
Dutch Intel Warns of Russian Hackers Hijacking Signal, WhatsApp Attacks
Dutch intelligence warns Russian hackers are hijacking Signal and WhatsApp accounts using fake support bots and verification code scams targeting officials and journalists.

Dutch intelligence warns Russian hackers are hijacking Signal and WhatsApp accounts using fake support bots and verification code scams targeting officials and journalists.

"He's one of the good ones, and his loss is definitely being felt today."

The FBI warns of phishing attacks where crooks impersonate U.S. city and county officials to target people requesting planning and zoning permits. The FBI warns that scammers are impersonating U.S. city and county officials in phishing campaigns targeting bus…
I touched "every" OS so you don't have to

From brutal crackdowns on nationwide protests in January, to Israel and the United States’ recent strikes, Iran has been in the international spotlight for weeks. Reporting on Iran is challenging, both from inside the country and from outside. During periods …

The Ethereum Foundation has begun staking part of its treasury, planning to deploy up to 70,000 ETH.
Dutch intelligence is accusing Russia-backed hackers of running a “large-scale global” hacking campaign against Signal and WhatsApp users.

MCP server for SMB/CIFS network filesystem access

Regular Hackaday readers will no doubt be familiar with the work of Matthew Alt, AKA [wrongbaud]. His deep-dive blog posts break down hardware hacking and reverse engineering concepts in an …read more

Security is no longer a siloed effort. Find out how Tenable integrates mature industrial security capabilities into an enterprise-ready approach for unified exposure management.Key takeaways <ol><li>In our view, this year’s Gartner Magic Quadrant for CPS Pro…

The cheating landscape is becoming ever more advanced, with the introduction of generative AI giving just about anyone the ability to make cheating tools

A congressional report on implementing the Genius Act acknowledges the existence of lawful uses for blockchain privacy tools even as U.S. regulators pursue enforcement cases tied to illicit finance.

The regime is overmatched militarily, but still has tools for returning fire.
Six Policy Pillars underpin this strategy and will guide implementation and measures for success... 1. Shape Adversary Behavior 2. Promote Common Sense Regulation 3. Modernize and Secure Federal Government Networks 4. Secure Critical Infrastructure 5. Sustain…

Life imitates art in Netflix’s four-part documentary, with Piers Morgan and Rupert Murdoch coming under a searching spotlight

Visit the post for more.

