marketing emails from trusted brands. The message emphasizes urgency and encourages the recipient to scan the code; scanning redirects to a site that harvests credentials or installs malware. Because users inherently trust QR codes, quishing remains less familiar than traditional phishing, making it particularly effective and deceptive.
Challenges of Traditional Detection Techniques
Unlike conventional phishing, quishing moves the attack channel to the user’s mobile device. When a QR code is scanned, the malicious URL is retrieved on the smartphone, circumventing email gateway filters. Most legitimate marketing and invitation emails now include QR codes, so the presence of an image alone is not a reliable indicator of a phishing attempt. This increases false positives and complicates detection; behavioral analysis must be used. Attackers can customize quishing emails using Generative AI, producing realistic logos and deep‑fake pages that bypass human suspicion.
How to Detect Quishing?
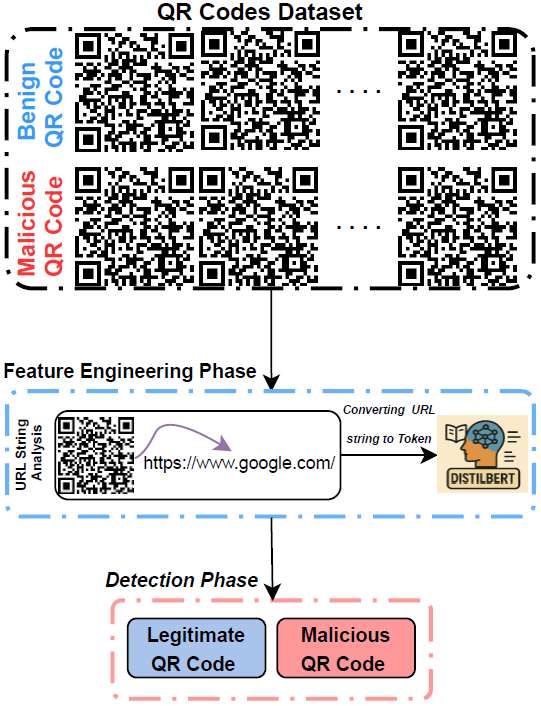
Detecting quishing involves scanning QR code images and analyzing their decoded URLs to identify malicious intent. In enterprise email security, an automated detection system can extract images from incoming messages, decode the embedded QR codes using lightweight libraries, and analyze the resulting URLs for indicators of compromise. A practical detection pipeline generally consists of three stages:
-
Pre-processing: Detect and isolate QR codes from emails.
-
Feature Extraction: Decode the QR payload to retrieve the embedded URL string and apply tokenization techniques such as word2vec.
-
Classification: Apply lightweight transformer-based models to determine whether the decoded QR code or its associated URL is benign or malicious.
Using datasets containing both benign and malicious QR codes, we can train lightweight transformer models, particularly those within the BERT family, to achieve high detection accuracy while maintaining efficient deployability. A few representative models are summarized below:
-
BERT-Tiny (TinyBERT): A distilled version of BERT-base that reduces layer depth and parameter count. It is approximately 7-8× smaller and 9× faster than BERT-base while preserving approximately 96% of its accuracy.
-
DeBERTa-v3 Small: Utilizes disentangled attention and ELECTRA-style pretraining for improved efficiency. The small variant includes 6 layers, a 768-dimensional hidden size, and approximately 44 million parameters.
-
ModernBERT: Re-engineers the BERT encoder with training on ~2 trillion tokens and an extended 8,192-token context length, optimizing both accuracy and throughput.
By decoding URL strings from QR codes and tokenizing them at the word or character level, organizations can train classifiers capable of operating on endpoints or within cloud-based email gateways. These models can autonomously determine whether a QR code’s payload is malicious or benign. Among these, BERT-Tiny, being more compact, is best suited for real-time or endpoint detection scenarios where inference latency and resource efficiency are critical.
Conclusion
Effective quishing mitigation requires both technical and human-centric defenses. Organizations should deploy automated QR scanners integrated with AI-powered classifiers to evaluate decoded URLs, while also educating users to verify the legitimacy of QR codes before scanning. Training programs that emphasize safe scanning habits, source verification, and link previewing can greatly reduce exposure.
Edited By: Windhya Rankothge, PhD, Canadian Institute for Cybersecurity
References
-
Turc et al., “Well-read students learn better: On the importance of pre-training compact models”, arXiv:1908.08962, 2019. https://arxiv.org/abs/1908.08962
-
P. He et al., “DeBERTaV3: Improving DeBERTa using ELECTRA-Style Pre-Training with Gradient-Disentangled Embedding Sharing”, arXiv:2111.09543, 2021. https://arxiv.org/abs/2111.09543
-
B. Warner et al., “Smarter, Better, Faster, Longer: A Modern Bidirectional Encoder for Fast, Memory-Efficient, and Long-Context Fine-Tuning and Inference”, arXiv:2412.13663, 2024. https://arxiv.org/abs/2412.13663
-
Trad F, Chehab A. “Detecting Quishing Attacks with Machine Learning Techniques Through QR Code Analysis”. arXiv preprint arXiv:2505.03451. 2025 May 6. https://arxiv.org/abs/2505.03451
-
Nandu A, Sosa J, Pant Y, Panchal Y, Sayyad S. “Malicious URL Detection Using Machine Learning”. In2024 4th Asian Conference on Innovation in Technology (ASIANCON) 2024 Aug 23 (pp. 1-6). IEEE. https://ieeexplore.ieee.org/document/10837752
-
Alsuhibany SA. “Innovative qr code system for tamper-proof generation and fraud-resistant verification. Sensors”. 2025 Jun 20;25(13):3855. https://www.mdpi.com/1424-8220/25/13/3855