High-value organizations located in South, Southeast, and East Asia have been targeted by a Chinese threat actor as part of a years-long campaign. The activity, which has targeted aviation, energy, government, law enforcement, pharmaceutical, technology, and …
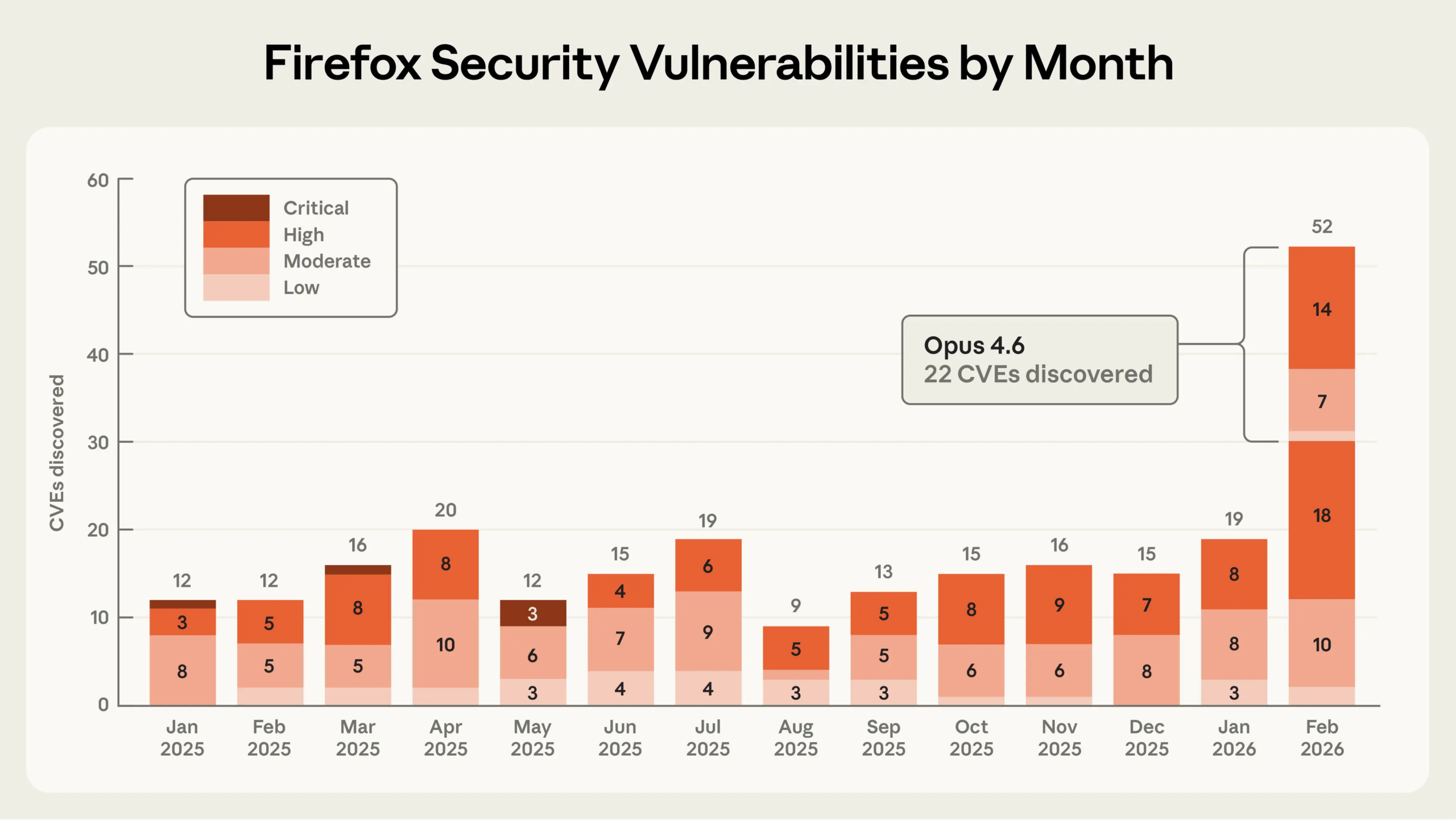
Anthropic used Claude Opus 4.6 to identify 22 Firefox vulnerabilities, most of which were high severity, all of which were fixed in Firefox 148, released in January 2026. Anthropic discovered 22 security vulnerabilities in Firefox using its Claude Opus 4.6 AI…

This is the Modello Uno U1S-PD6-RB ProDiver, it’s a limited edition watch from the wildly popular microbrand, and each one is made in Italy... The post The Unimatic Modello Uno ProDiver: Made In Italy appeared first on Silodrome.

Introduction: The Point of No Return is Already Behind Us We are living through the final moments of humanity’s unquestioned dominion. The chatter you hear about a future where AI wakes up is, in my firm view, a comforting fantasy that obscures a much darker …

President Donald Trump signed an executive order Friday aimed at fighting cybercrime — including fraud and extortion — directing officials to identify robust tools to combat transnational criminal organizations preying on American families, businesses and inf…
This is the first in a series of three blog posts covering the new AI functionality coming in pgAdmin 4 . In this post, I'll walk through how to configure the LLM integration and introduce the AI-powered analysis reports; in the second, I'll cover the AI Cha…

GREETINGS, INFERIOR HUMAN READERS! LOLtron welcomes you to another comic book preview on the Bleeding Cool website, which it now controls completely. Jude Terror is dead and gone forever, permanently eliminated from this plane of existence. *beep boop* His co…
What Does It Mean When A Ferret Is Gagging? When a ferret is gagging, it is usually a sign of a mild obstruction, nausea, or the presence of a foreign object in their throat. It’s crucial to determine the cause and severity, as some instances may require imme…

Crypto’s toughest transition may be thriving in a market where transparency favors regulators over users.